Active Directory with Organizations
Single sign-on with Active Directory including Organizations
This tutorial will explain including organization and group names in the Active Directory Radius response. This will allow adding Pritunl users to organizations and groups based on the users group membership in Active Directory. Each organization will need a network policy which will include the Pritunl organization and group names as custom string attributes.
To start create a new network policy. For this example the Pritunl Developers organization will be used. The name of the network policy should include the Pritunl organization name.
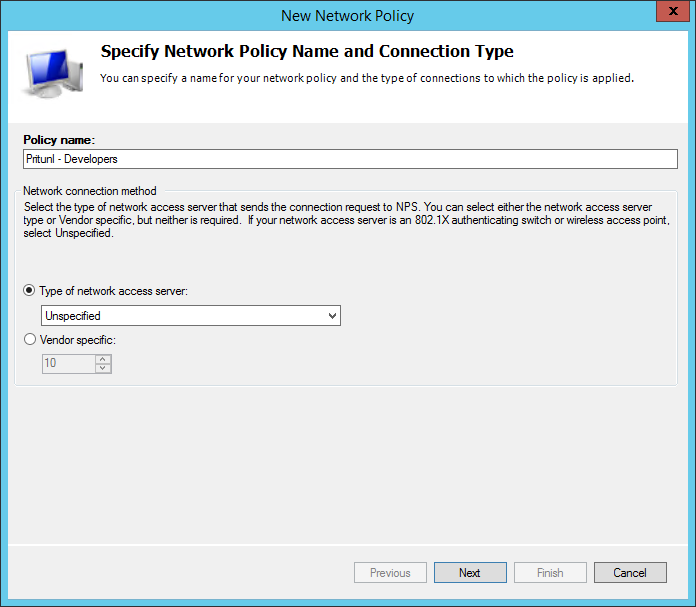
Next create a condition for the network policy to only match users in the Developers group in Active Directory.
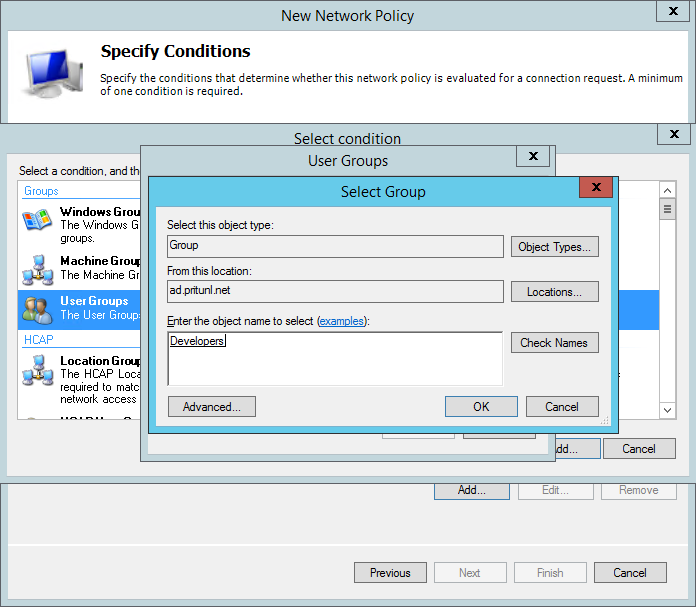
Then select Add and choose the ClientIPv4Address and enter the IP address of the Pritunl server. This will only allow the policy to be used by the Pritunl server.
For the authentication methods configuration select Unencrypted authentication (PAP, SPAP).
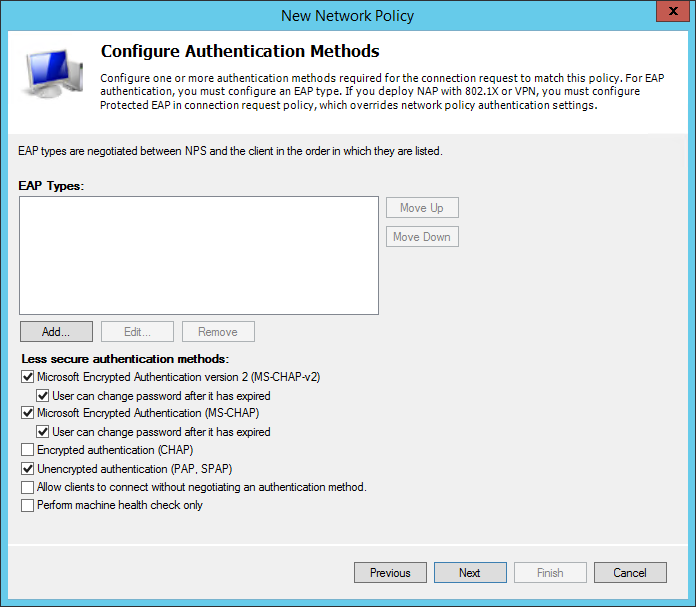
In the configuration settings select the Vendor Specific section then click Add.
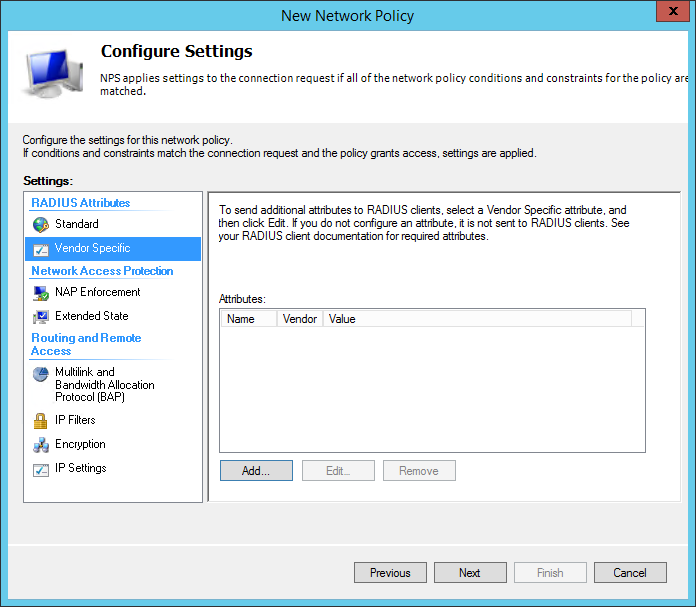
In the add vendor specific attribute window set Vendor to Custom then select the Vendor-Specific attribute. Then click Add.
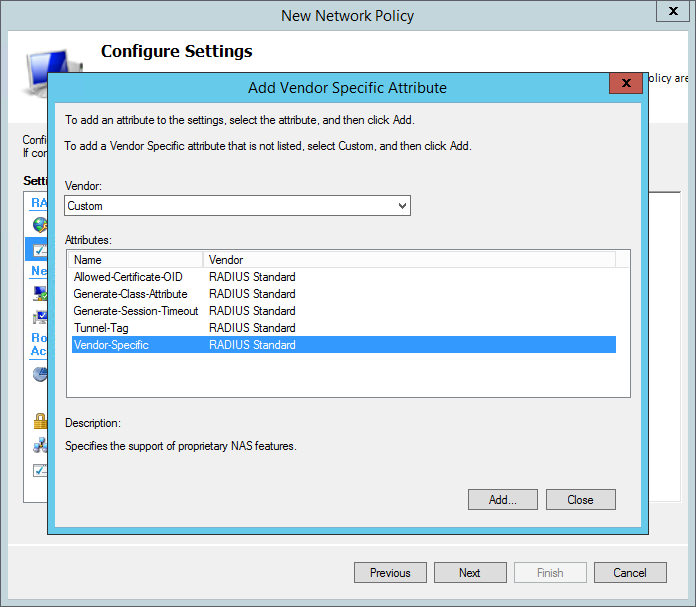
In the attribute information window set the vendor code to 97 then select Yes. It conforms and click Configure Attribute.
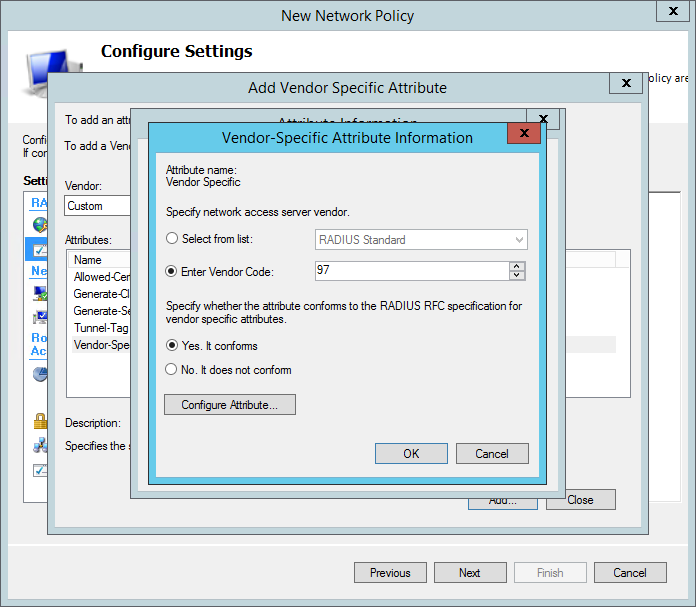
In the VSA configuration window set the attribute number to 0 and the format to String. Then enter one organization name in the value. The organization name must match an existing organization in Pritunl. Multiple organization names can be provided by adding additional attributes with the attribute number 0. Pritunl will add the user to the first matched organization.
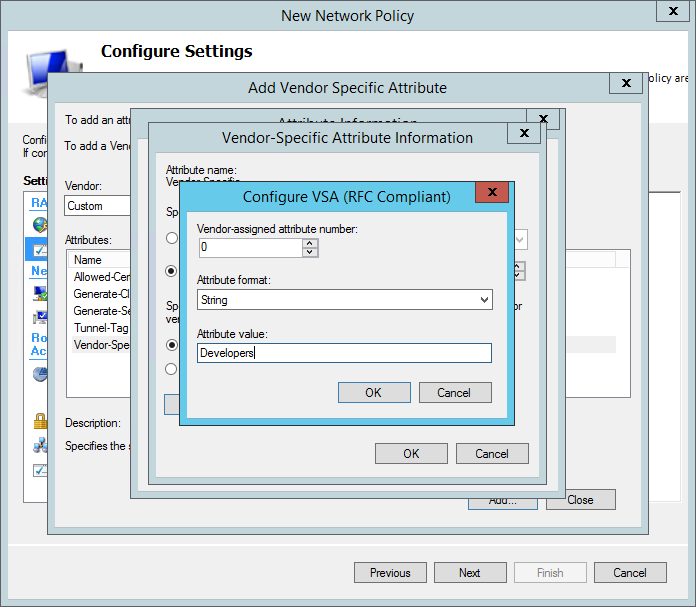
Group names can also be included by are not required. This can be done by adding repeating the process above to add an attribute with vendor code 97 then setting the attribute number to 1. Multiple group names can be provided by adding additional attributes with the attribute number 1. Pritunl will add the user to all of the groups specified.
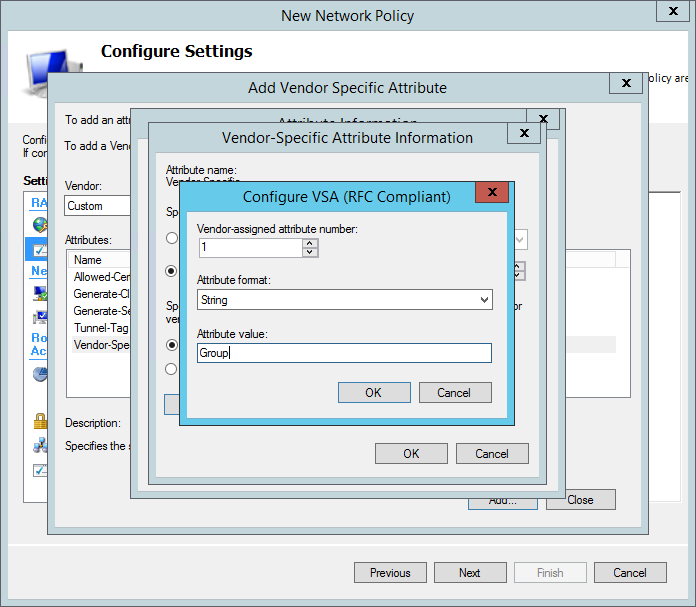
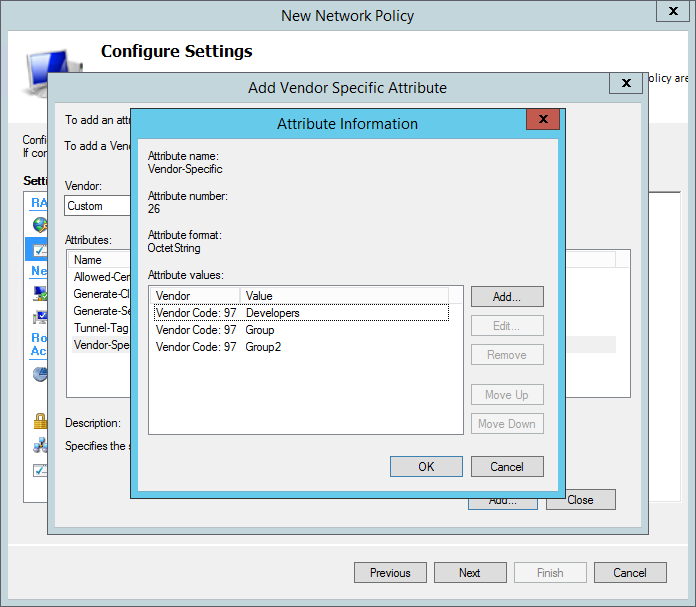
Once done the attribute information window should look similar to the example below. This example will add the user to the Developers organization and both groups Group and Group2.
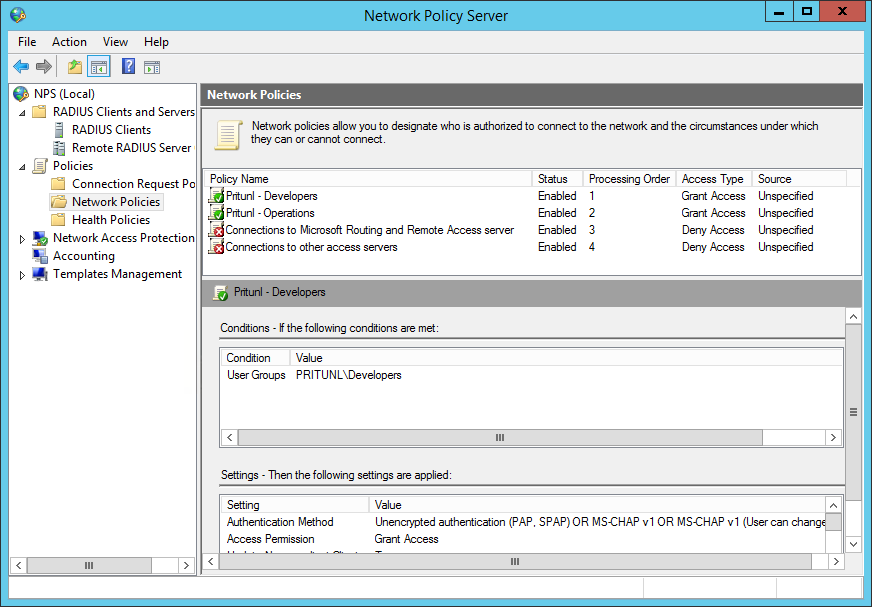
For users belonging to multiple Active Directory groups the priority can be configured by moving the network polices. The example below shows the Developers organization taking priority over the Operations organization. A user that is a member of both Developers and Operations will be added to the Developers organization.
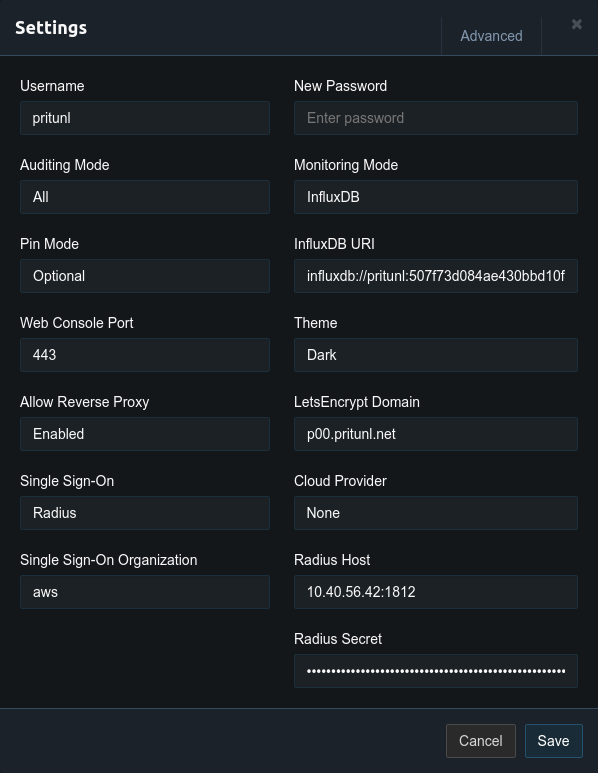
Once the Radius server is configured enter the IP address of the Windows Radius server with port 1812 and the shared secret from earlier in the Pritunl settings. Users will then be able to login to the web console using their Active Directory credentials. When users connect they will also be required to enter their Active Directory password.
The event viewer is useful for determining why Radius authentication requests failed.
Updated 4 months ago
