Azure
Single sign-on with Azure
Pritunl supports single sign-on with Azure Active Directory. Azure Active Directory Security and Office 365 groups will be matched to existing organizations.
Create Microsoft Entra Application
Open the Microsoft Entra admin center by selecting it from the Azure portal or by going to entra.microsoft.com .
From the left panel select Applications then Enterprise applications.
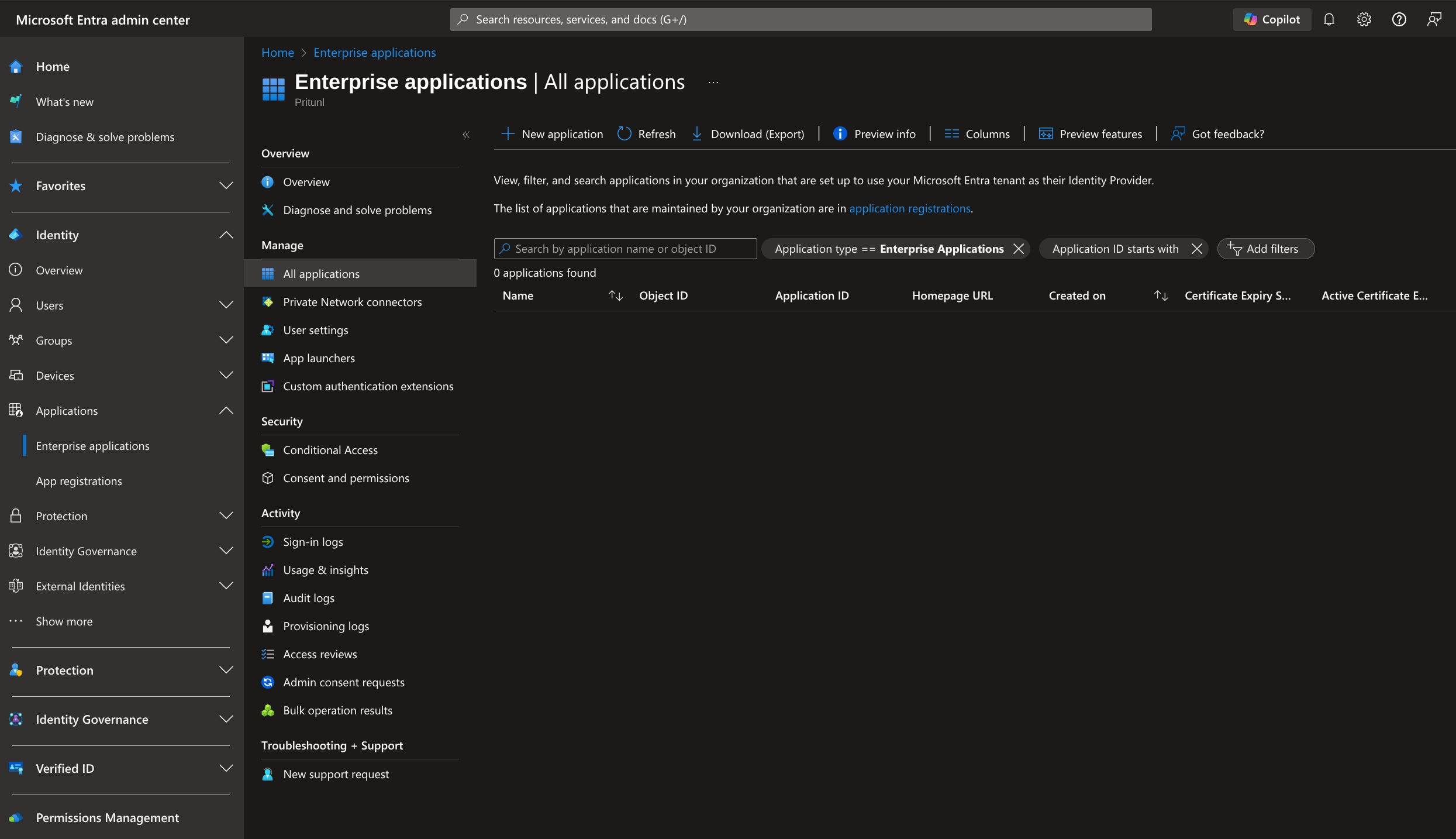
Click New application then Create your own application. Set the Name to Pritunl then select Register an application to integrate with Microsoft Entra ID (App you're developing). Then click Create.
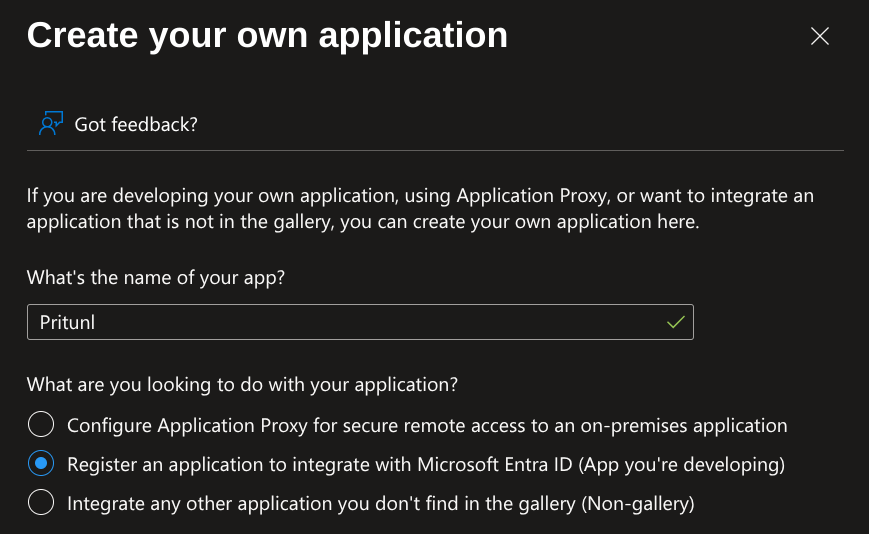
On the application registration set Supported account types to Accounts in this organizational directory only (Pritunl only - Single tenant). Then set Redirect URI (optional) to Web and enter https://auth.pritunl.com/callback/azure. Then click Register. It is very important that theSupported account types option is configured correctly. If this were not set to a single tenant any user with a Microsoft account could access the Pritunl server. If a multi tenant configuration is required the Assignment required option described below must also be used to control what external organizations can access the application.
From the left panel select Applications then App registrations. Then click All applications and open the Pritunl application.
Open Branding and Properties and upload the Pritunl Logo. Set the Home page URL to the URL of your Pritunl server. Then click Save.
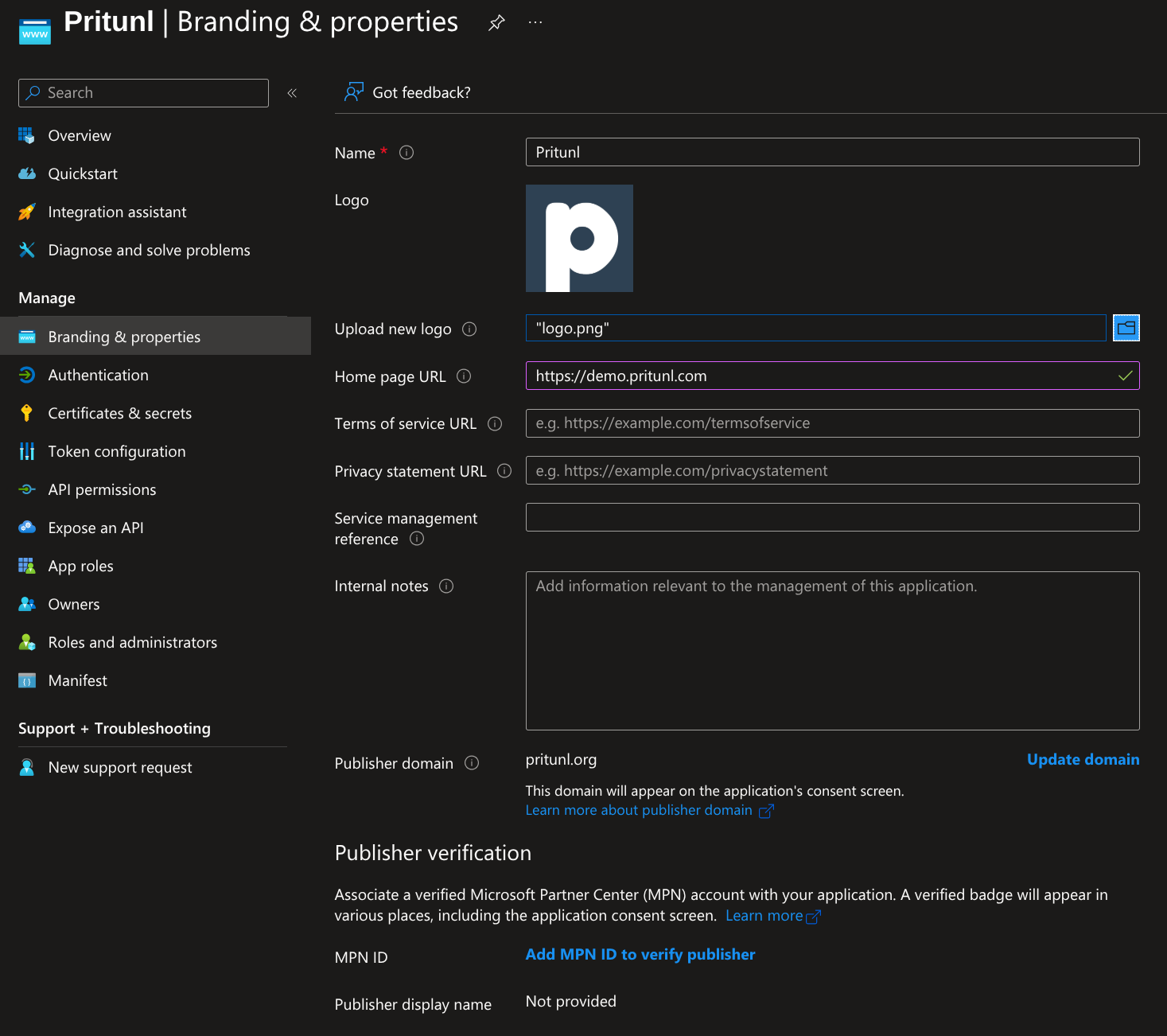
Open the Authentication tab and set Implicit grant and hybrid flows to Access tokens (used for implicit flows). Then click Save.
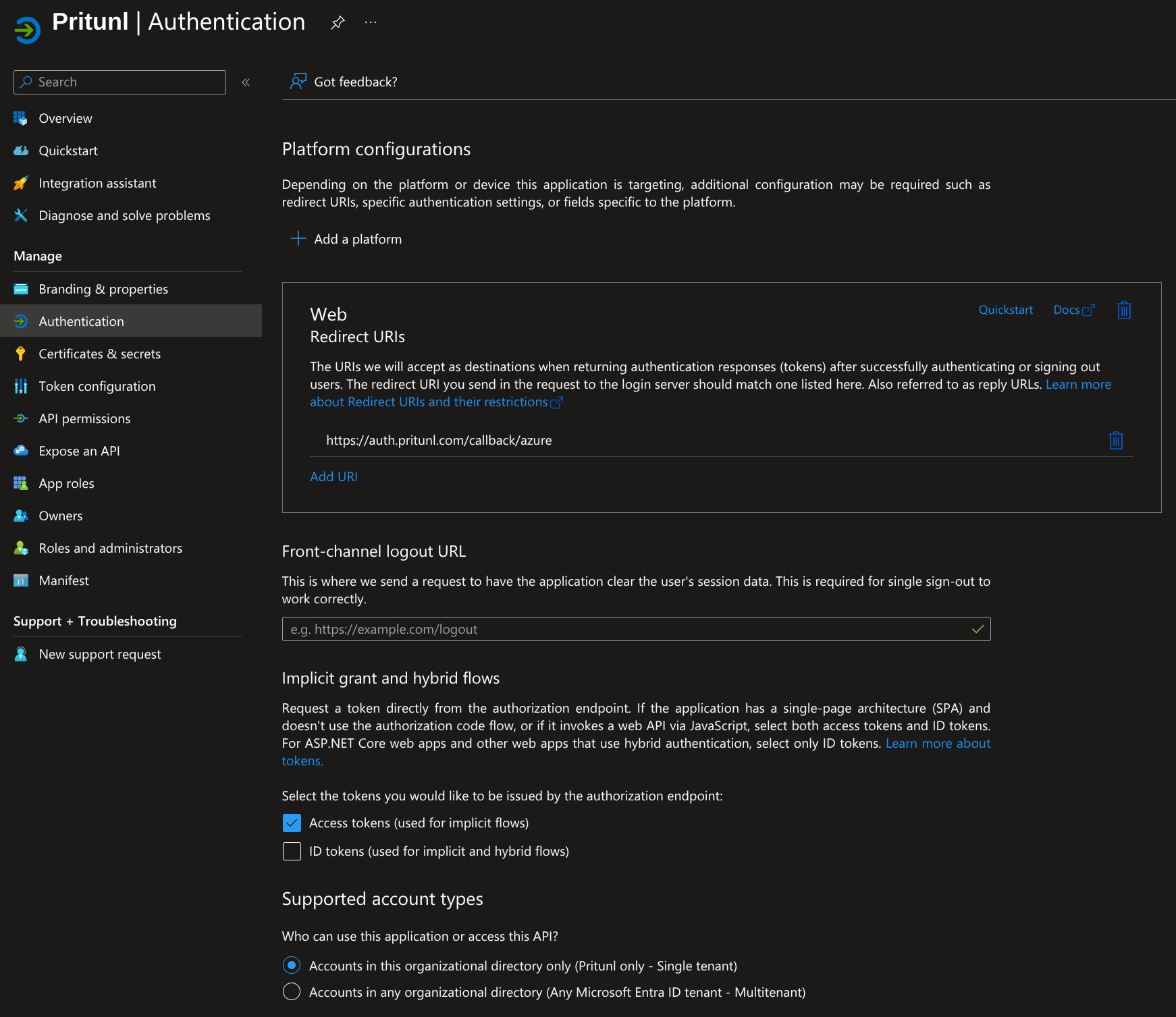
Open API permissions and click Add a permission. Then click Microsoft Graph and select Delegated permissions. Search for User.Read and select User.Read.
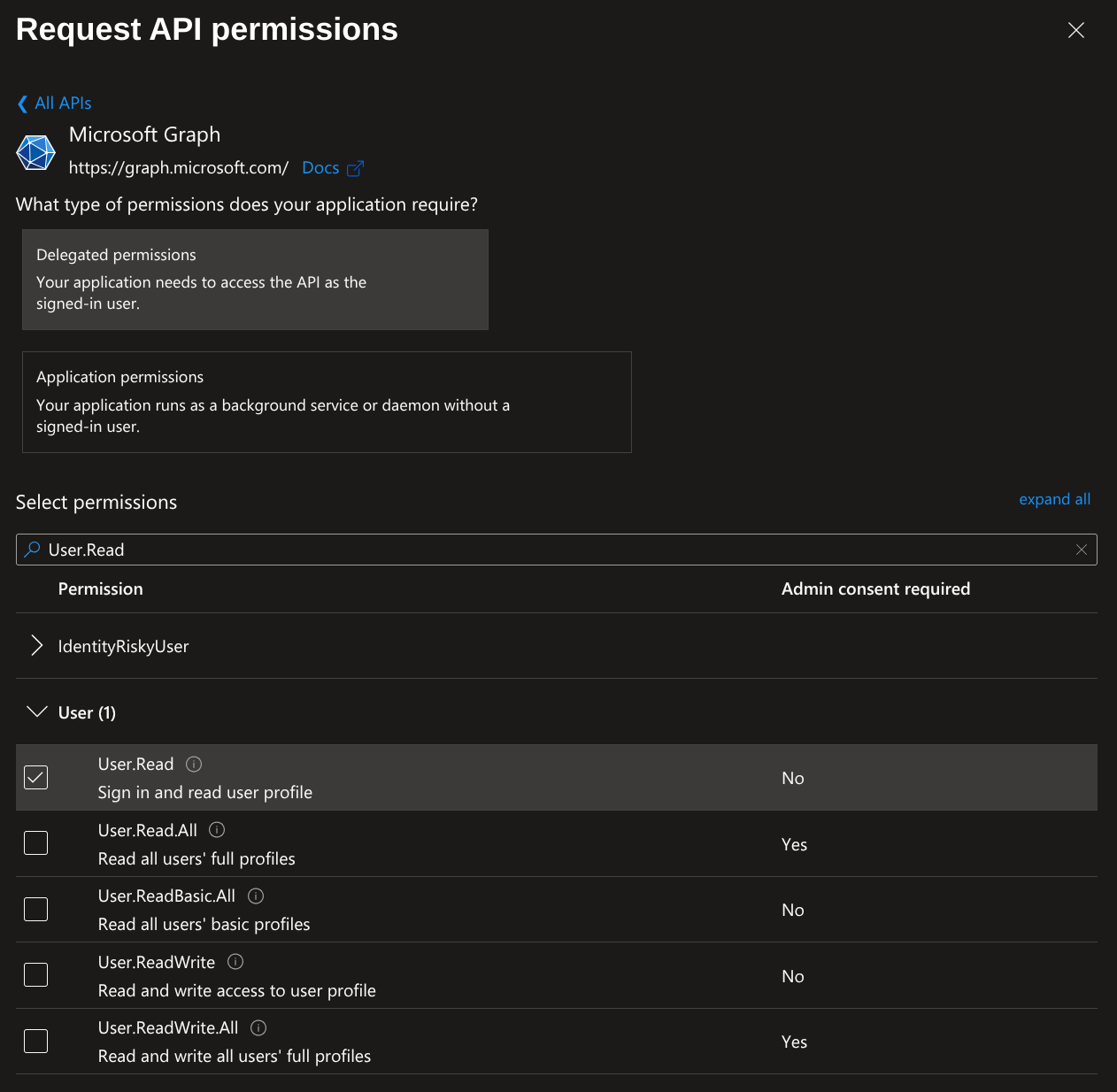
Next search for Group.Read and select Group.Read.All.
Next search for offline_access and select offline_access. Then click Add permissions
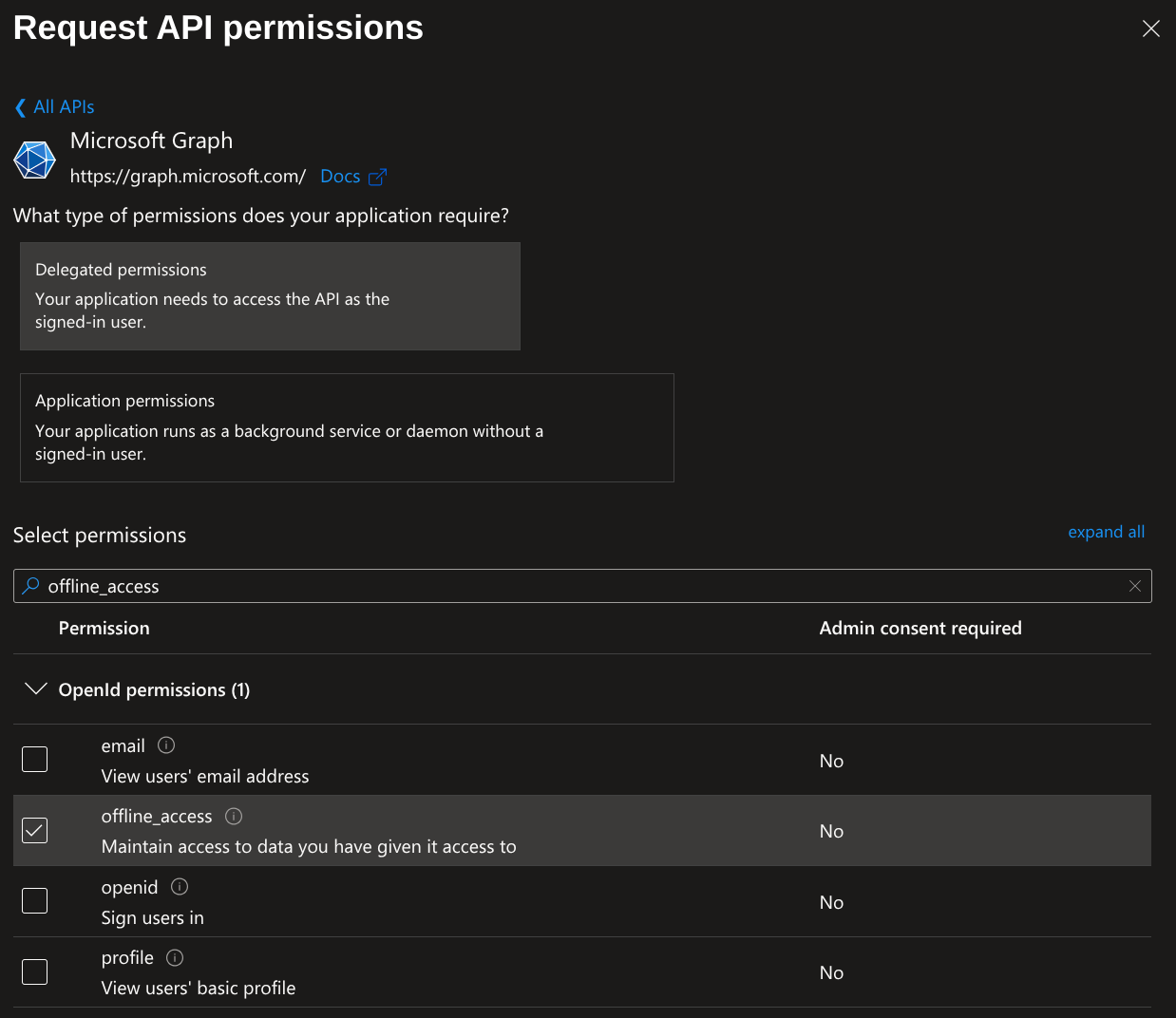
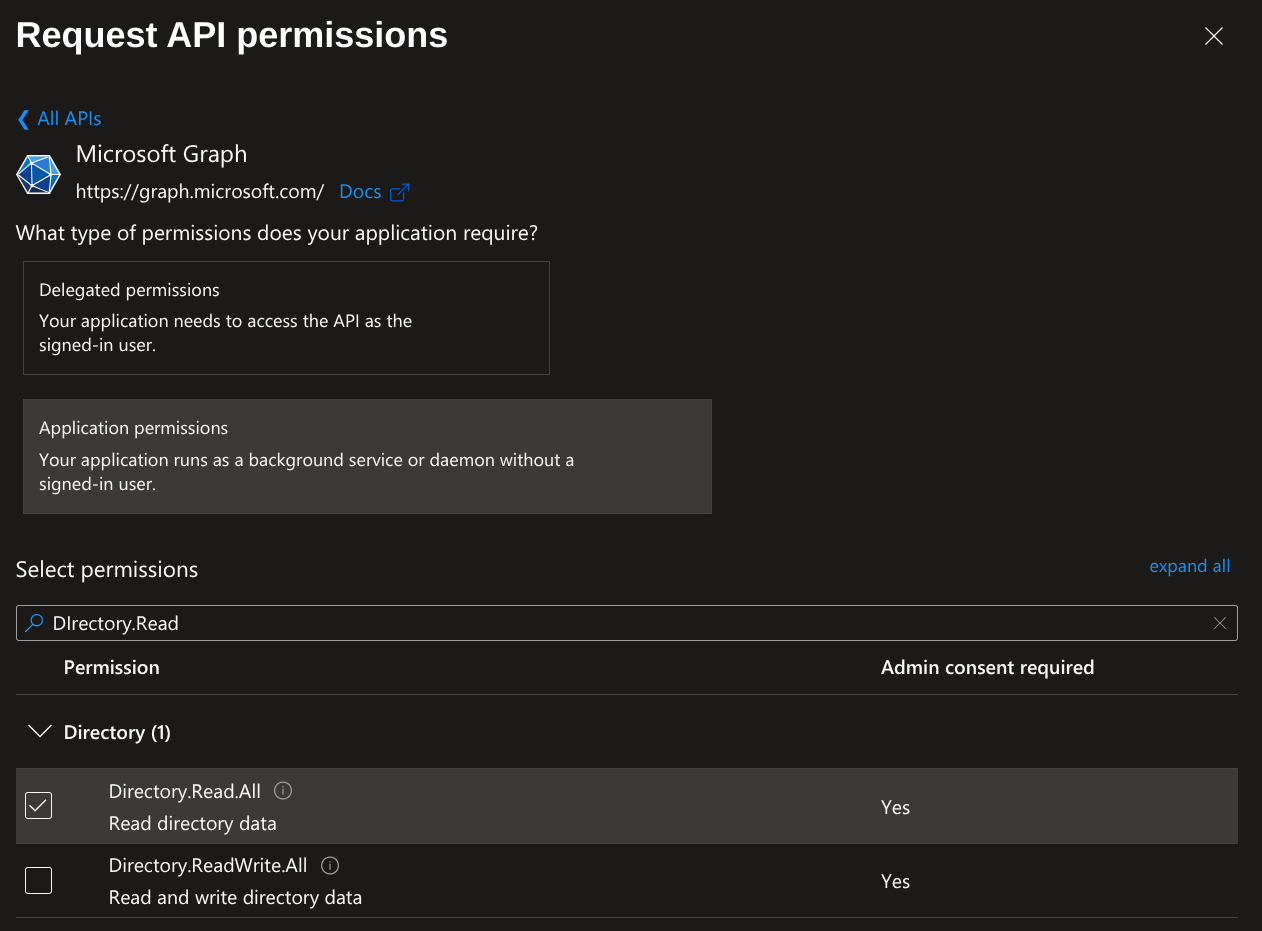
Next click Add a permission. Then click Microsoft Graph and select Application permissions. Search for Directory.Read and select Directory.Read.All. Then click Add permissions. This gives the Pritunl server access to lookup the Azure users groups for group to organization matching.
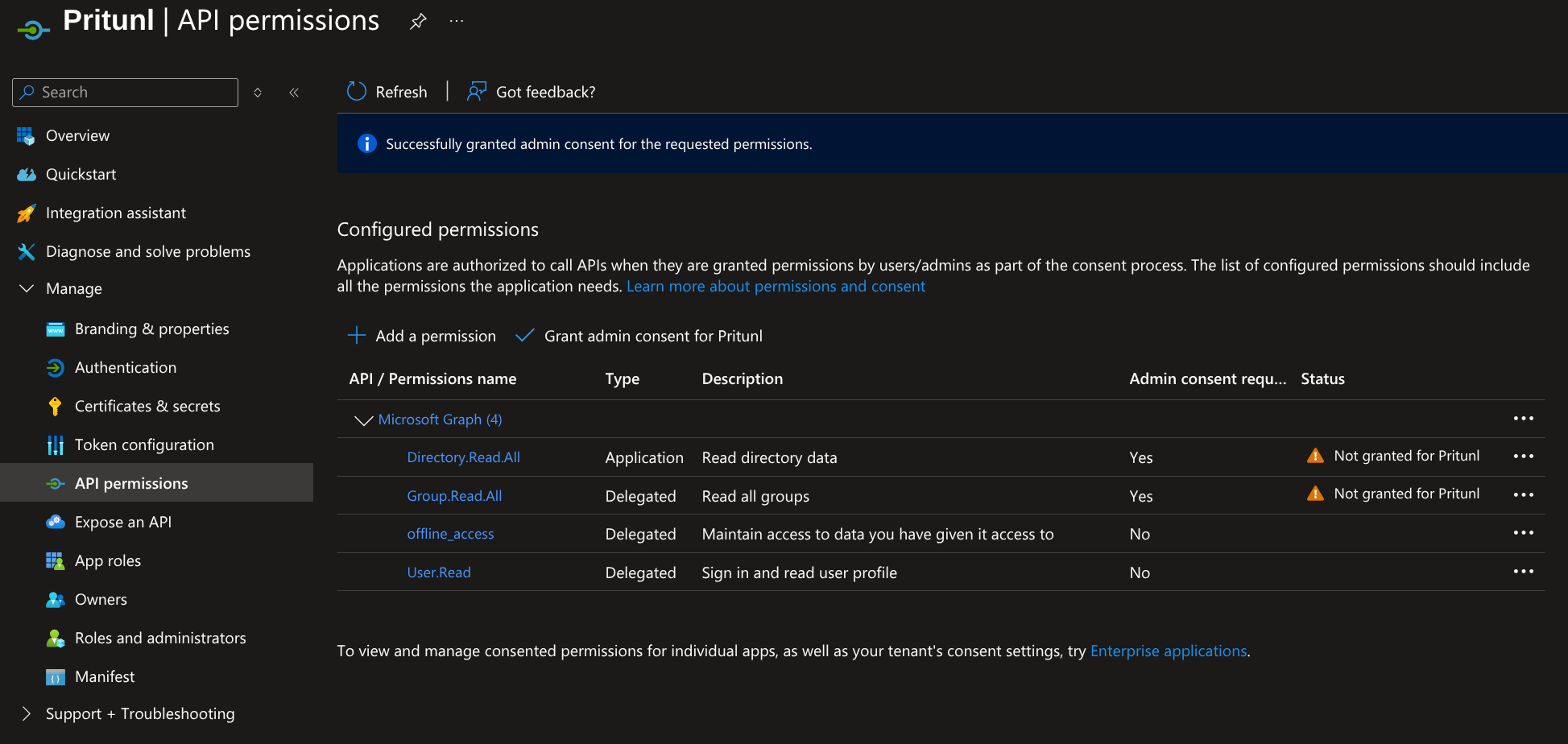
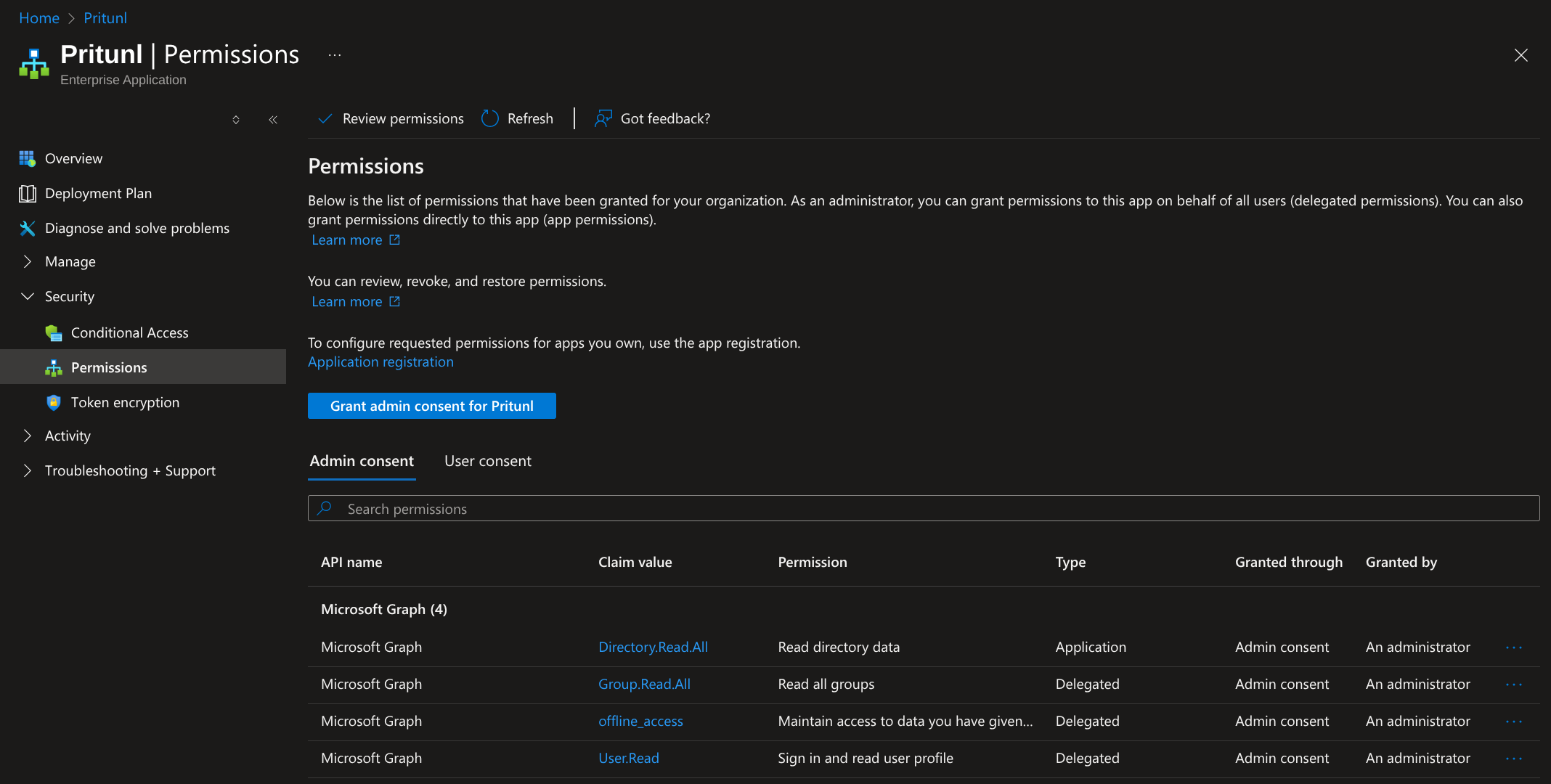
From the API permissions panel the permissions shown below should all be listed. After confirming this click Grant admin consent for Pritunl.
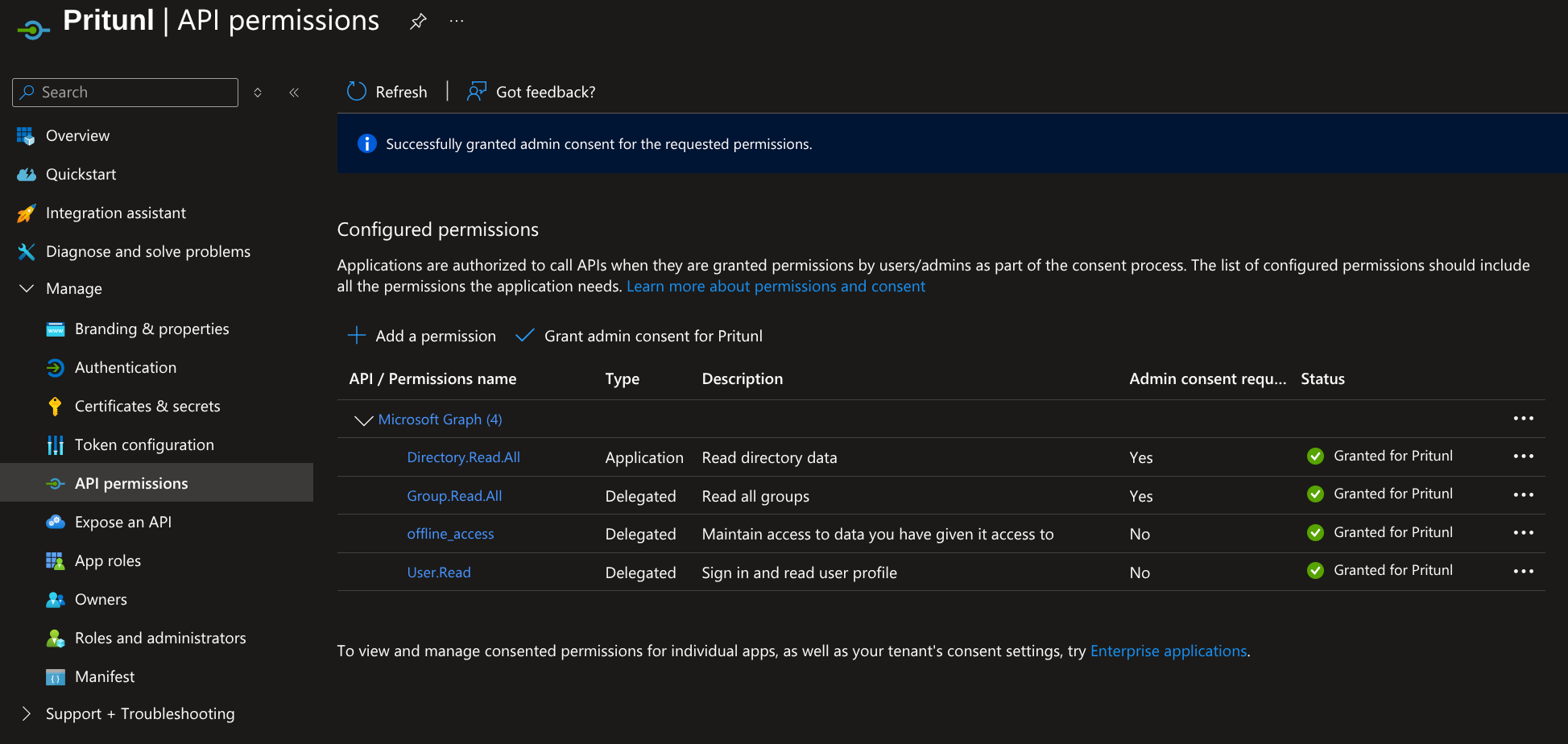
After this all permissions should have the status shown below.
Open Certificates & secrets and click New client secret. Then set the Description to Pritunl and set Expires to the maximum value available. Once done click Add.
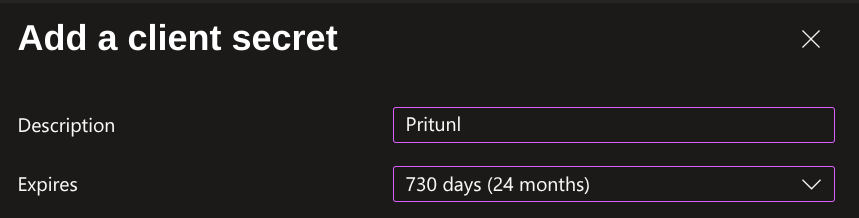
On the Certificates & secrets page copy the Value from the list of secrets. TheSecret ID is not relevant and should not be copied. Save this value and label it Azure Application Secret for the steps below.
Entra App Permissions
From the Azure Portal open Microsoft Entra ID then from the sidebar select Manage then Enterprise applications. This should display a list of the enterprise applications. This section is different from the previous App registrations section and contains different options.
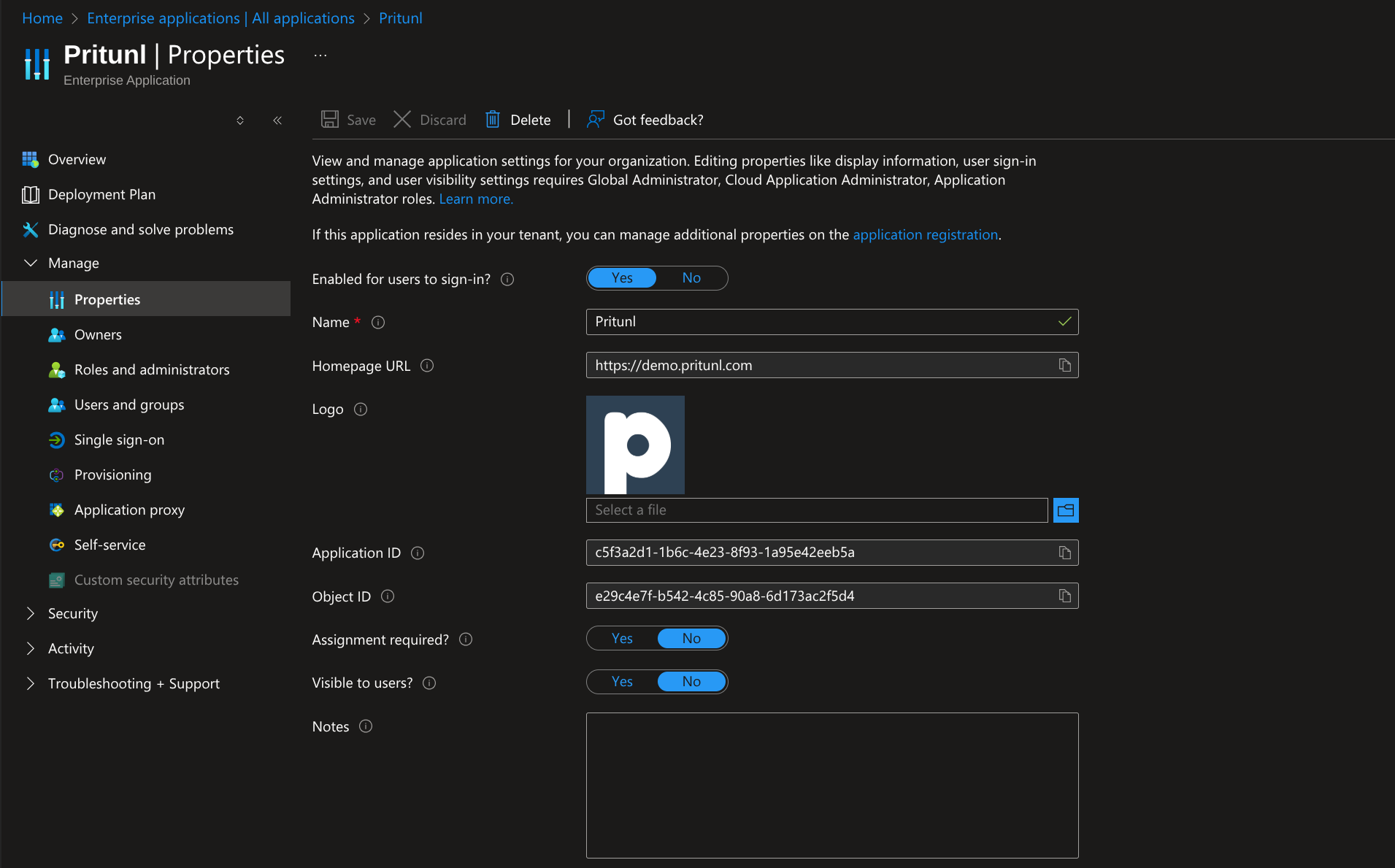
Select the Pritunl application to open the application management. This section will allow controlling access to the application and adding users. From the sidebar select Manage then Properties. This will display the Assignment required option. By default all users in the Azure organization will be able to access the Pritunl server. Turning assignment required on will require that users or a users group are manually added to the application from this management console. It is recommended to use this option for more secure and controlled access to the Pritunl server. Once done click Save at the top.
Next from the sidebar select Security then Permissions and click Grant admin consent for Pritunl. Then complete the prompts to approve the permissions.
Configure Pritunl
Open the Overview of the Pritunl app in App registrations. Copy the Directory (tenant) ID, and Application (client) ID for the configuration below.

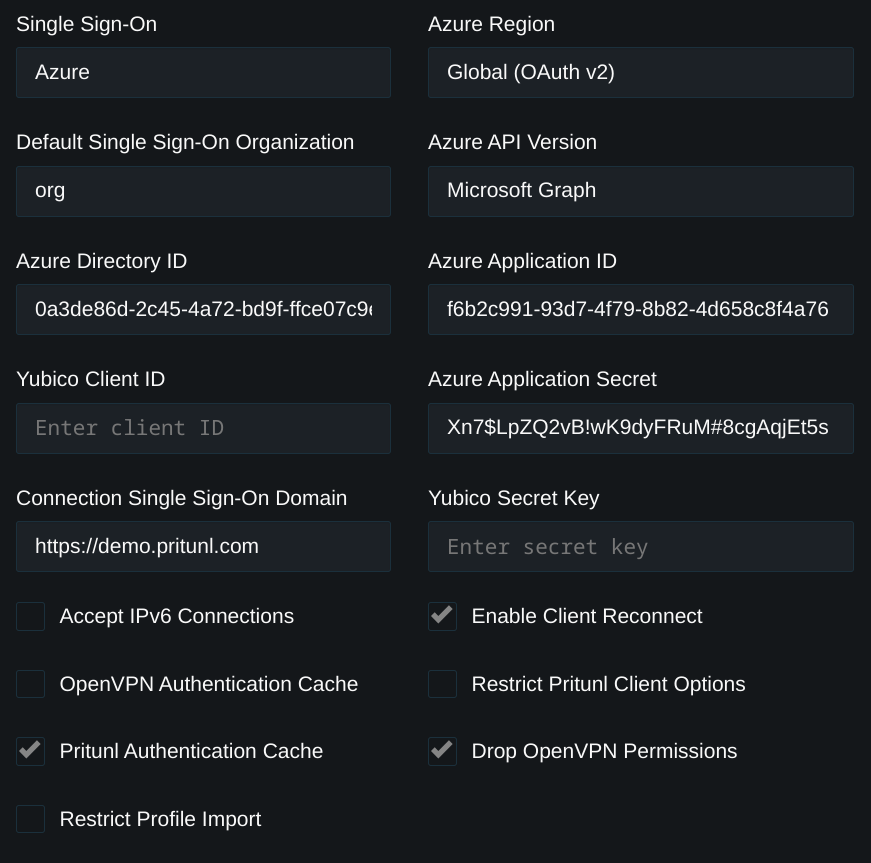
Open the Settings in the Pritunl web console and set Single Sign-On to Azure. Then set Azure Region to Global (OAuth v2) and Azure API Version to Microsoft Graph. Copy the Directory ID and Application ID from the steps above. Then copy the Azure key value from the earlier steps into Application Secret. When users sign in the Pritunl server will attempt to match one of the users Azure groups to a case sensitive name of an existing organization. This allows grouping users in Pritunl by their Azure groups. The Default Single Sign-On Organization will be used if none of the Azure groups match an existing Pritunl organization.
Configure Pritunl Zero
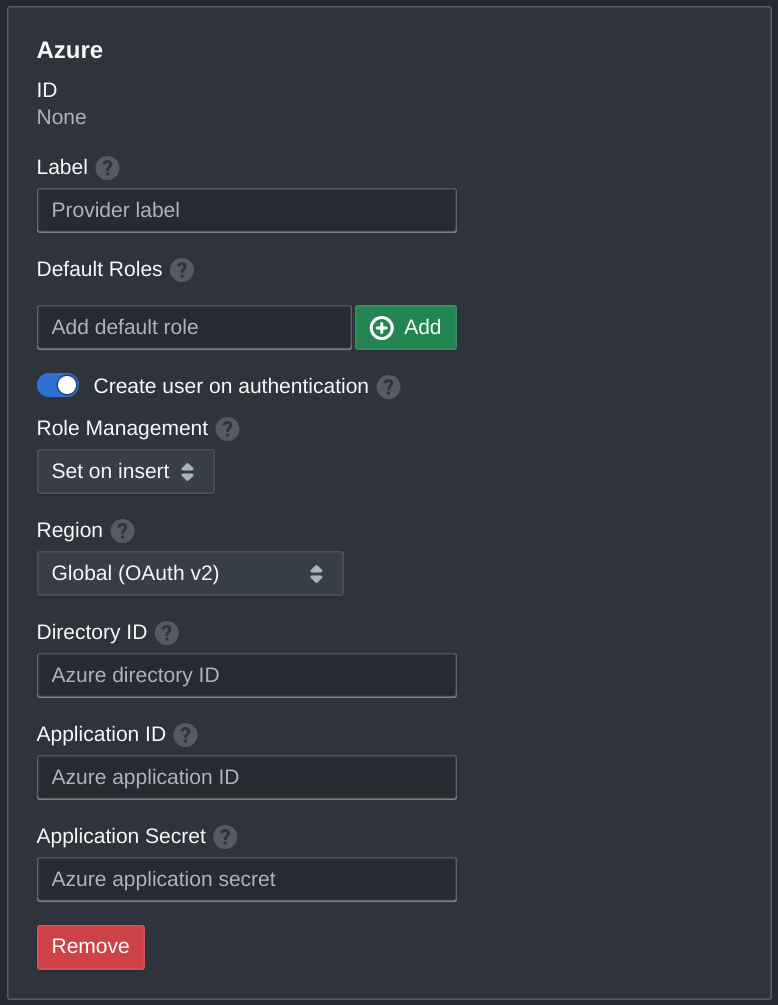
For Pritunl Zero these same options can be found in the Settings tab.
Azure Permission Issues
Adjustments to the Azure consent and permissions may be needed if error messages about admin approval required are shown. Refer to the Azure configure how users consent to applications documentation for more information.
Updated 4 months ago
