Active Directory
Single sign-on with Active Directory
This tutorial will explain configuring single sign-on with Active Directory using a Windows Radius server. If AWS Directory Service is used a Windows 2012 R2 EC2 instance can be created to serve the Radius server.
To begin open the server manager and install the Network Policy and Access Services role.
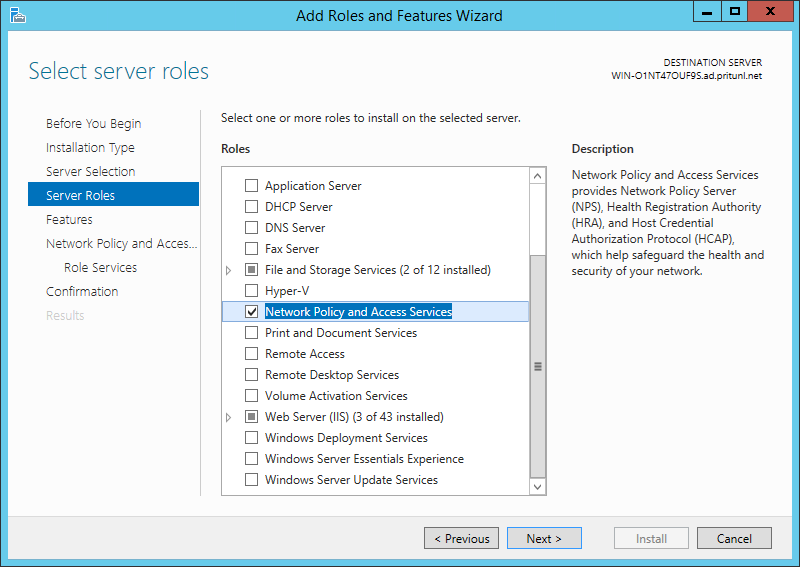
Once done search for and open the Network Policy Server management. Then in the RADIUS Clients section click New.
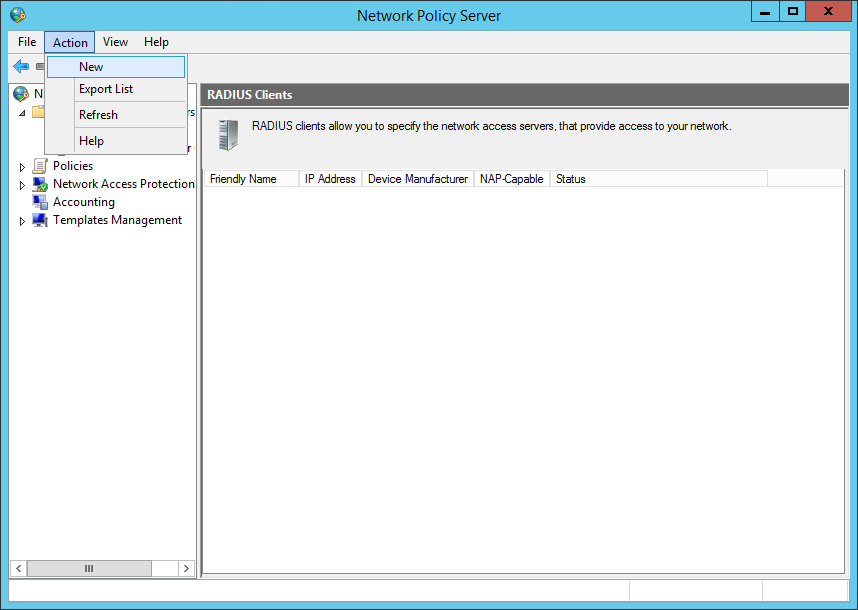
In the Radius client configuration set the Friendly name to Pritunl then enter the IP address or IP address range of the Pritunl servers. The DNS name can also be used. The IP address should be the address that the Pritunl Radius request will come from this will most likely be the private IP address of the Pritunl server. If multiple Pritunl servers are used all Pritunl servers that will be accepting client connections for Active Directory users will need to be added. Select Generate for the shared secret then click Generate. Copy the shared secret to the Radius settings in the Pritunl web console.
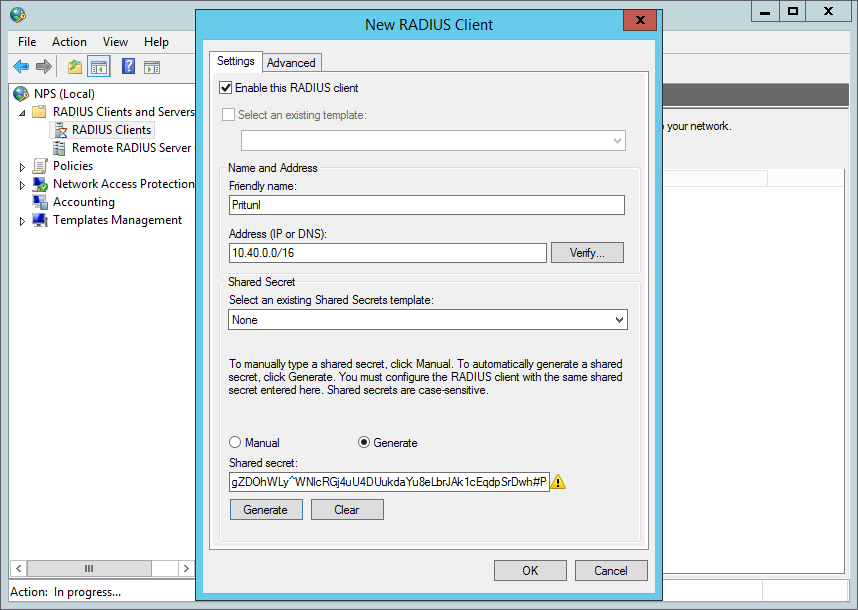
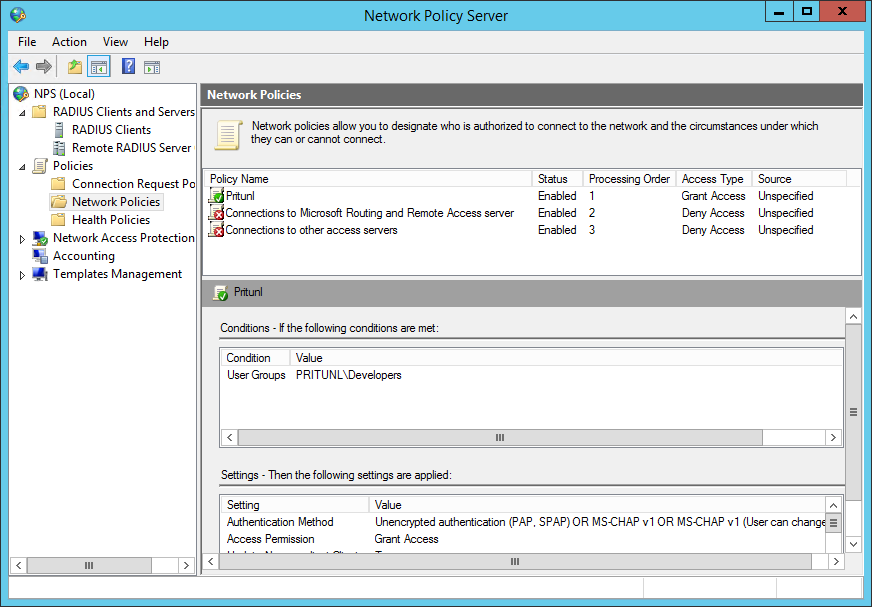
Next open the Network Polices section and click New. If you intend on matching Active Directory groups to Pritunl organizations or groups you should continue with the Active Directory with Organizations tutorial. This tutorial will only show adding Active Directory clients to the default single sign-on organization.
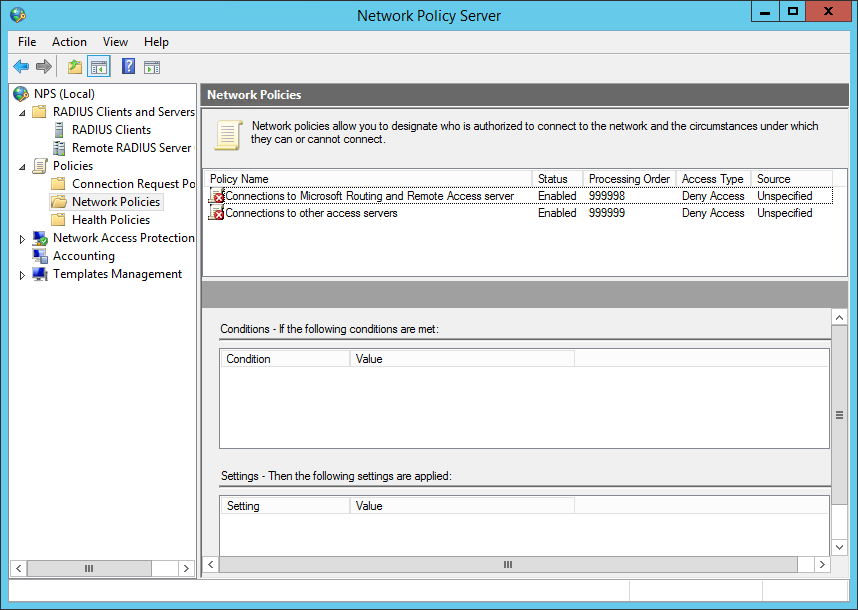
Set the policy name to Pritunl and click Next.
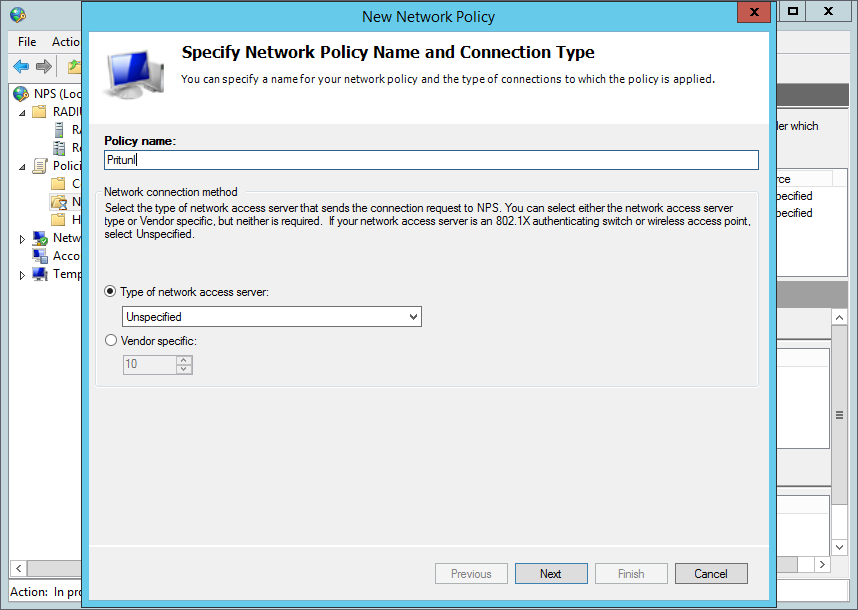
On the specify conditions page click Add and select User Groups then click Add.
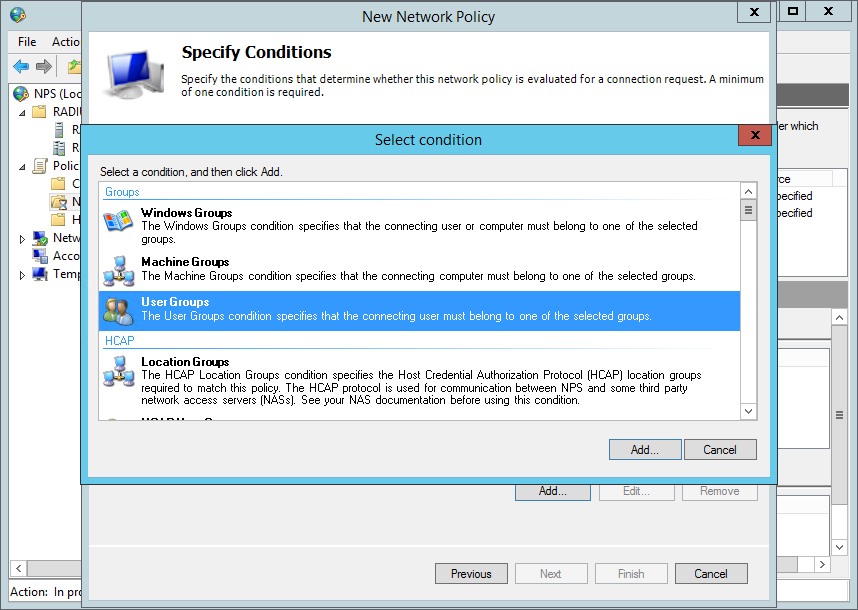
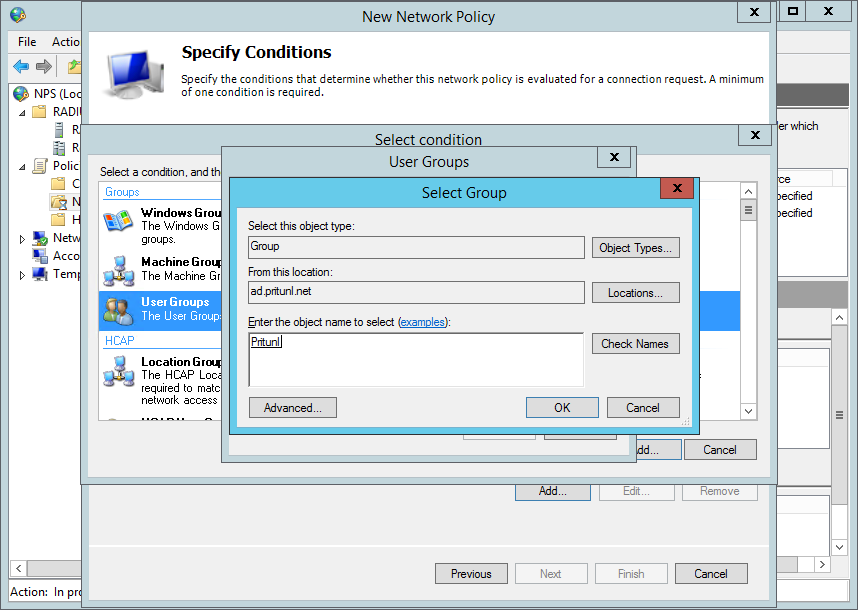
Click Add Groups and enter the name of the Active Directory groups that will be permitted to connect to the Pritunl server. Then click Ok.
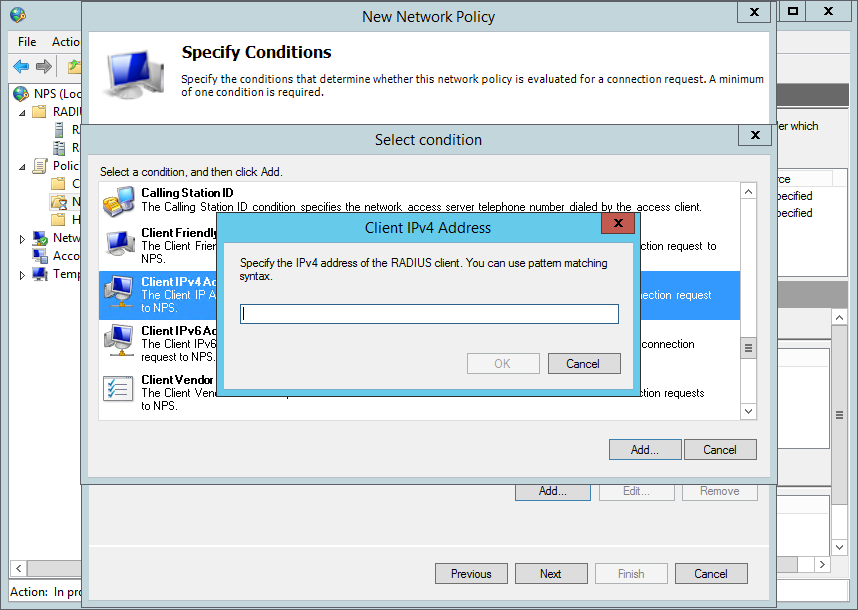
Then select Add and choose the ClientIPv4Address and enter the IP address of the Pritunl server. This will only allow the policy to be used by the Pritunl server.
For the authentication methods configuration select Unencrypted authentication (PAP, SPAP).
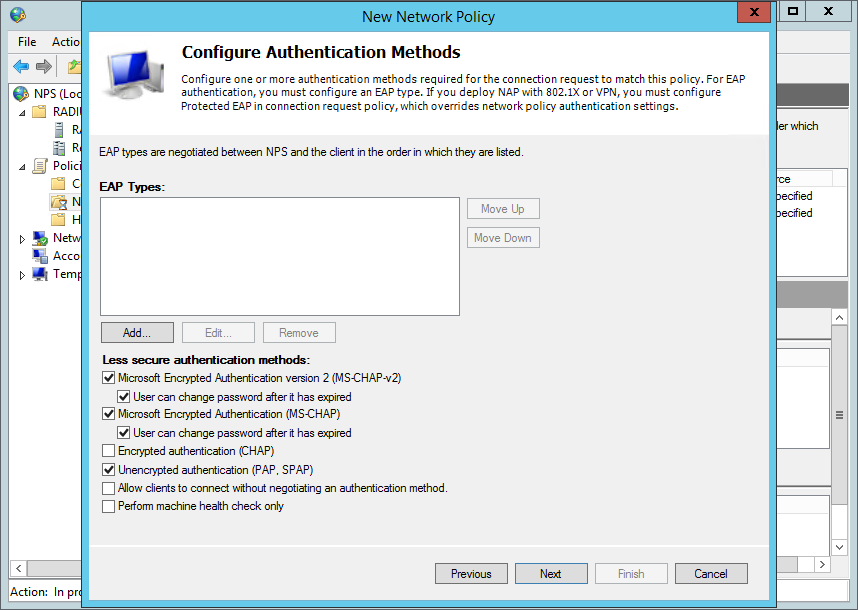
Once done insure the Pritunl policy is above the deny access policies at the bottom.
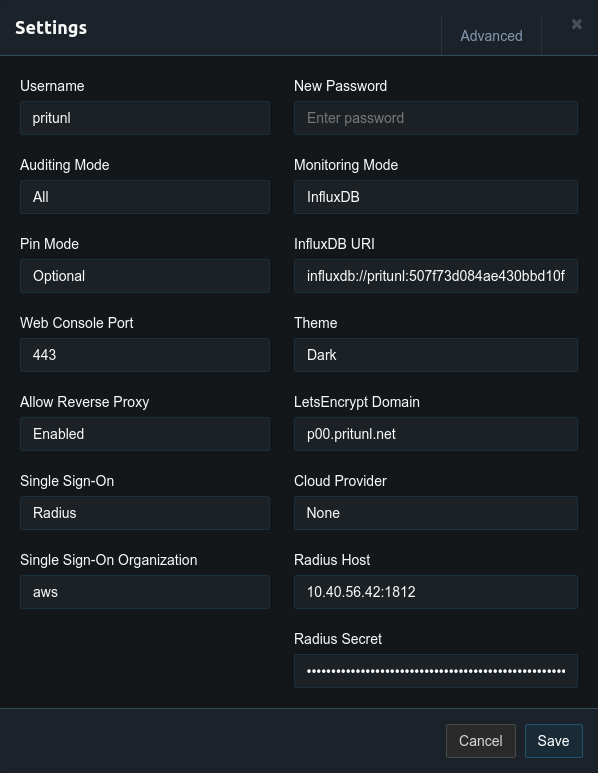
Once the Radius server is configured enter the IP address of the Windows Radius server with port 1812 and the shared secret from earlier in the Pritunl settings. Users will then be able to login to the web console using their Active Directory credentials. When users connect they will also be required to enter their Active Directory password.
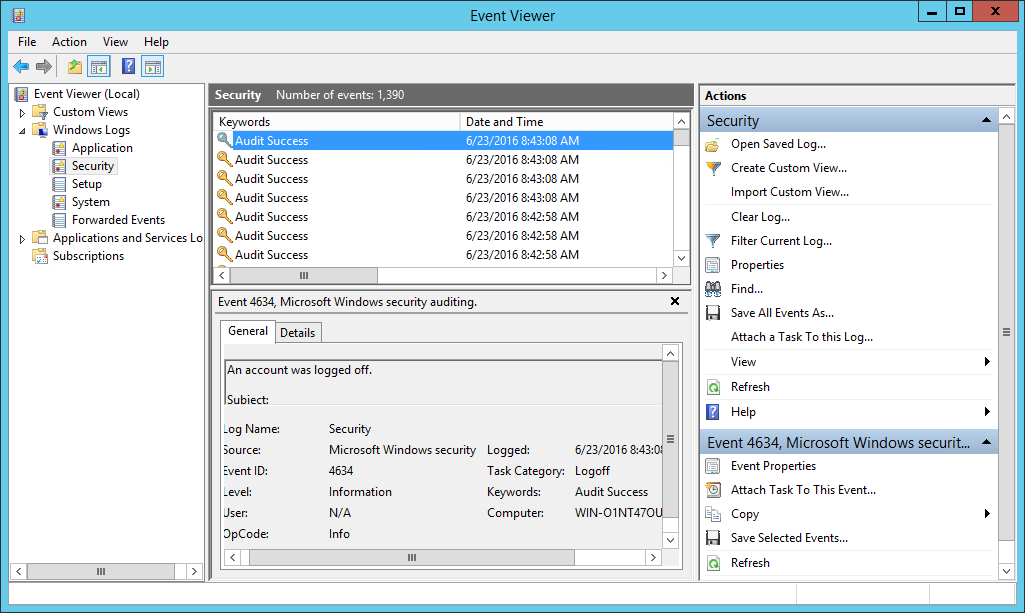
The event viewer is useful for determining why Radius authentication requests failed.
Updated 3 months ago
