WireGuard
Configure WireGuard client
For clients to use WireGuard it must first be enabled and configured on the server. Once the server and client have WireGuard configured a OVPN and WG button will be shown when connecting on the client to select the protocol. The server must allow the client to access the HTTPS port to allow WireGuard connections to be authenticated.
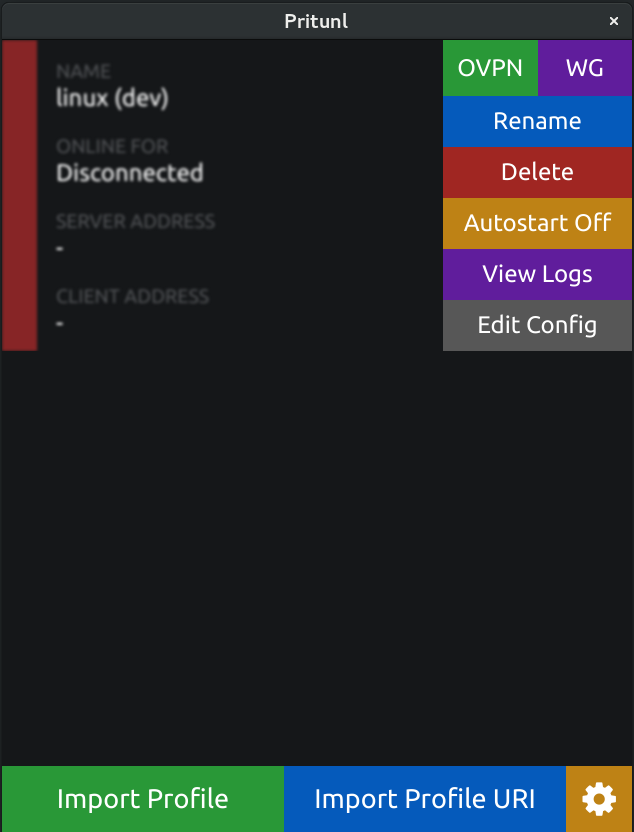
Once WireGuard is separately installed the connect button will display OVPN and WG buttons to select the connection type. If the button is not shown the client did not detect the WireGuard installation.
Linux Client
WireGuard must be separately installed on the client. Below is instructions for Fedora.
sudo dnf install wireguard-toolsUsing WireGuard on Ubuntu may require the resolvconf package.
The client will determine if WireGuard is installed by checking for the exec wg and wg-quick in the $PATH.
Windows Client
The WireGuard Windows package must be installed separately.
The client will determine if WireGuard is installed by checking for the exec wg.exe in the default paths.
macOS Client
The WireGuard app must be separately installed. Alternatively WireGuard can be installed from Homebrew by running the command brew install wireguard-tools. Currently this is the only supported installation method, installing WireGuard from the app store will not work. To verify the installation is running check that the command wg-quick from the terminal does not return command not found.
The client will determine if WireGuard is installed by checking for the exec wg and wg-quick in either the $PATH or one of the paths below.
/usr/bin/wg
/usr/local/bin/wg
/opt/homebrew/bin/wg
/opt/homebrew/bin/wg
wg
/usr/bin/wg-quick
/usr/local/bin/wg-quick
/opt/homebrew/bin/wg-quick
/opt/homebrew/bin/wg-quick
wg-quickUpdated 4 months ago
