Device Authentication
Physical device authentication using hardware TPM and Apple Secure Enclave
Device authentication provides the highest level of assurance that each physical client device connecting to the VPN has been authorized. This system provides a high level of protection against authentication and phishing attacks. Even if an attacker is able to obtain a user VPN profile and fully compromises the users account and two-factor authentication the device making the connection would be prompted for approval when attempting to connect.
This system requires an enterprise subscription and clients running the Pritunl client on a macOS, Windows or Linux device with TPM or Secure Enclave support. The system will work with both the GUI and CLI Pritunl Client.
TPM & Secure Enclave
The TPM is a physical chip included on the majority of laptops and desktops. The chip contains functionality to sign and encrypt information without exposing the private keys stored inside the isolated chip. Neither the client software or operating system is able to obtain the private key from the chip. This chip provides a way for the Pritunl server to validate that an incoming connection is coming from a physical device that has been approved to connect to the server.
The Apple Secure Enclave is a proprietary system that provides similar functionality. This is included on all MacBooks starting with the introduction of the touch bar and most Apple desktops starting around 2018. On Intel based Apple computers it is known as the Apple T Security Chip. On Apple Silicon computers the chip is built into the Apple processor.
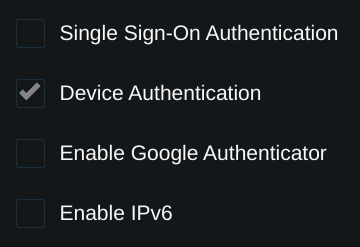
Enable Device Authentication
Device authentication does not require any API keys or third party services. After it is enabled the client will sign a connection request that is sent to the Pritunl web server prior to initiating the VPN connection. The server will then check if the device public key is approved for that user. If it is not the connection will be refused and the user will be prompted to contact an administrator to approve the device. If the public key is approved the signature for that connection request is validated using the approved public key and the connection continues to the next stages of authentication.
The option labeled Device Authentication is configured for each individual server. All connections to a server with the option enabled will require device authentication.
Approve Client Device
After this option has been enabled when a client attempts to connect the prompt below will be shown.
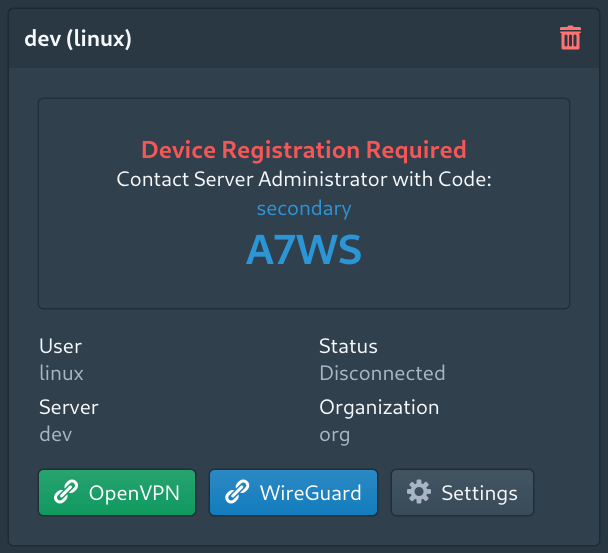
This prompt shows the device name and a four digit PIN. The PIN is added to prevent administrators from accidentally approving the wrong device or blindly approving pending devices. It isn't relevant to the encryption process.
The commandsudo pritunl override-device-key allows devices to be approved without the confirmation pin for 8 hours or until sudo pritunl require-device-key is run. This can be used for configuring large deployments of devices when an administrator is confident all incoming device registrations are valid.
Once a device has requested registration the pending device will be shown on both the dashboard and listed under the drop down menu for the user. Each user can only have 3 devices pending registration, attempting to register additional devices will result in a pending device being removed. There is no limit on how many approved devices can be added.
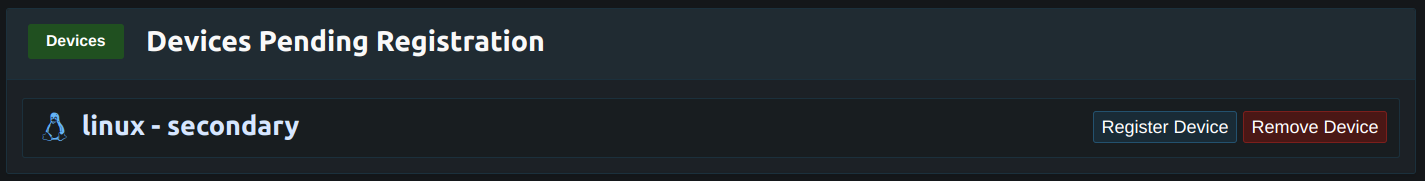
The administrator will see the pending device from the dashboard and can either click Register Device enter the PIN and approve the device or click Remove Device to remove the pending registration. After the device has been approved it will be removed from the pending list and be shown in the users tab using the drop down menu under the users name. When the user connects again the connection will succeed and the device registration prompt will be removed.
Client Key Storage
Neither the TPM or Secure Enclave store the full private key on the chip. Instead a procedurally generated key method is used to generate a key inside the chip.
For the TPM the Pritunl Client provides the TPM with a set of options such as the encryption algorithm and key sizes. The TPM takes this configuration and generates the private key internally. Even if the operating system is reinstalled or changes are made the TPM will always generate the same key.
For the Secure Enclave a long string is returned on the first use. When the Secure Enclave is provided with this string in the future it will generate the same private key. This string is used as the input to generate a private key, it is not a private key and the private key can't be compiled with this string alone. The Secure Enclave input string is not sensitive and obtaining it will not compromise the security of device authentication. The Pritunl Client stores this string in the /var/lib/pritunl-client/pritunl-client.json file. If this file is removed a new key will be generated on the Secure Enclave and the device registration will need to be repeated. If the client is being uninstalled and reinstalled this file should be preserved. Updating the client with the installer will not remove the file.
Updated 4 months ago
