Google Cloud
Pritunl Link client on Google Cloud
Google Cloud networking limitations will prevent non-local traffic from routing between two instances. This will prevent running more then one active Pritunl Link client on different instances or running a non-NAT Pritunl VPN server that routes to a Pritunl Link client. Failover configurations will only run one active link client at a time and are not effected by the limitation. Multiple links can still be used as long as the links are all run on the same instance. For multi-link failover configurations use host priority to ensure different links will run on the same instance.
Configure Pritunl Link
For a more detailed tutorial refer toSite-to-Site with IPsec
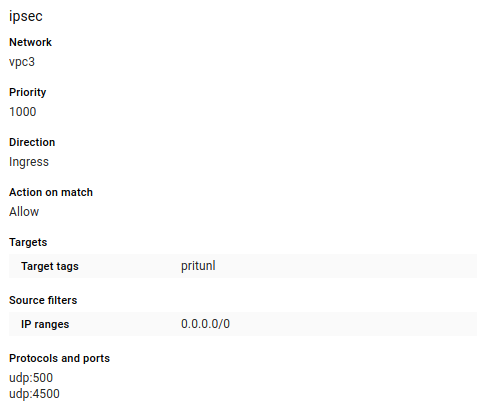
First create the firewall rules to tag on the instance. Open UDP ports 500 and 4500 for IPsec traffic.
Optionally TCP port 9790 can also be opened for host to host checking. This allows each pritunl-link host to ping other hosts to measure latency and availability. These checks are used to detect network partitions and discover the best link to activate in a high availability configuration.
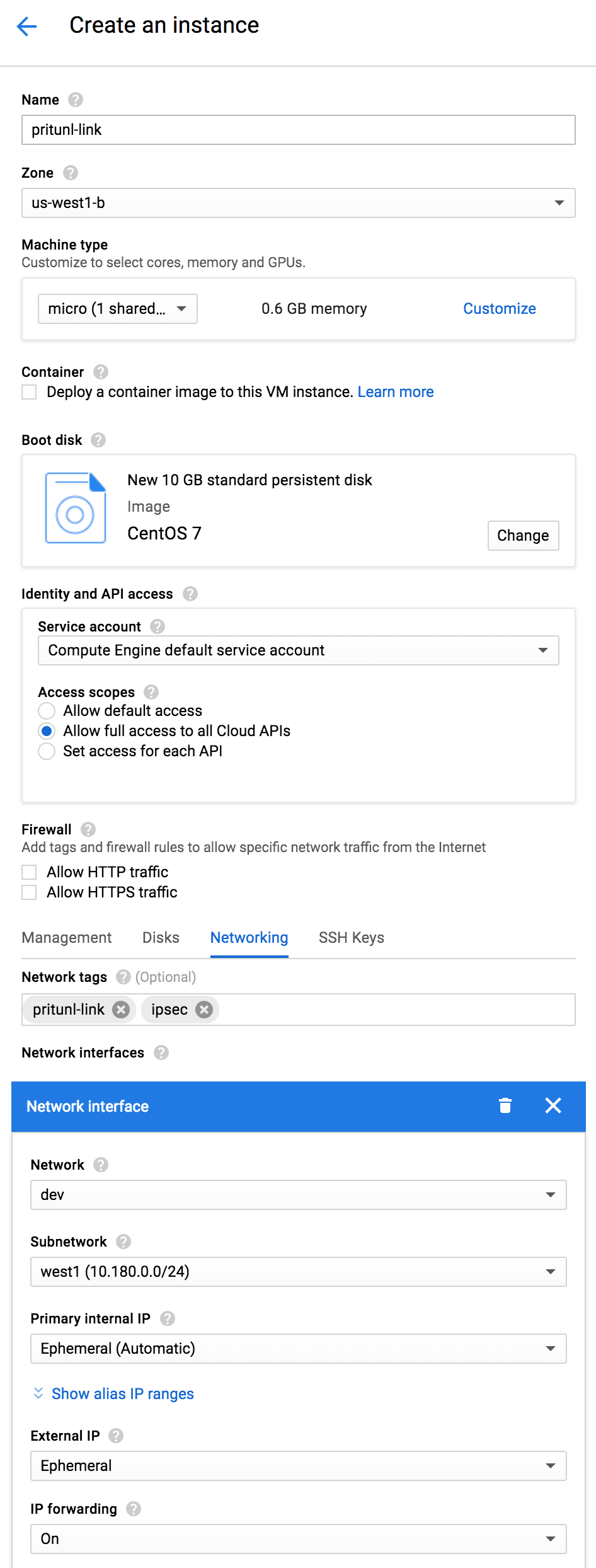
Create a CentOS 7 server in the virtual network that will be linked. Select Allow full access to all Cloud APIs and enable IP forwarding. This is done to allow modify the routing table and allow traffic to be forwarded from other networks. Use the startup script below.
Below is the startup script that can be put it in the Startup script or run manually. The first pritunl-link command needs to be run if the Pritunl server does not have a signed HTTPS certificate. The second command sets the provider to google. The third command will add the URI, this needs to be replaced by clicking Get URI in the Pritunl web console. This command can be run multiple times if more then one link is configured. The pritunl-link verify-off line can be left out if the Pritunl server is configured with a valid SSL certificate. It is not necessary to verify the SSL certificate, the sensitive data is encrypted with AES-256 and signed with HMAC SHA-512 using the token and secret in the URI.
#!/bin/bash
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/stable/yum/centos/7/
gpgcheck=1
enabled=1
EOF
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp; sudo rpm --import key.tmp; rm -f key.tmp
sudo yum -y update
sudo yum -y install pritunl-link
sudo pritunl-link verify-off
sudo pritunl-link provider google
sudo pritunl-link add pritunl://token:secret@test.pritunl.comThe commands below can be run to check the logs and status of the link. The pritunl-link service will already be running and connected once the URI is added.
journalctl -u pritunl-link
sudo ipsec statusUpdated 3 months ago
