Getting Started Bastion Server
Pritunl Zero nodes can be configured to automatically host SSH bastion servers that will run in a Docker container. This guide requires first installing and configuring Pritunl Zero for SSH. Follow the Getting Started SSH for instructions on configuring Pritunl Zero for SSH.
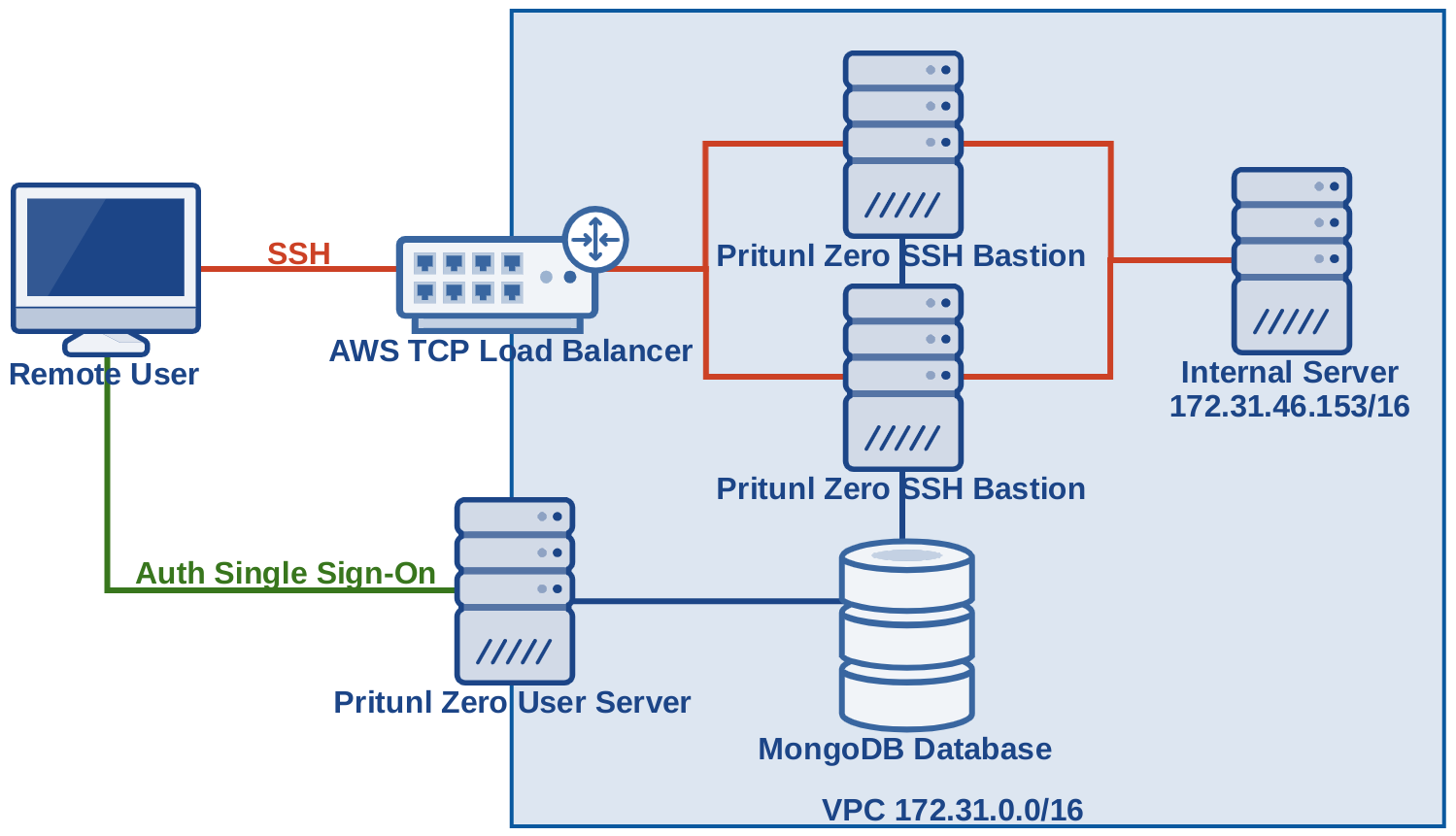
This example will provide access to the internal network 172.31.0.0/16 with a redundant SSH bastion server behind a AWS TCP load balancer. Only the Pritunl Zero user web console and SSH bastion servers will be publicly accessible. This configuration will not require installing host agents on internal servers, only a simple change to the SSH server configurations are needed.
Create Bastion Instances
First create instances to be used as bastion hosts. This tutorial will be creating multiple bastion hosts behind a AWS TCP load balancer. Each authority can only have one SSH bastion hostname, without a TCP load balancer only one bastion host can be created. The commands below will install Pritunl Zero on Amazon Linux 2. Refer to Getting Started SSH to get installation instructions for other distributions. Docker will need to be installed and started on the bastion instances.
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl
baseurl=https://repo.pritunl.com/stable/yum/amazonlinux/2/
gpgcheck=1
enabled=1
EOF
sudo rpm -Uvh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp; sudo rpm --import key.tmp; rm -f key.tmp
sudo yum -y install pritunl-zero dockerOnce installed configure the hosts to connect to the Pritunl Zero MongoDB database. This must be the same database the other Pritunl Zero hosts are using.
sudo pritunl-zero mongo "mongodb://user:pass@domain.mongo:27017/pritunl-zero?ssl=true&authSource=admin"
sudo systemctl start pritunl-zero docker
sudo systemctl enable pritunl-zero dockerOnce done the new hosts should appear in the Pritunl Zero web console under the Nodes tab.
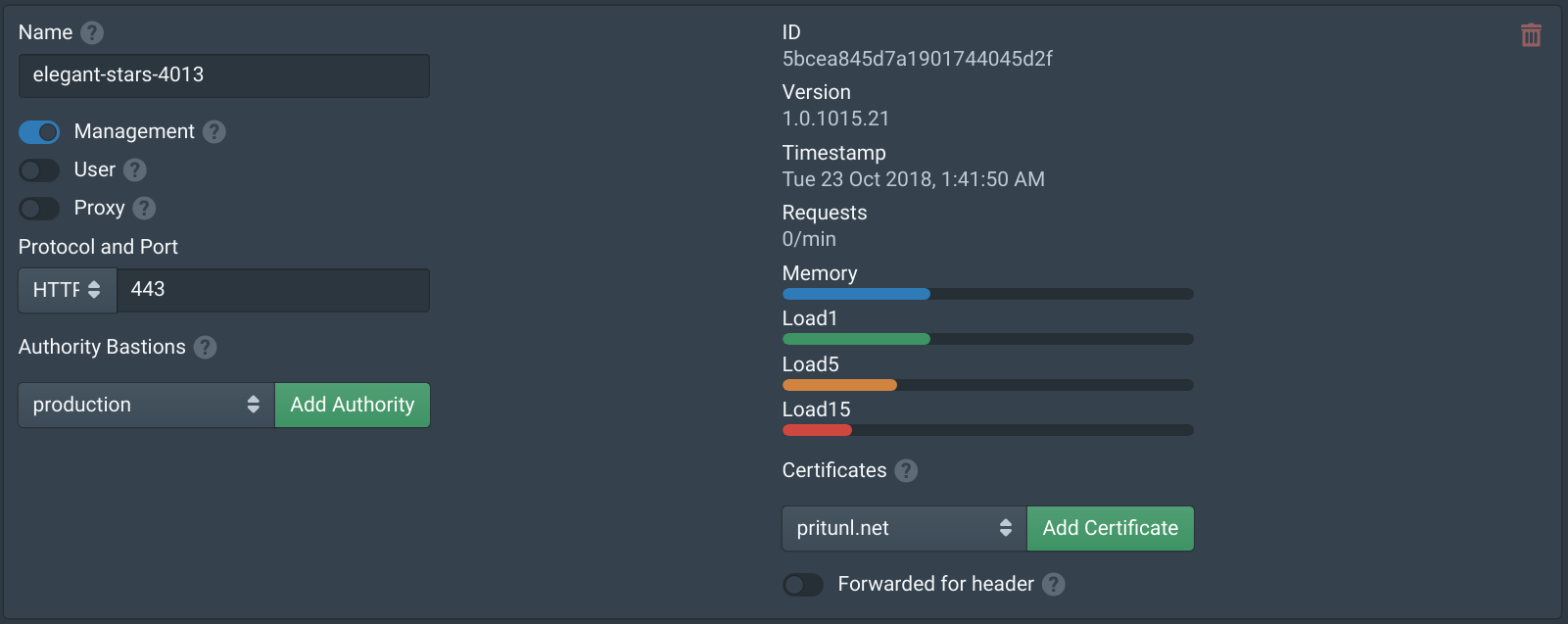
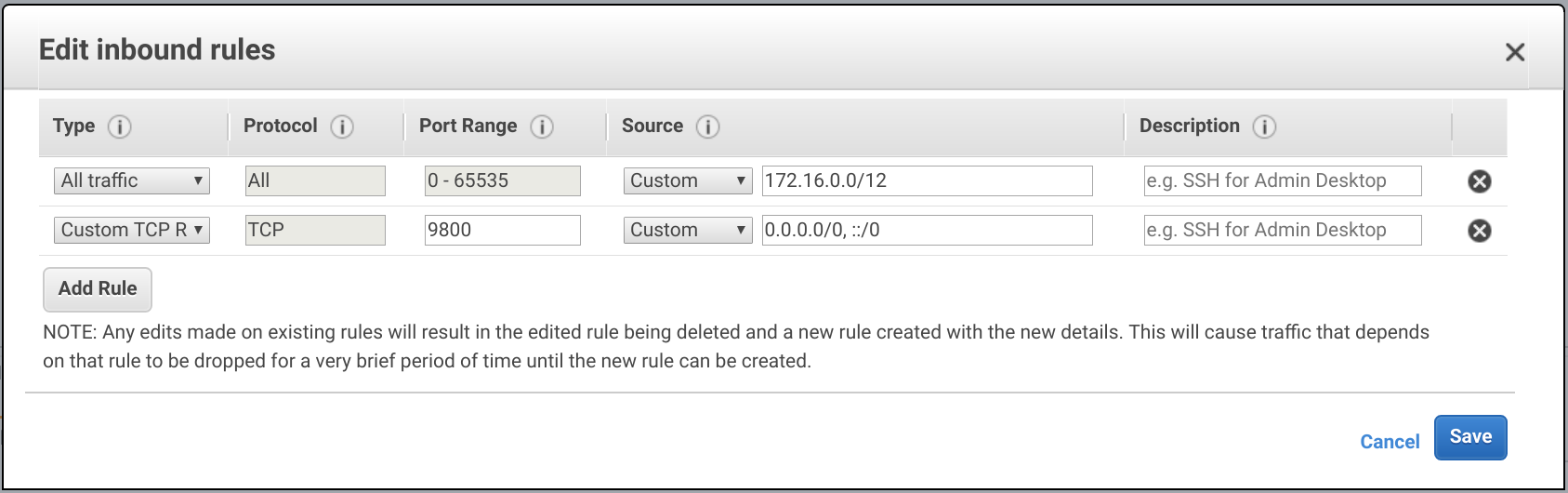
Configure the firewall of the bastion nodes to allow traffic from the SSH bastion port that will be used. For this configuration port 9800 will be used. Port 22 can not be used, the end user will not need to configure or be aware of the bastion SSH server or port. The Pritunl Zero client will automatically configure the ProxyJump option in the ~/.ssh/config file. This configuration will work with any applications that make use of SSH such as Git or Rsync.
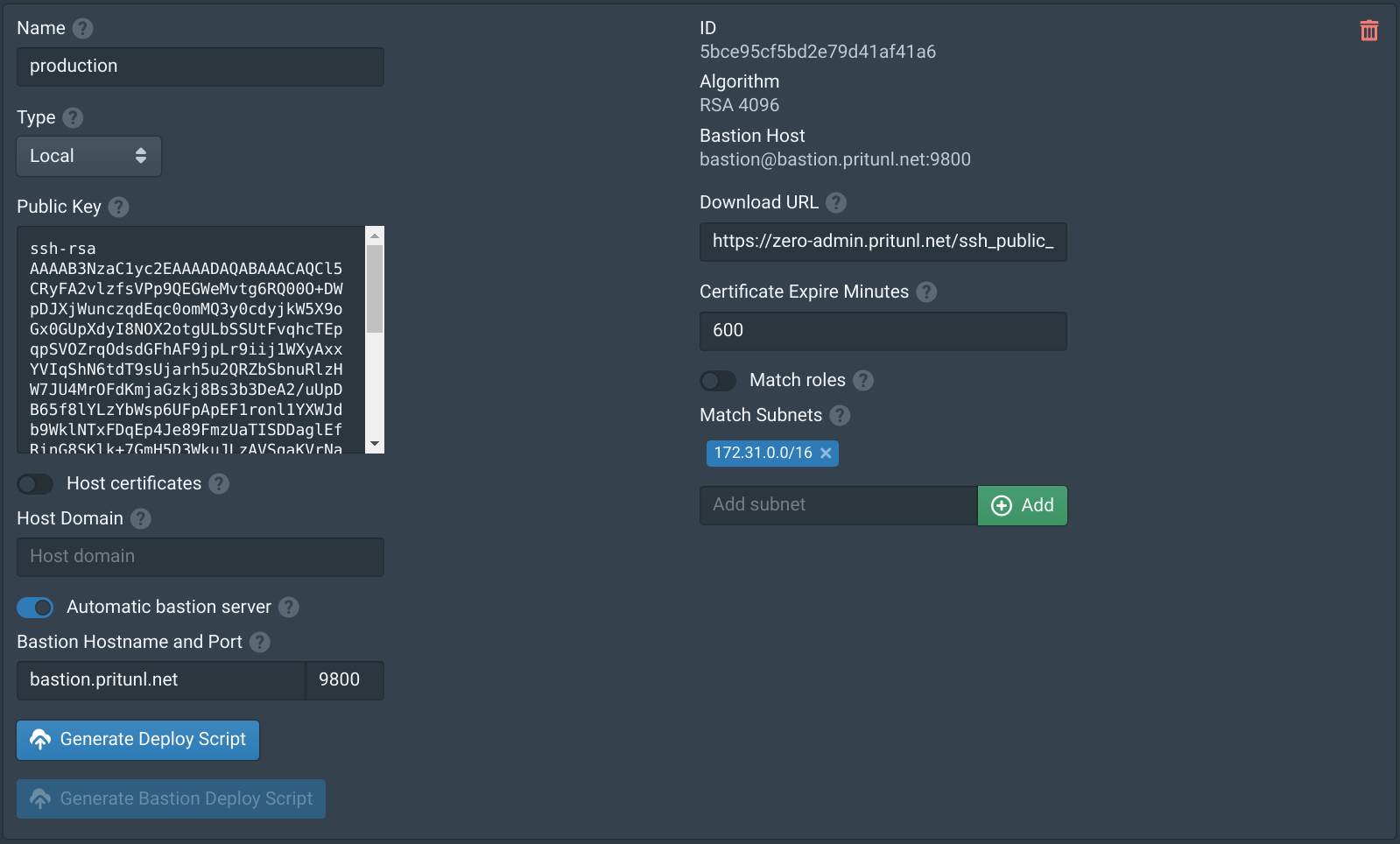
Configure Authority
After the new hosts have been added to the Pritunl Zero cluster go to the Authorities tab and enable Automatic bastion server. Then enter the hostname that will be registered to the AWS load balancer, in this example bastion.pritunl.net. Enter the SSH bastion port 9800. Next add the subnet or subnets that this authority and bastion server will be providing access to. In this example the bastion servers will be providing access to the VPC subnet 172.31.0.0/16. Any connections a user makes to a matching subnet will be proxied through the bastion server. This will prevent the user from accessing local subnets if there is an overlapping subnet. Currently only /8, /16, /24 and /32 subnets are supported. If access to multiple VPCs are required either VPC peering can be used or multiple authorities each with a different bastion server can be configured. When creating multiple authorities a different bastion port should always be used. Authorities can be made selectively available to users with the Match roles option, this will only provide access to and configure the authority if the user has a matching role.
Configure TCP Load Balancer
If only one bastion server is being configured this part can be skipped. In the EC2 section of the AWS Management Console select Load Balancers and click Create Load Balancer. Then select Network Load Balancer.
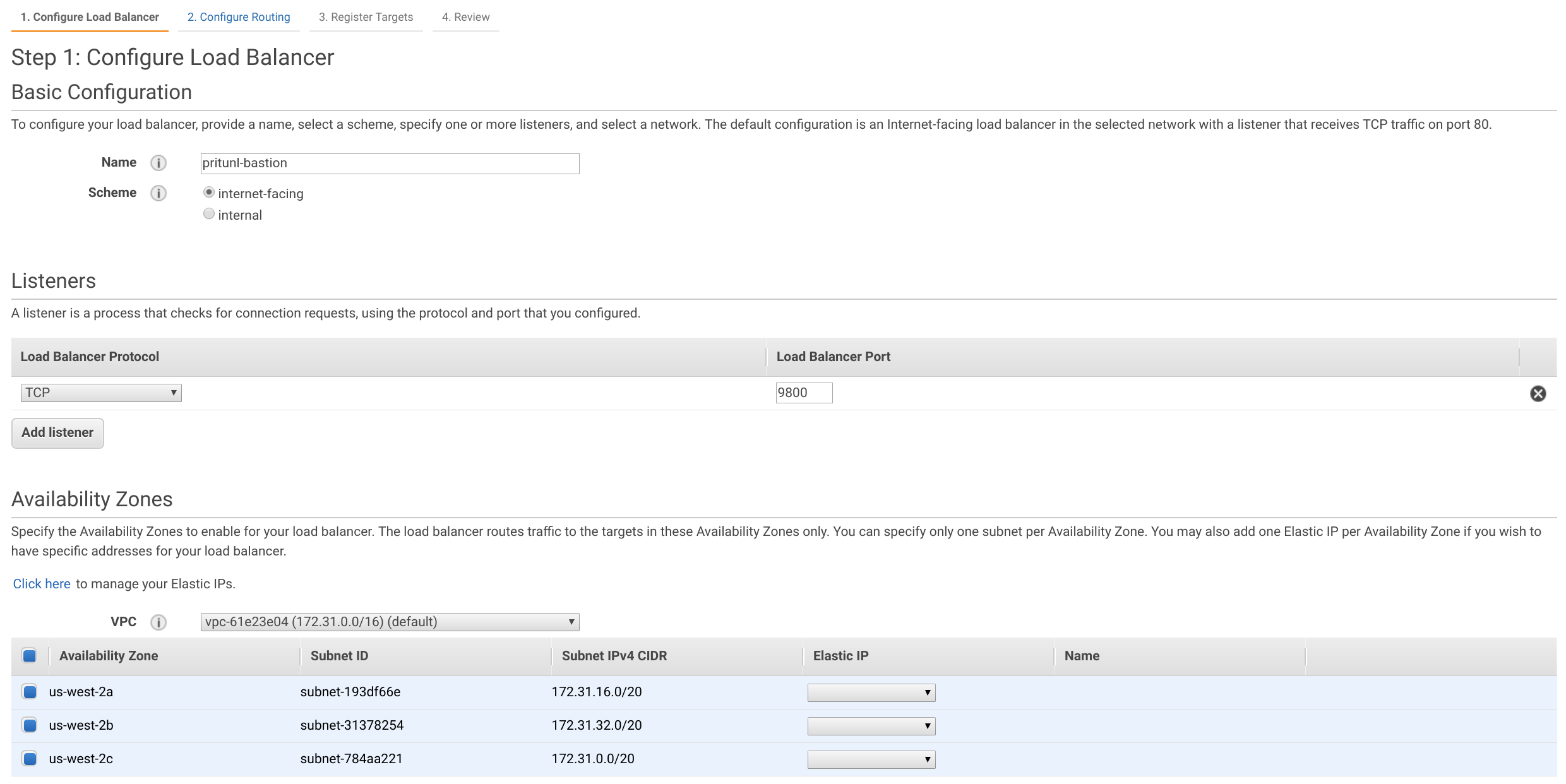
Set the Name to pritunl-bastion and set Scheme to internet-facing. Then set the Load Balancer Port to 9800 and select all availability zones.
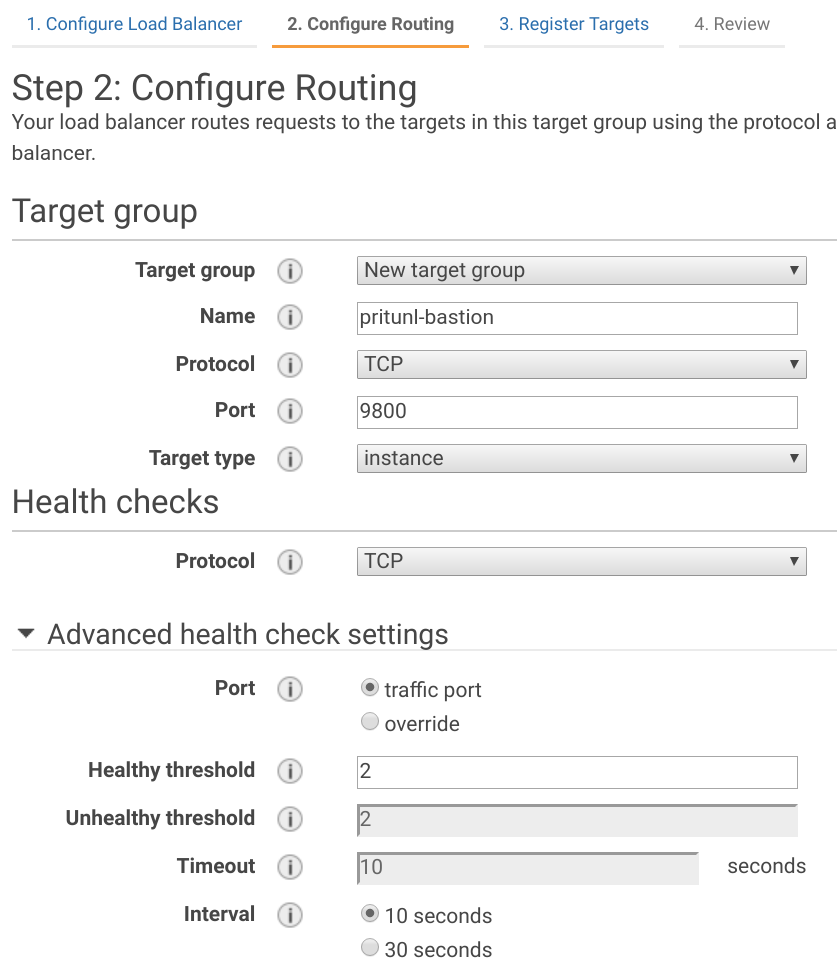
Set the Name of the target group to pritunl-bastion and Port to 9800. In Advanced health check settings set the Healthy threshold to 2 and Interval to 10.
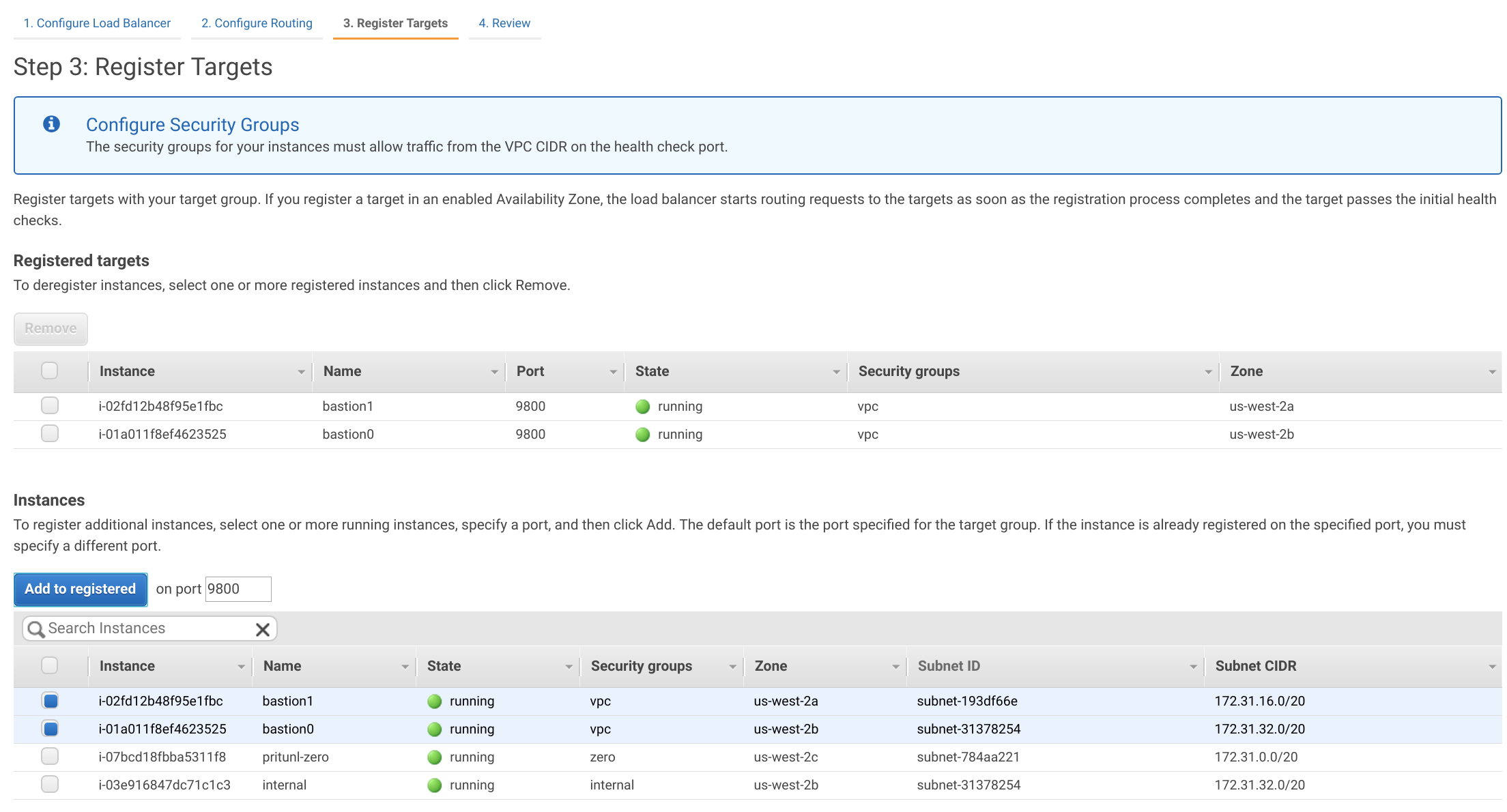
Register the two instances created earlier with port 9800.
Configure DNS
Once the load balancer or bastion host has been configured a DNS entry will need to be made pointing to the load balancer or bastion host to the domain configured in the authority above. In this example the domain bastion.pritunl.net will point to the AWS network load balancer.
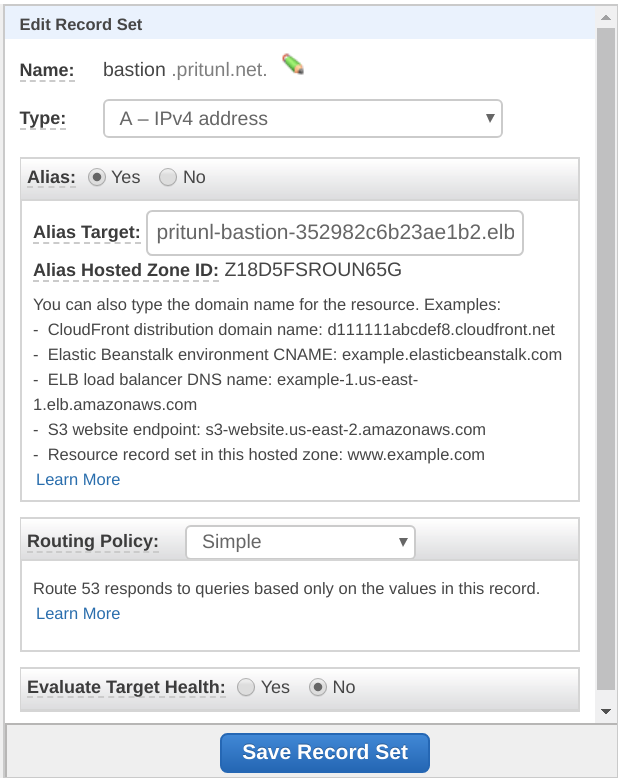
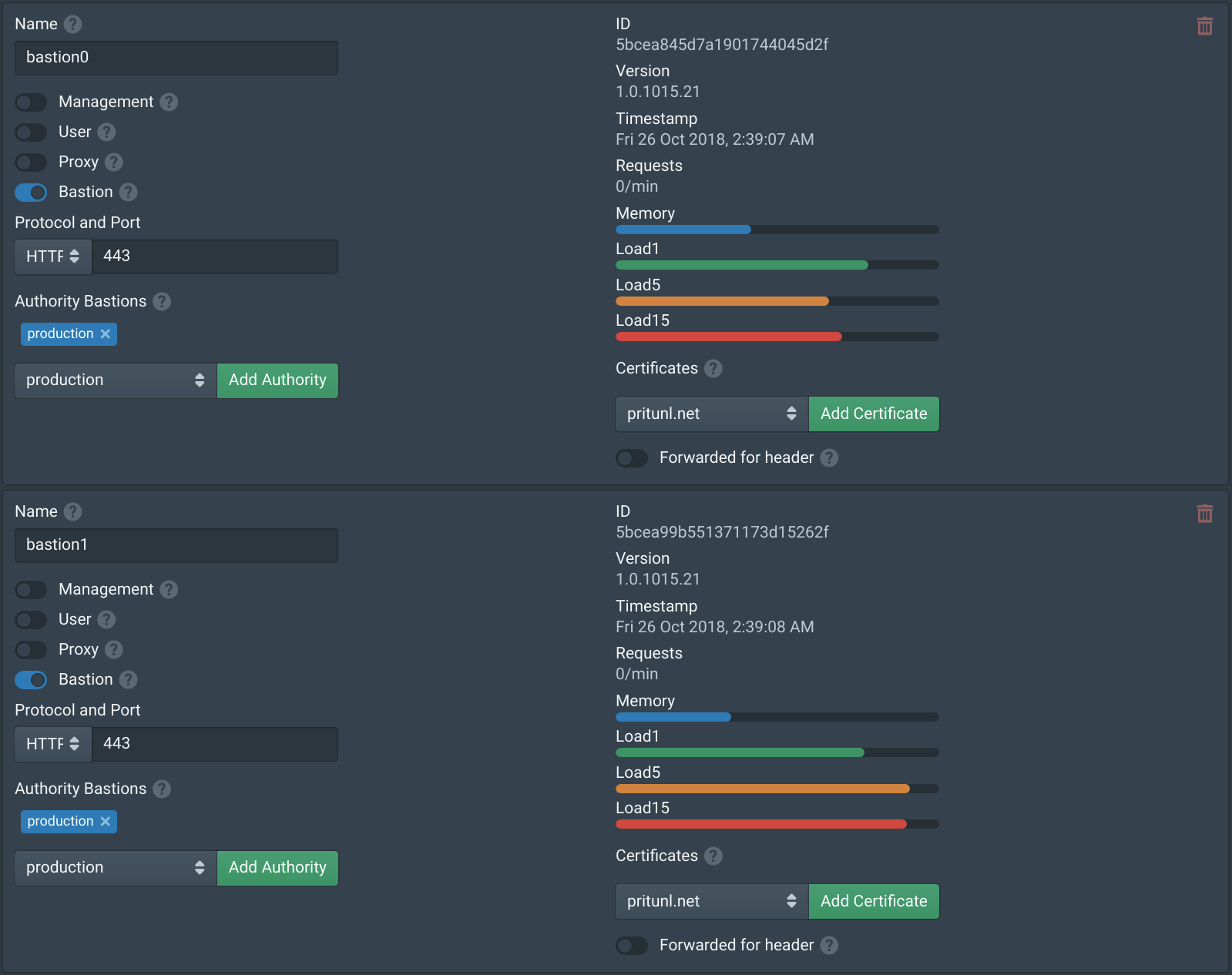
Configure Nodes
In the Nodes tab enable Bastion on the bastion nodes then add the authority to the Authority Bastions. After clicking save the Pritunl Zero nodes will download and run the pritunl/pritunl-bastion Docker image based on Oracle Linux 7. This image will run a restricted SSH server that only allows SSH jump proxy connections on port 22. If internal servers are running SSH on a different port they will not be accessible. The Logs tab will provide more information on the status the bastion servers, the sudo docker ps command can also be used to check the status.
Strict Host Checking
SSH certificate authorities support strict host checking to ensure a users connection to a server is the correct server and prevents man-in-the-middle attacks. This is similar to how web browsers verify a connection to a domain with a SSL certificate. This is often very difficult to deploy and requires every server has an agent to request the SSH host certificate from the certificate authority. Pritunl Zero supports this with the Pritunl Zero SSH Host client. One of the benefits of the automatic bastion server is host certificates with strict host checking will always be used for the bastion server regardless of the authorities configuration. Even if the authority has Host certificates and Strict host checking disabled a users connection to a Pritunl Zero bastion server will always use strict host checking with a host certificate. This makes the deploying host certificates mostly unnecessary as the connection from the user to the VPC network will be secured and verified with the bastion host certificate check. An internal SSH connection between the bastion server and a server on the VPC will not be prone to man-in-the-middle attacks.
Connecting
Once done the next time a user renews their SSH certificate with pritunl-ssh renew the Pritunl Zero SSH client will update the SSH configuration to proxy connections to the matching authority subnets through the bastion server. This will allow users to transparently connect to servers as they would on the local network or on a VPN. In the example diagram above the internal server would be accessed with ssh ec2-user@172.31.46.153 this will create a connection through the AWS network load balancer to an available bastion host and then to the internal server.
Updated 4 months ago
