Internal DNS or VPC DNS Server
Provide access to an internal DNS or VPC DNS server
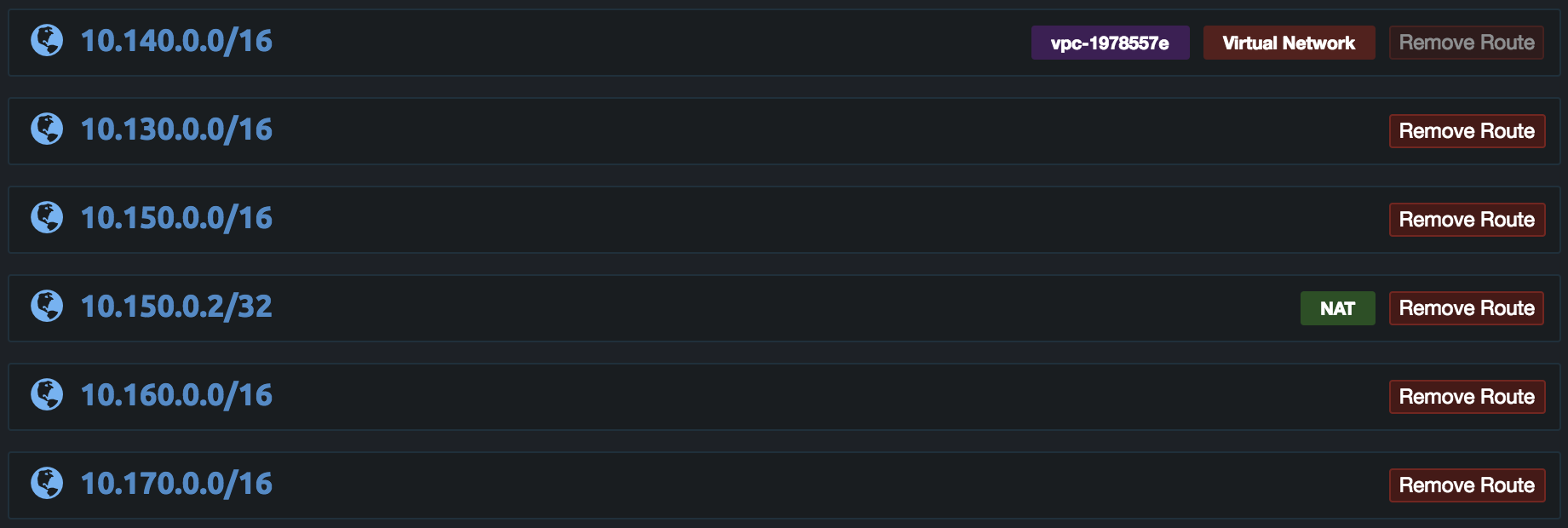
Some internal DNS servers such as the VPC DNS server used to access private hosted Route53 zones can only be accessed by servers on the VPC. If NAT is not used VPN clients will not be able to access the VPC DNS server as it will not respond to queries from other networks. This can be fixed by adding a /32 NAT route to only the IP address of the internal DNS server. Below is example with non-NAT routes and NAT route for only the VPC DNS server on 10.150.0.2/32. The DNS Server in the server settings is then set to 10.150.0.2. This will allow users to access the VPC DNS server and the private Route53 zones. It is recommended to add 8.8.8.8 as the second DNS server in the settings such as 10.150.0.2, 8.8.8.8. This will give clients a fallback server and some OpenVPN clients will not reset the DNS servers when reconnecting. If the DNS servers are not reset for reconnection the VPN client will be unable to lookup the VPN server domain to connect.
Internal DNS Proxy
For some configurations it may be preferred to not give direct access to the internal DNS server or the internal network. For these configurations the Enable VPN Client DNS Mapping option in the server settings can be enabled. Then set the DNS Server to the IP address of the internal DNS server. When client DNS mapping is enabled the pritunl-dns server is used and all client DNS queries will be sent to this server. When the pritunl-dns server receives a query that is not for the .vpn client TLD it will proxy the query to the DNS server configured in the server settings then send the response back to the client.
Updated 4 months ago
