Single sign-on with Google
Pritunl supports single sign-on with Google G Suite. This allows users to use their Google employee account to authenticate with Pritunl. Oauth is used to authenticate users, re-authentication is also done on each connection. When a Google user is removed or disabled they will no longer be able to connect to a Pritunl server. To start set the Single Sign-On to Google and set the Google Apps Domain. The domain should be the domain used for the business Gmail such as pritunl.com. Multiple domains can be separated by a comma. The single sign-on organization will control which organization Google users are added to.
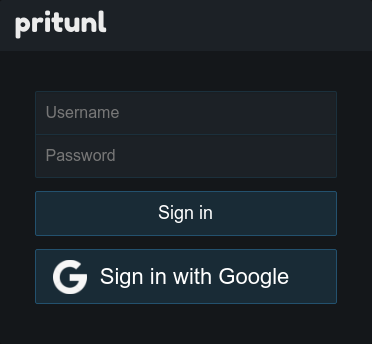
Once configured a Sign in with Google button will appear on the login page.
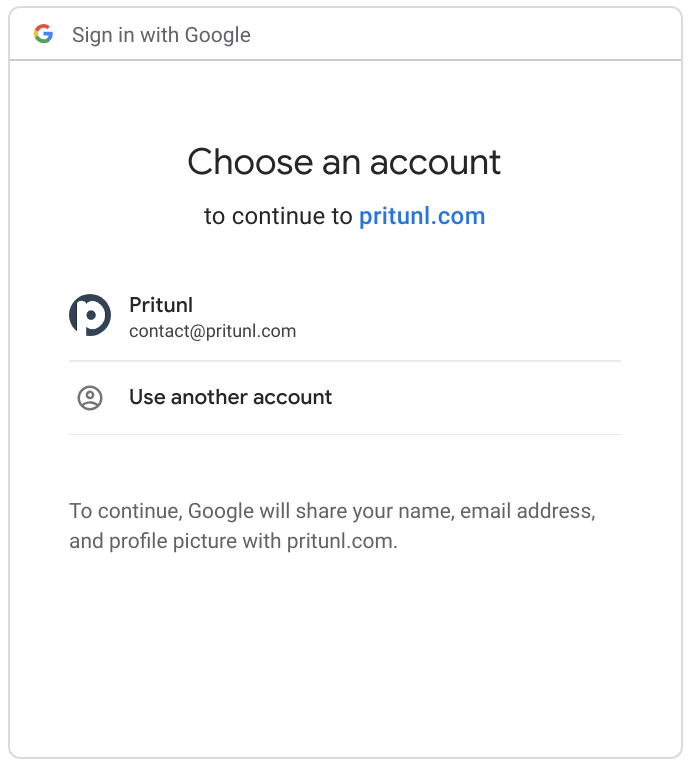
After a user clicks Sign in with Google they will be prompted to approve the Oauth login. Then they will be directed to their VPN profiles.
Match Groups to Organizations
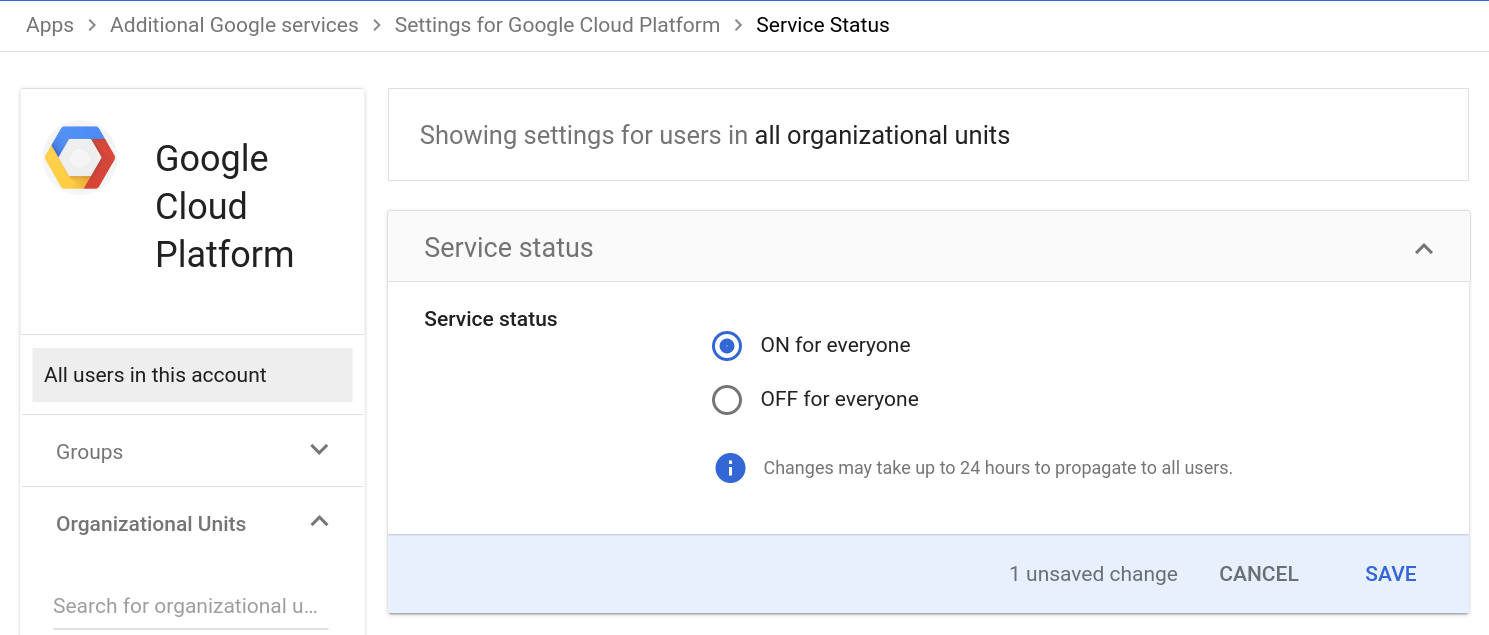
From the Google Workspace Admin Console search for Google Cloud Platform and select Settings for Google Cloud Platform. Then enable the service.
Open the Google Cloud Console and create a project if one does not already exist.
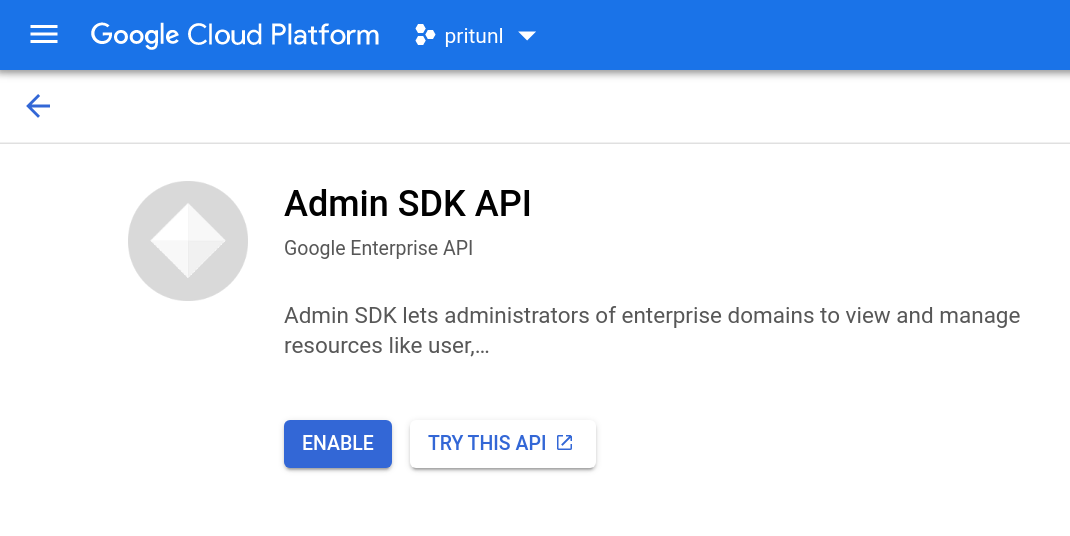
Either open the Admin SDK API Settings or use the search from the cloud platform console to search for Admin SDK API. Then click Enable.
From the navigation menu select IAM & Admin then IAM. From the IAM page open Service Accounts.
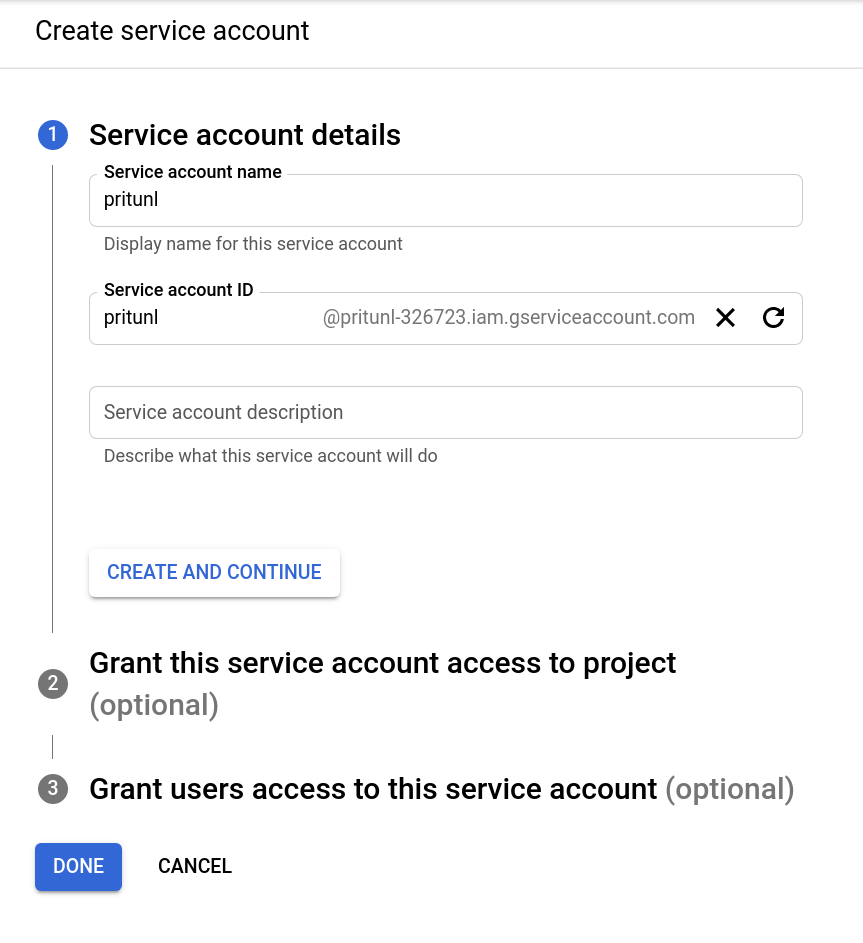
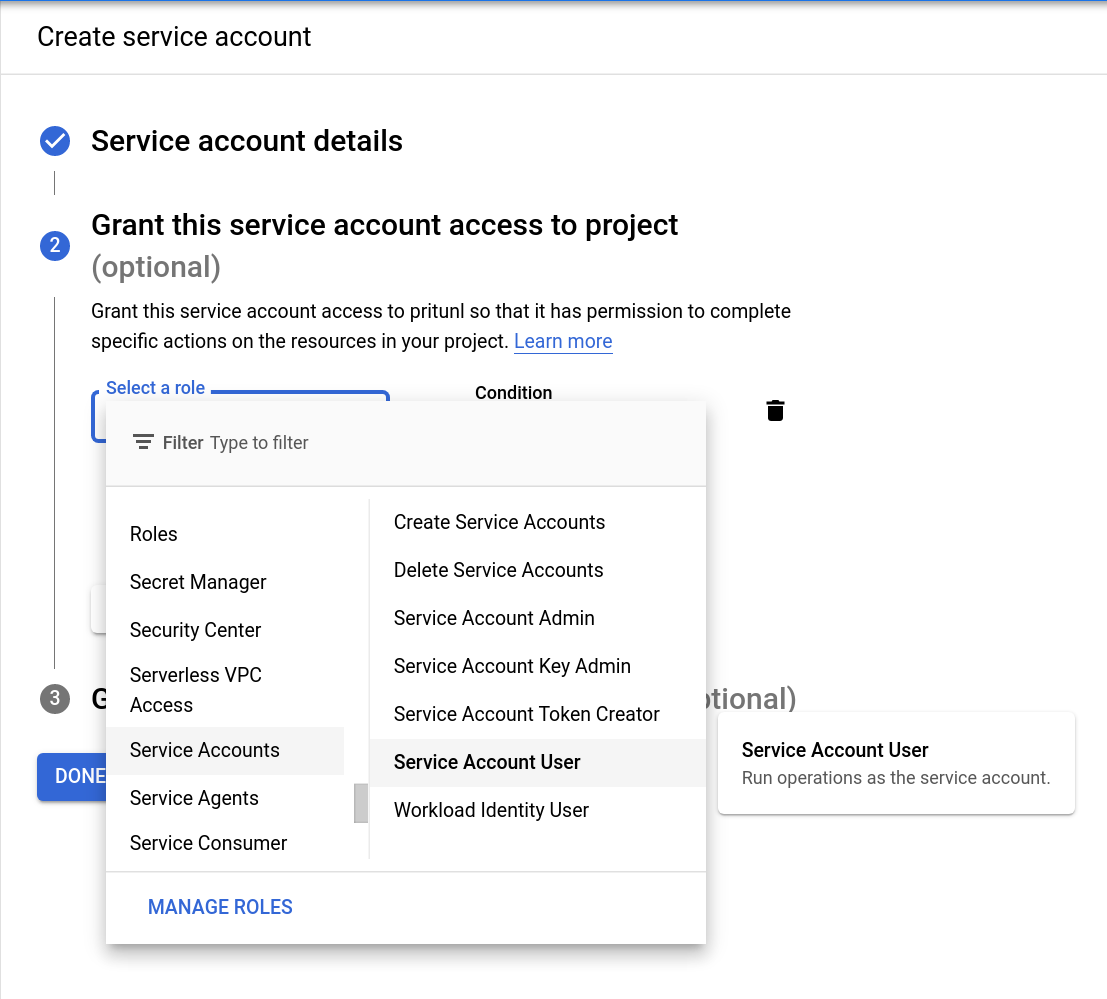
Click Create Service Account and name the service account pritunl. Then click Create and Continue.
Click Add role and select Service Accounts then select Service Account User. Click Continue then click Done to create the service account.
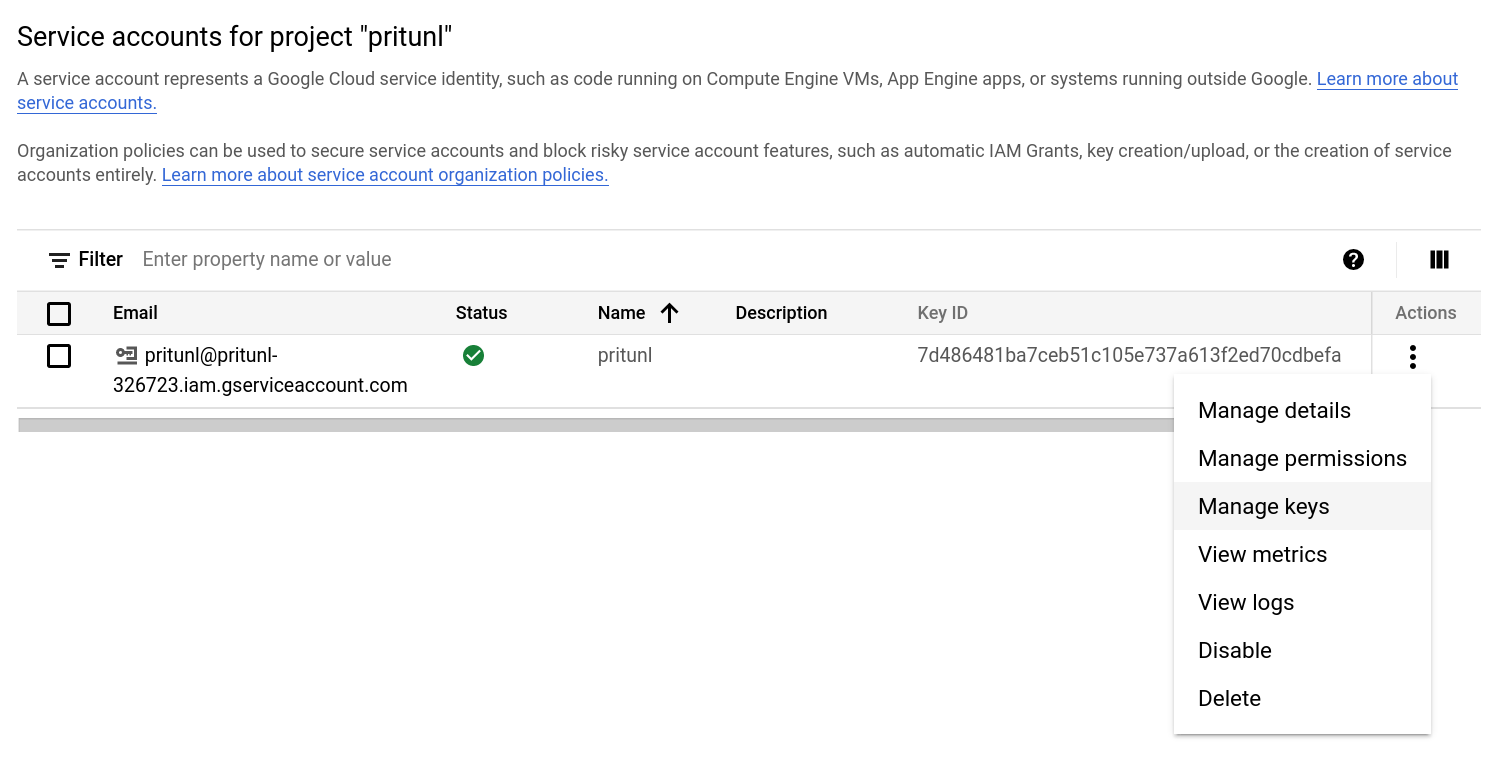
Click the menu button for the user under Actions then click Manage keys.
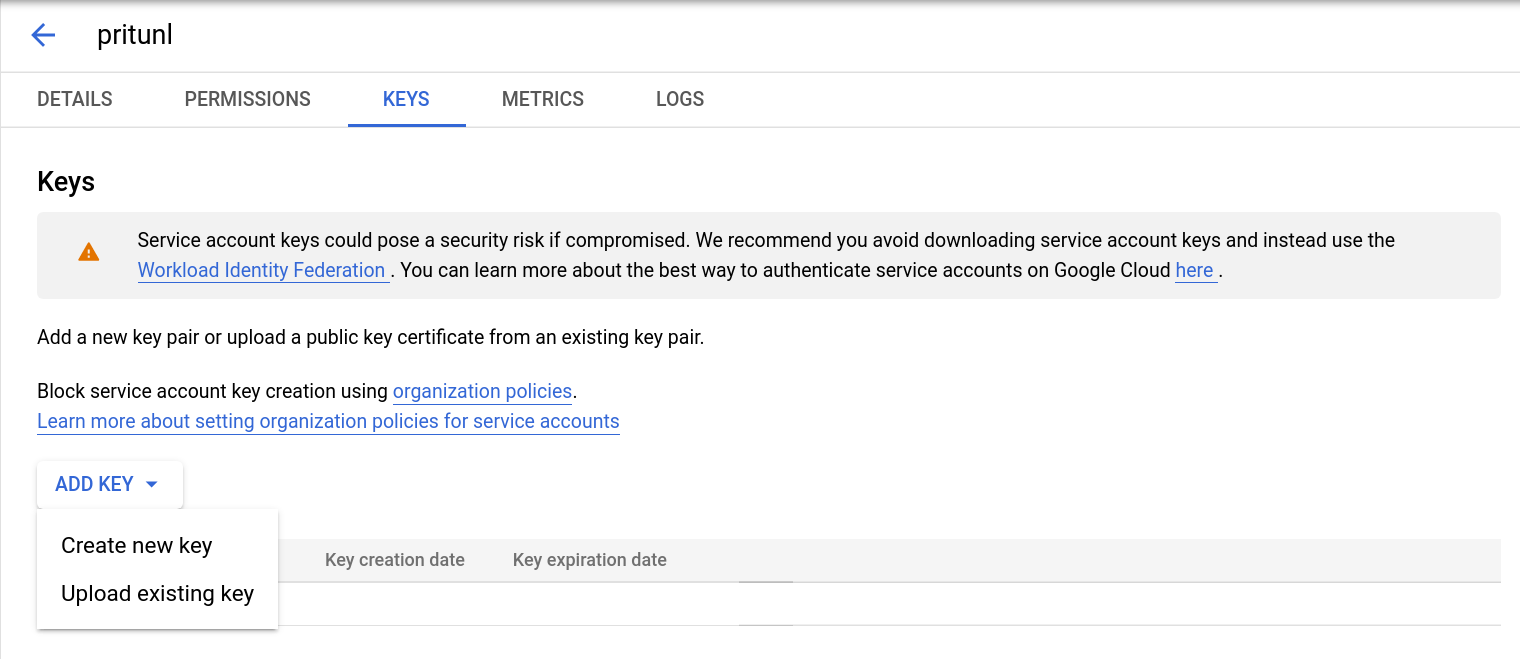
Click Add Key and Create new key.
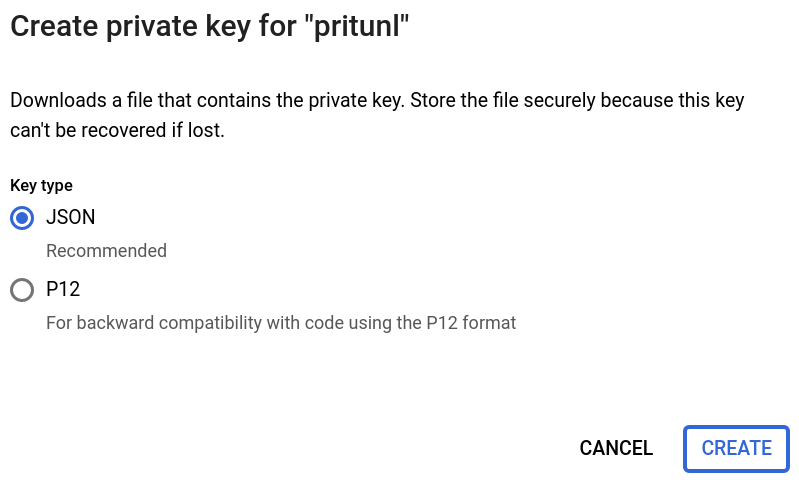
Set the Key type to JSON and click Create. The key will be downloaded in json format.
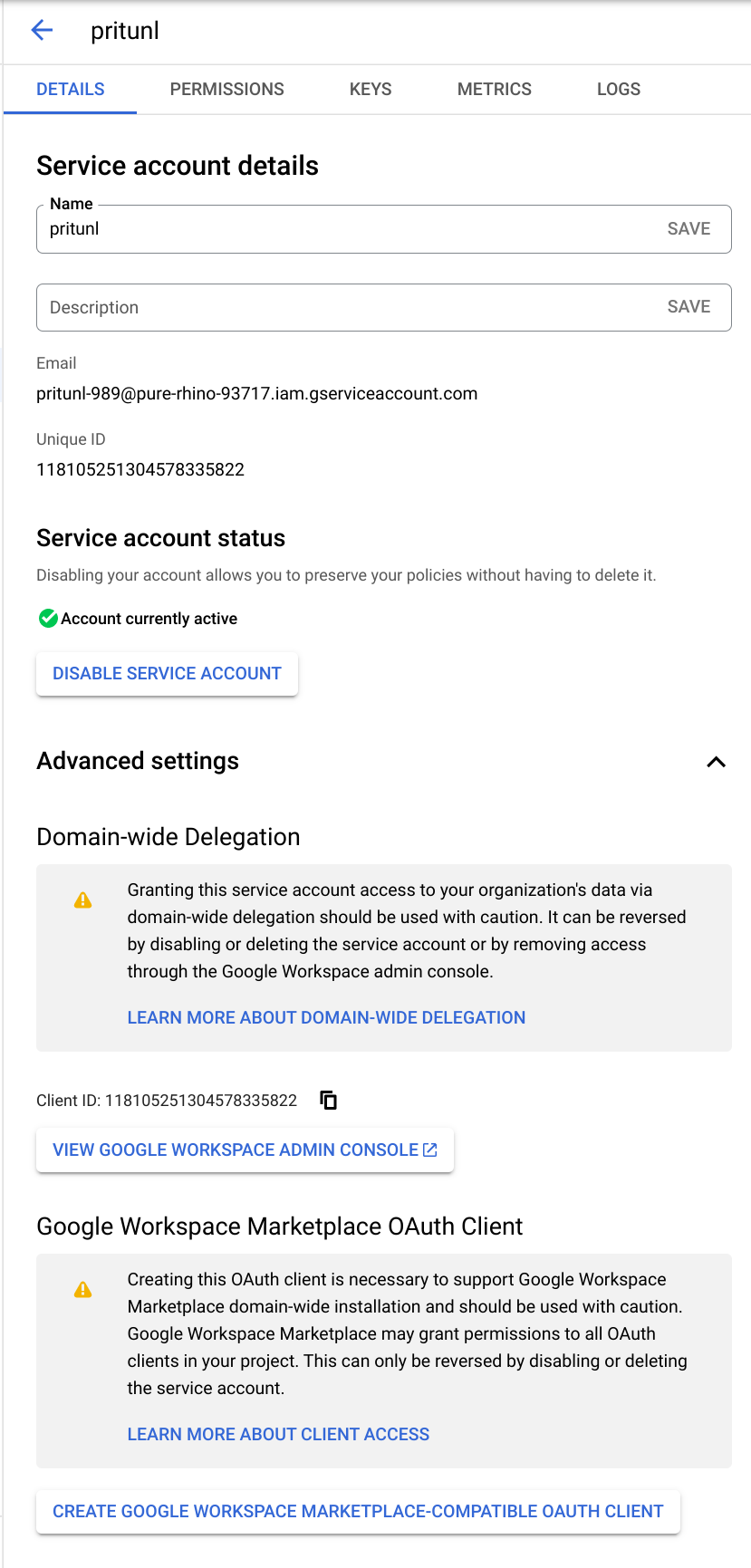
Either open the Details tab from the keys page or click Manage details from the user actions menu.
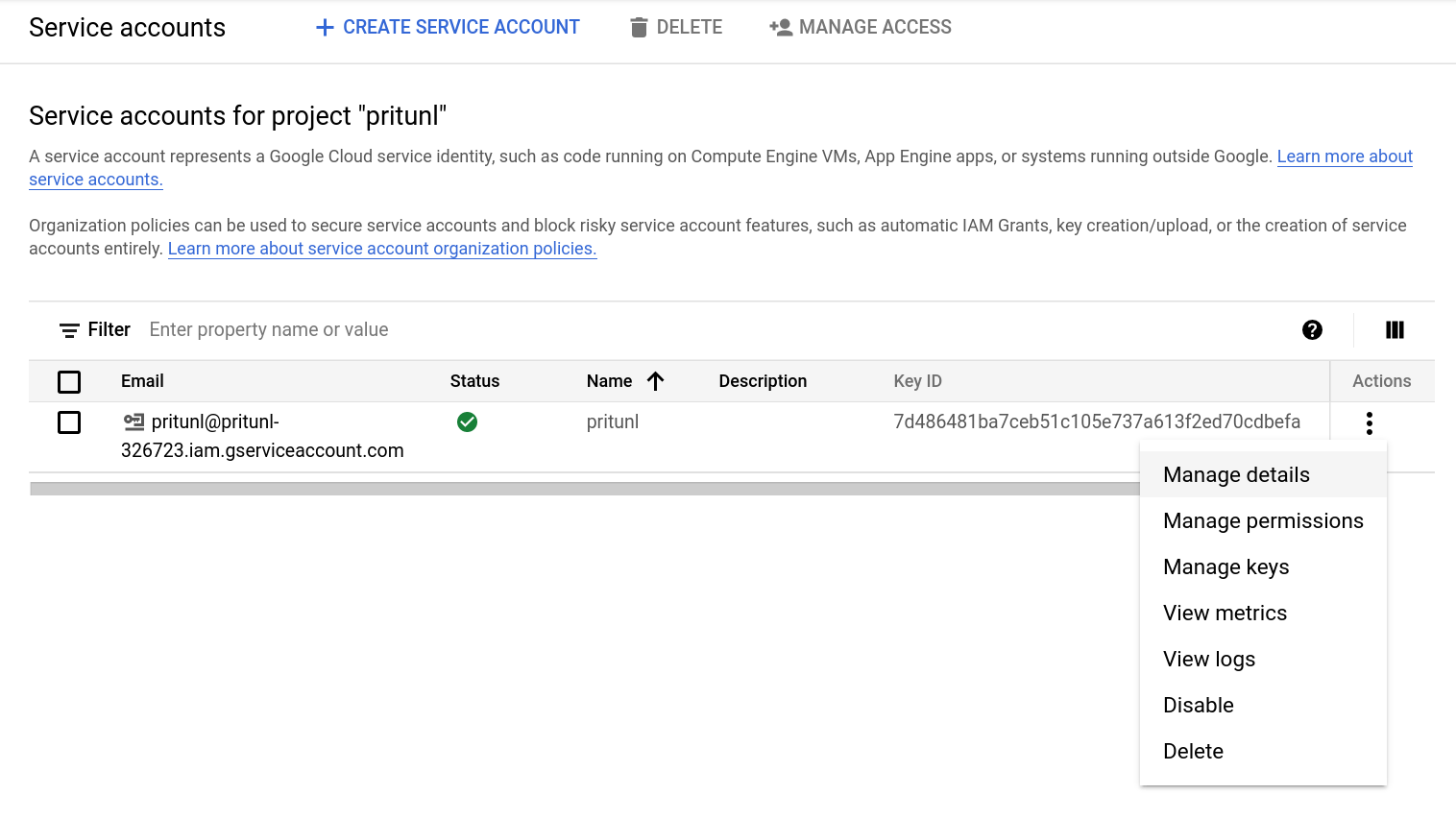
Copy the Unique ID shown for the next steps.
Go to the Google Workspace Admin Console and select Security then Access and data control then API controls from the menu. Enable Trust internal, domain-owned apps.
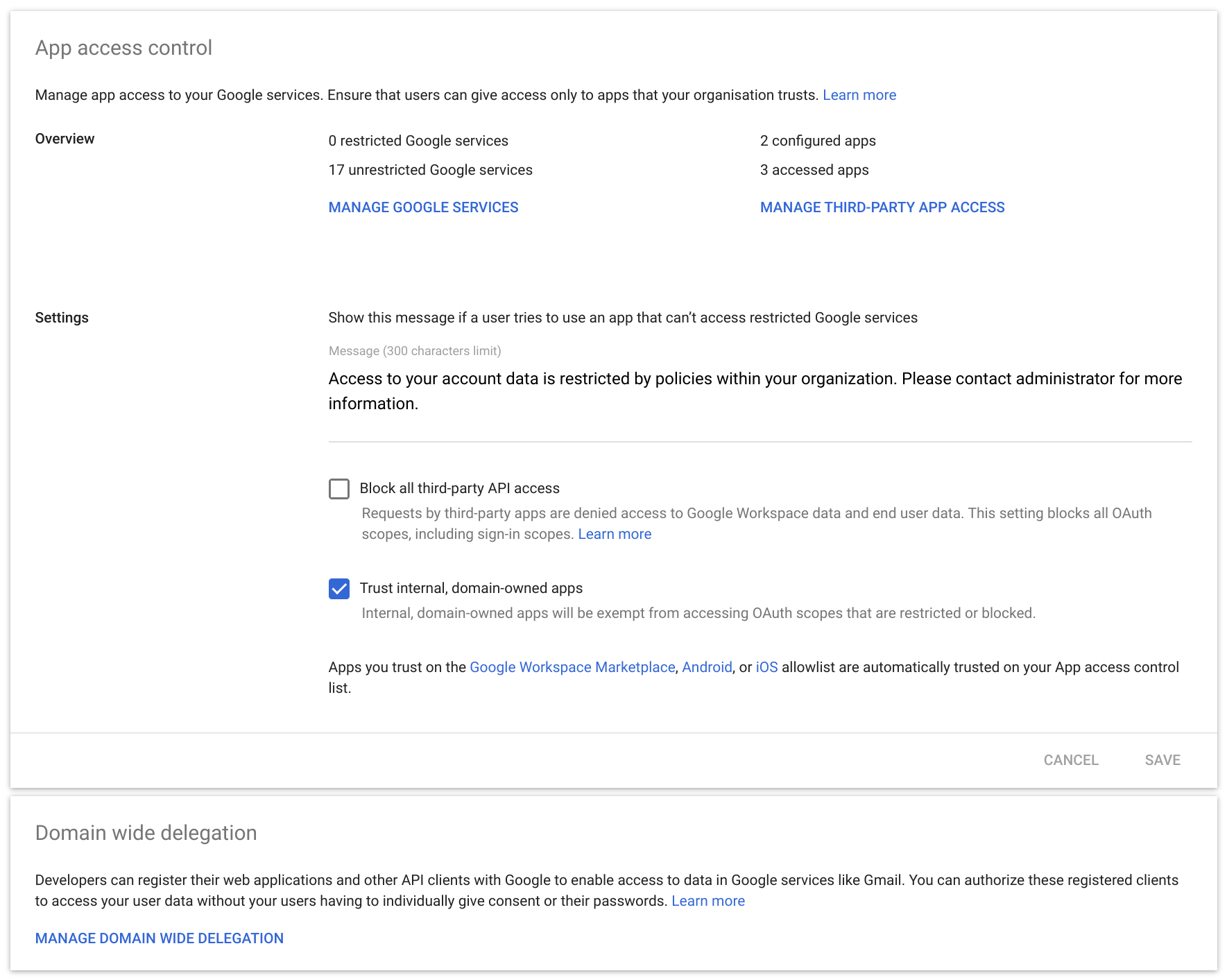
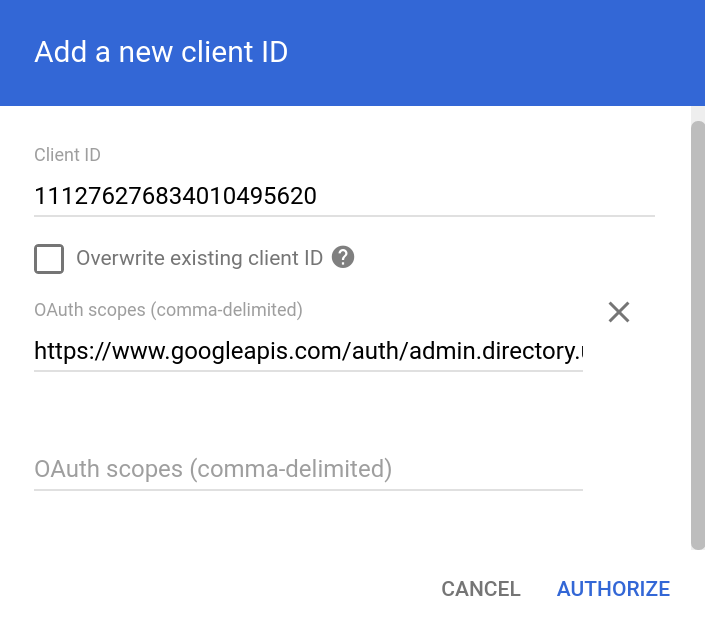
Once done click Manage Domain Wide Delegation. Then click Add new then enter the Client ID from the previous steps. Set the OAuth scopes to https://www.googleapis.com/auth/admin.directory.user.readonly, https://www.googleapis.com/auth/admin.directory.group.readonly and click Authorize.
Open the settings from the Pritunl web console and verify the Google Apps Domain is set to the correct company domain. Then set the Google Admin Email to any Google Workspace administrators email, this is used by the Google Cloud API to discover the Google Workspace Domain. Open the json file that was downloaded from the previous steps and copy the key to Google JSON Private Key. Then click Save.
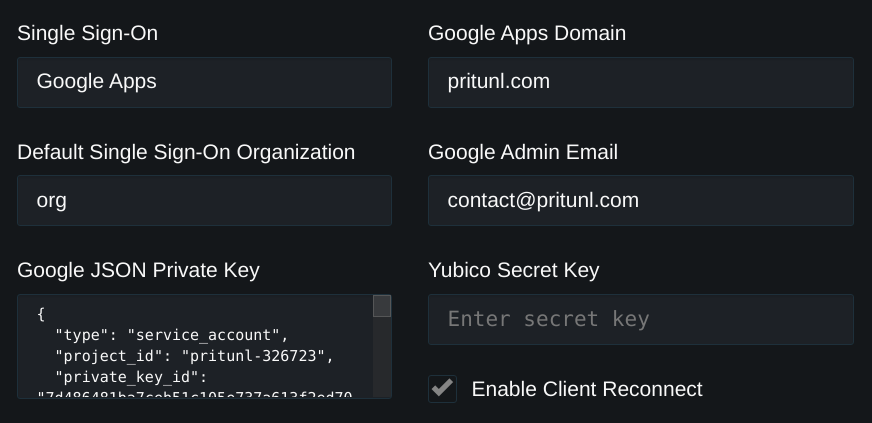
Once done the Pritunl user will be created in the matching organization when authenticating with Google. The logs will display what names are discovered when a user authenticates.
Configure Pritunl Zero
For Pritunl Zero these same options can be found in the Settings tab.
Updated 4 months ago
