Connection Authentication
Pritunl connection authentication with single sign-on
By default when single sign-on is used in Pritunl the user will authenticate with the single sign-on provider from the Pritunl web console then import a VPN profile into a client. The VPN profile will contain a certificate and private key that will be used to authenticate the user to the VPN server. Instead of requiring the user to re-authenticate with single sign-on for each connection the Pritunl server will utilize the API from the single sign-on provider to verify the status of the user. This check will verify that the user exists and is not disabled. Most providers also support defining a single sign-on application, the API will also be used to verify the user has access to the defined application. These checks will occur for every connection even when authentication cache is enabled. If a single sign-on user were to fail the check the VPN connection would be blocked.
This design allows supporting all OpenVPN clients where there is no support for opening a web browser to complete authentication. It also allows the user to quickly connect to a VPN server without additional prompts. For most configurations this will not reduce the security of the connection, most users web browsers will already have a cached session for the single sign-on login. If the profile private key stored on the client was compromised the cached single sign-on sessions would also likely be compromised.
For additional authentication the Single Sign-On Authentication option can be enabled in the server settings. This will require the user to complete authentication with the single sign-on provider for each connection. The authentication cache can also be enabled in the top right settings to allow caching the authentication.
The most effective method of getting better connection security is to use multi-factor authentication. Pritunl provides multiple options for multi-factor authentication. This will always provide a higher level of security.
This option requires an updated Pritunl server and Pritunl client.
Feature Support
| Feature | Default Configuration | SSO Authentication |
|---|---|---|
| User authentication with profile certificate and private key | ✅ | ✅ |
| User status verified with single sign-on API | ✅ | ✅ |
| Multi-factor authentication with single sign-on provider | ✅ | ✅ |
| Supports connection authentication cache | ✅ | ✅ |
| Supports all OpenVPN clients | ✅ | ❌ |
| Requires web browser single sign-on prompt for connections | ❌ | ✅ |
| User pin | ✅ | ❌ |
| Google Authenticator | ✅ | ❌ |
Configuration
Single sign-on connection authentication can be enabled for each individual server. This allows configuring servers with or without single sign-on authentication. Only single sign-on users will be able to connect to a server with single sign-on authentication.
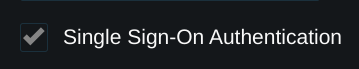
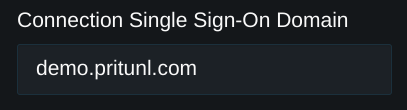
After this option has been enabled on a server the Connection Single Sign-On Domain will appear in the top right settings. This should be configured to a domain that is used to access the Pritunl web console. If a load balancer is configured for access to the web console the domain of the load balancer should be used.
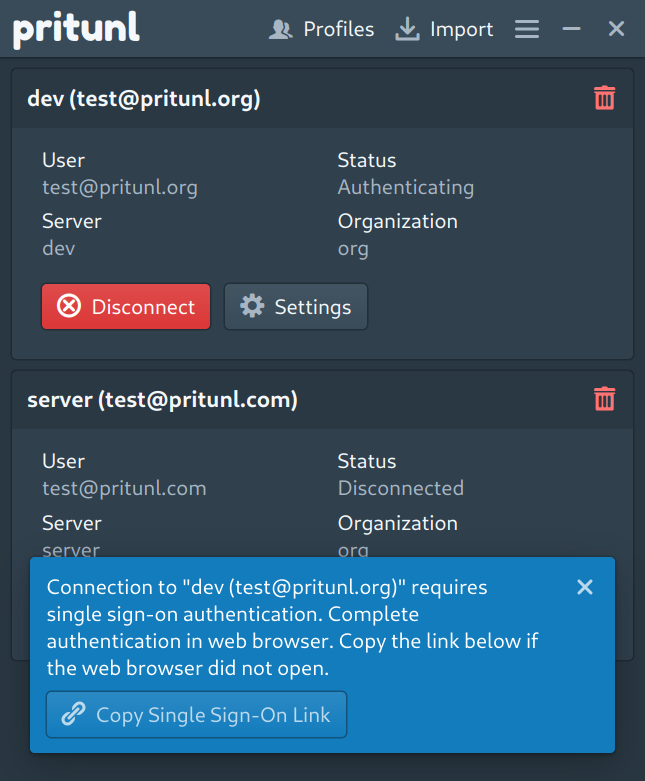
Once the option is configured a web browser will open after the user clicks connect. If a default system browser is not configured the link can be copied from the prompt shown.
Once the web browser opens the user will complete the single sign-on authentication and the VPN connection will authenticate.
Updated 3 months ago
