Getting Started Host Certificates
Configure Pritunl Zero host certificates and bastion SSH server
This guide requires first installing and configuring Pritunl Zero for SSH. Follow the Getting Started SSH for instructions on configuring Pritunl Zero for SSH. This guide explains configuring host certificates and a bastion host. If only host certificates are being configured the bastion host sections can be skipped.
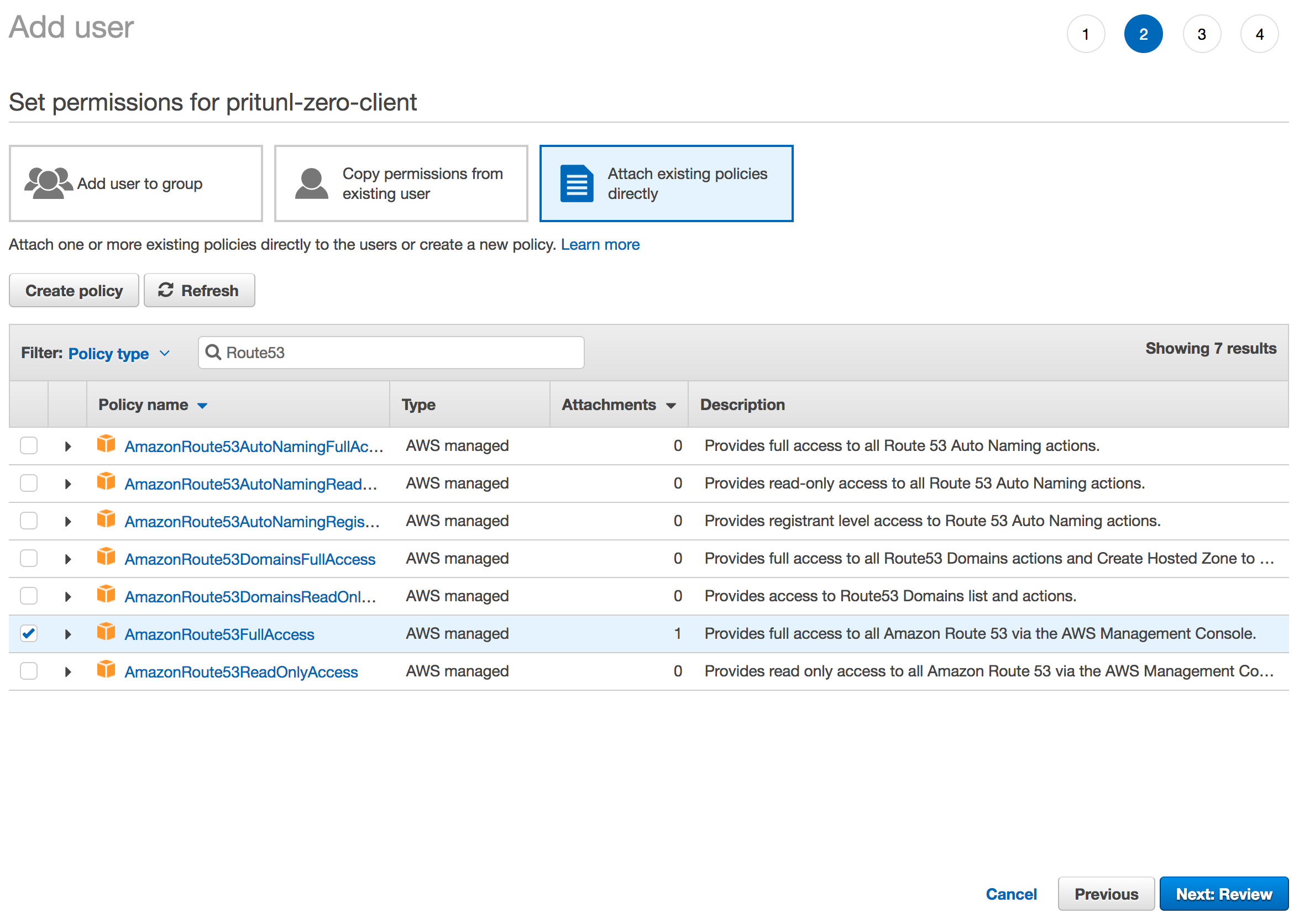
Host Domain
The OpenSSH client requires a host configuration to declare which servers are verified with host certificates and accessed through a bastion host. This is done with Pritunl Zero using a wildcard on the domain such as *.ssh.pritunl.com. This will direct any connections to servers in the ssh.pritunl.com domain to be verified with the certificate authority and tunneled through the bastion host.
Strict Host Checking
It is recommended to also enable strict host checking when using a bastion host as DNS entries will already be required and strict host checking will only slightly increase the complexity of the deployment while significantly improving security. Strict host checking is done with SSH host certificates. These certificates are essentially the same concept as certificates used to verify HTTPS connections in the web browser. It allows the SSH server to prove to the client that the server has a valid certificate for the domain the client is connecting to and that the connection between the client and the server is secure. This prevents clients from unknowingly connecting to rogue SSH servers that do not belong to the company and man-in-the-middle attacks.
Host Certificates
Pritunl Zero provisions host certificates similar to LetsEncrypt. The Pritunl Zero SSH host client requests a certificate from the Pritunl Zero server and starts a web server on port 9748. The Pritunl Zero server then makes a request to the domain on port 9748 to verify the server owns domain. After verifying ownership of the domain the Pritunl Zero server provisions a certificate to the host.
Configure Host Domain
A host domain must be configured in the authority settings from the Pritunl Zero web console. All servers must have a DNS entry for a subdomain of the host domain. Different authorities can't use the same host domain. No changes need to made to the domain DNS configuration for the host domain. In this example prod.pritunl.net will be used, all servers will be in the *.prod.pritunl.net domain.
Configure Route53 Access
If automatic Route53 configuration is going to be used either an instance role or access key needs to be created. If the servers are on the same AWS account an EC2 role is recommended. For servers on other cloud providers access keys will need to be used.
Route53 Instance Role
Open the IAM Management Console in the AWS console and click Create role in the Roles section. Select AWS service and EC2 then click Next: Permissions.
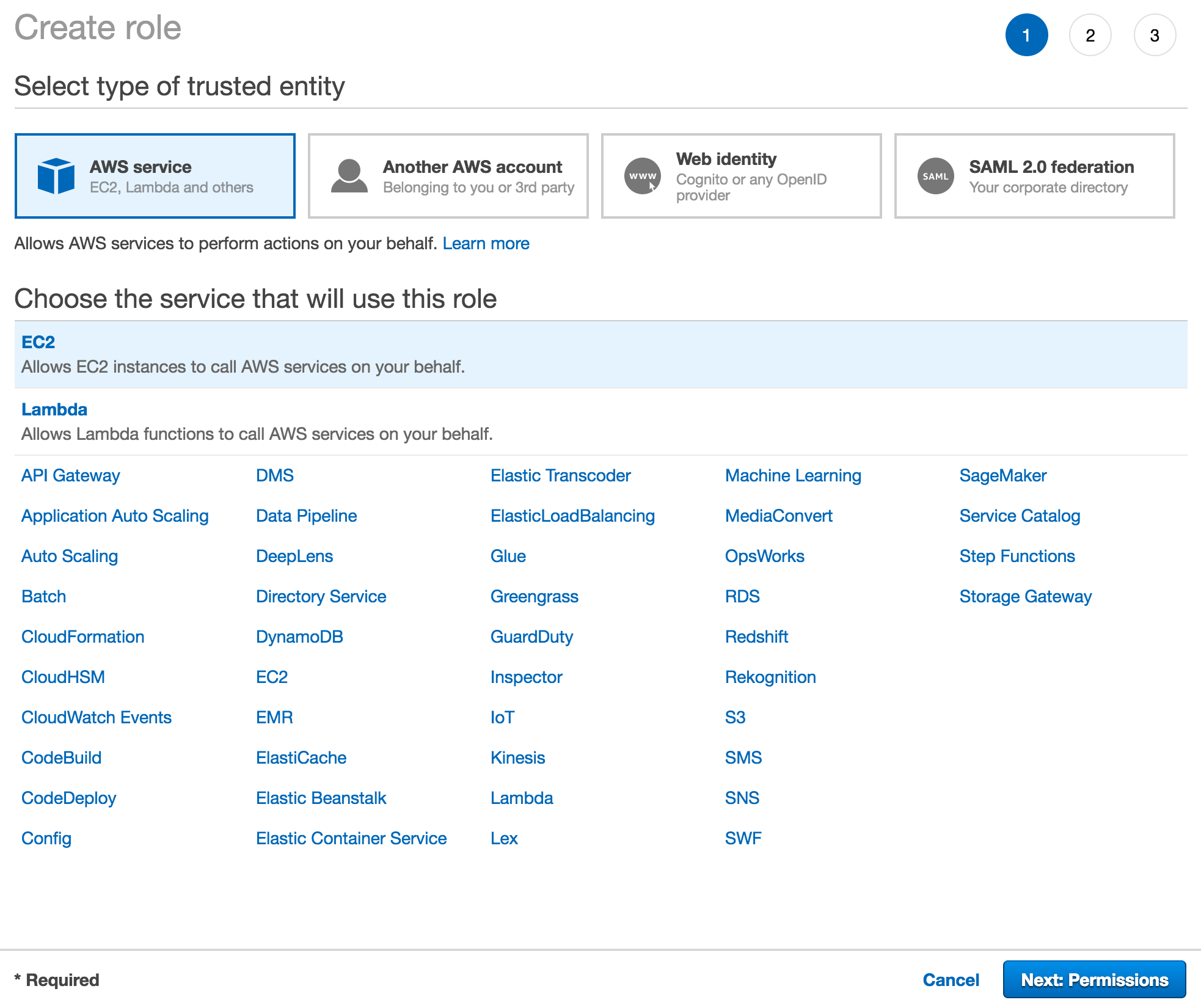
Search for Route53 and select AmazonRoute53FullAccess then click Next: Review.
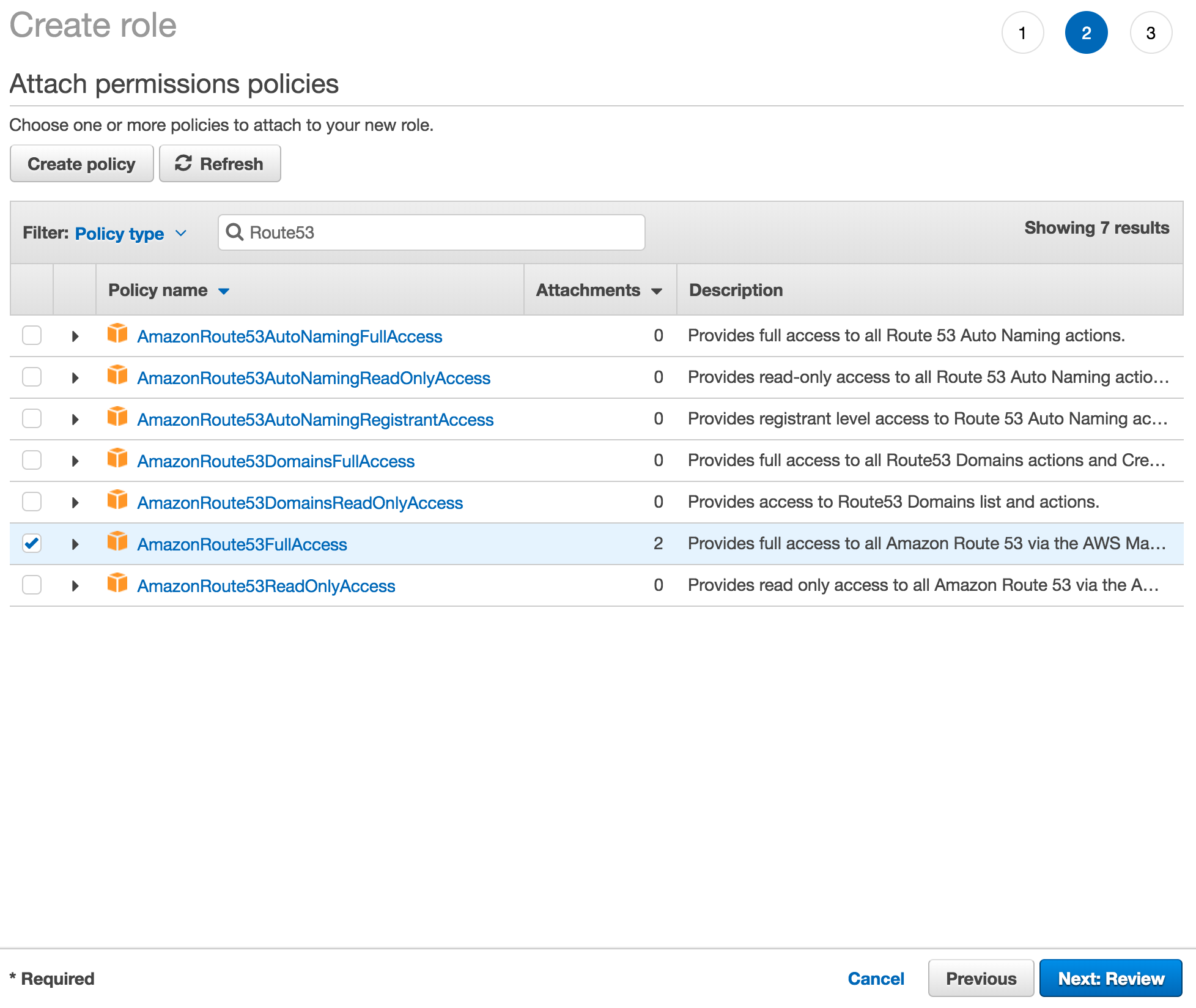
Set the Role name to pritunl-zero-client and click Create role.
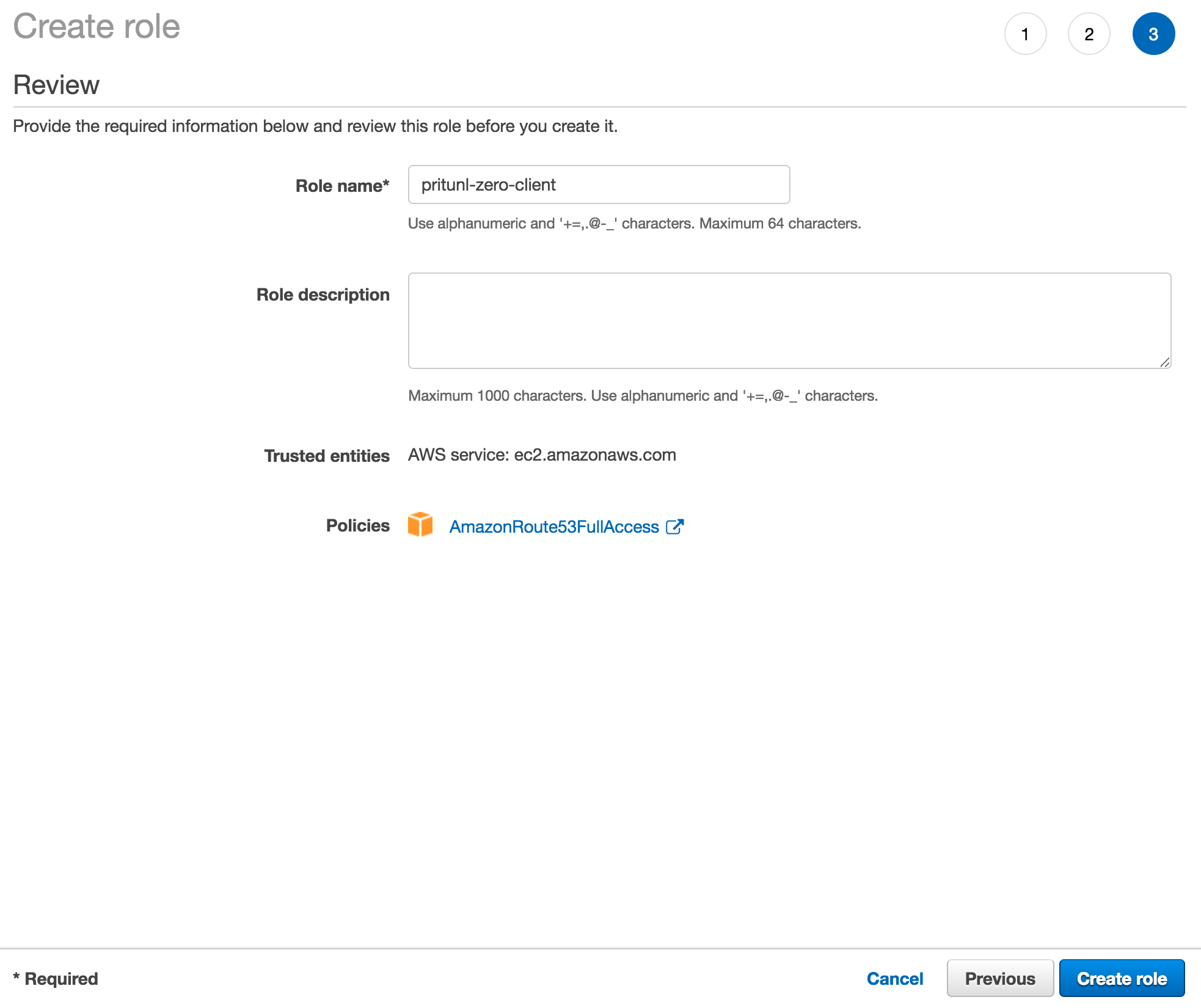
Route53 Access Key
Open the IAM Management Console in the AWS console and click Add user in the Users section. Set the Role name to pritunl-zero-client and select Programmatic access. Then click Next: Permissions.
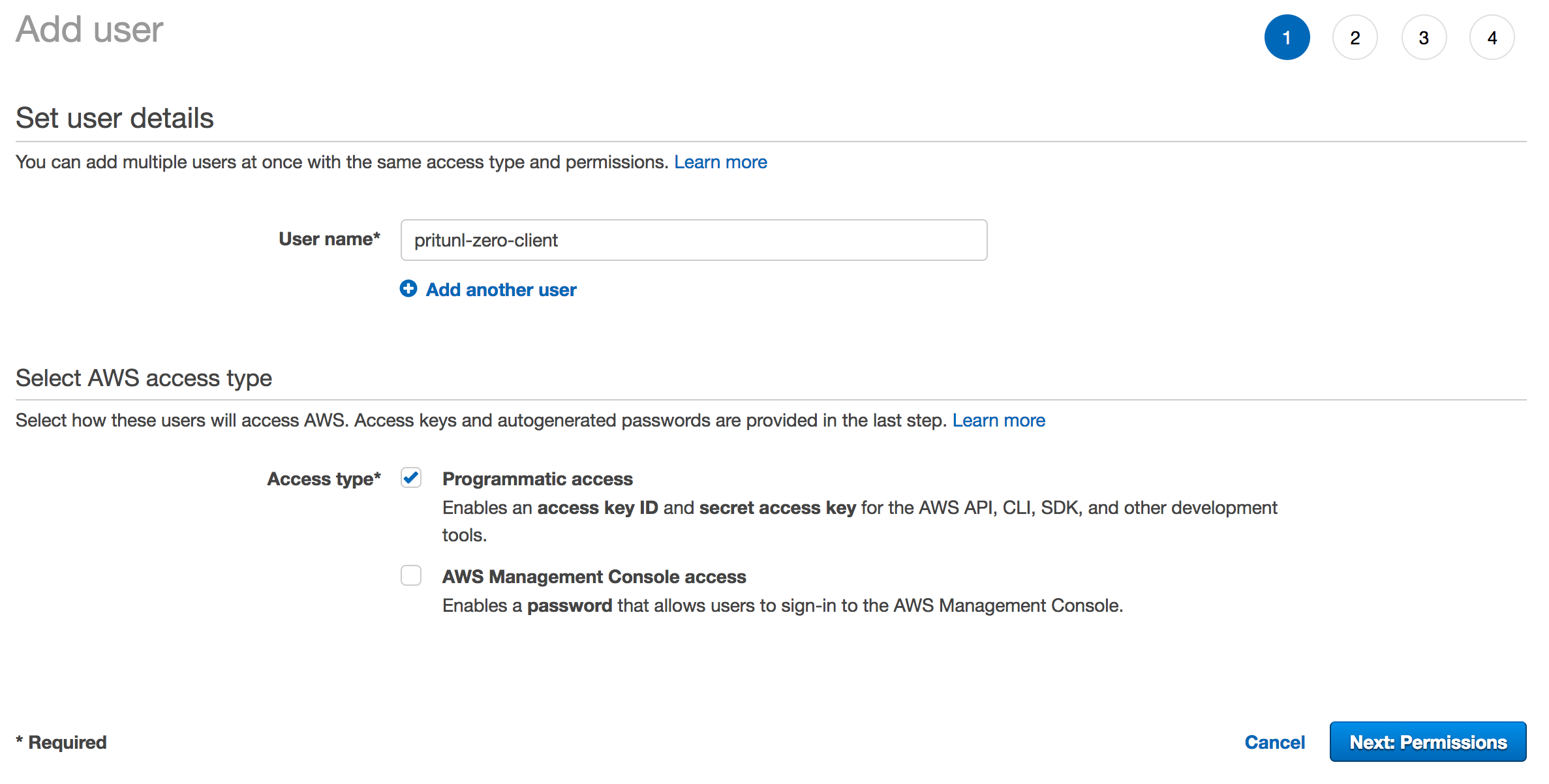
Select Attach existing policies directly and search for Route53. Then select AmazonRoute53FullAccess and click Next: Review.
Deploy Bastion Host (Optional)
To deploy the bastion host first set the Bastion Host in the authority settings. The bastion host must have be a subdomain of the Host Domain, set the username to bastion. If using the generate bastion deploy script the user will be created automatically and should not be a username that already exists. In this example bastion@bastion.prod.pritunl.net is used.
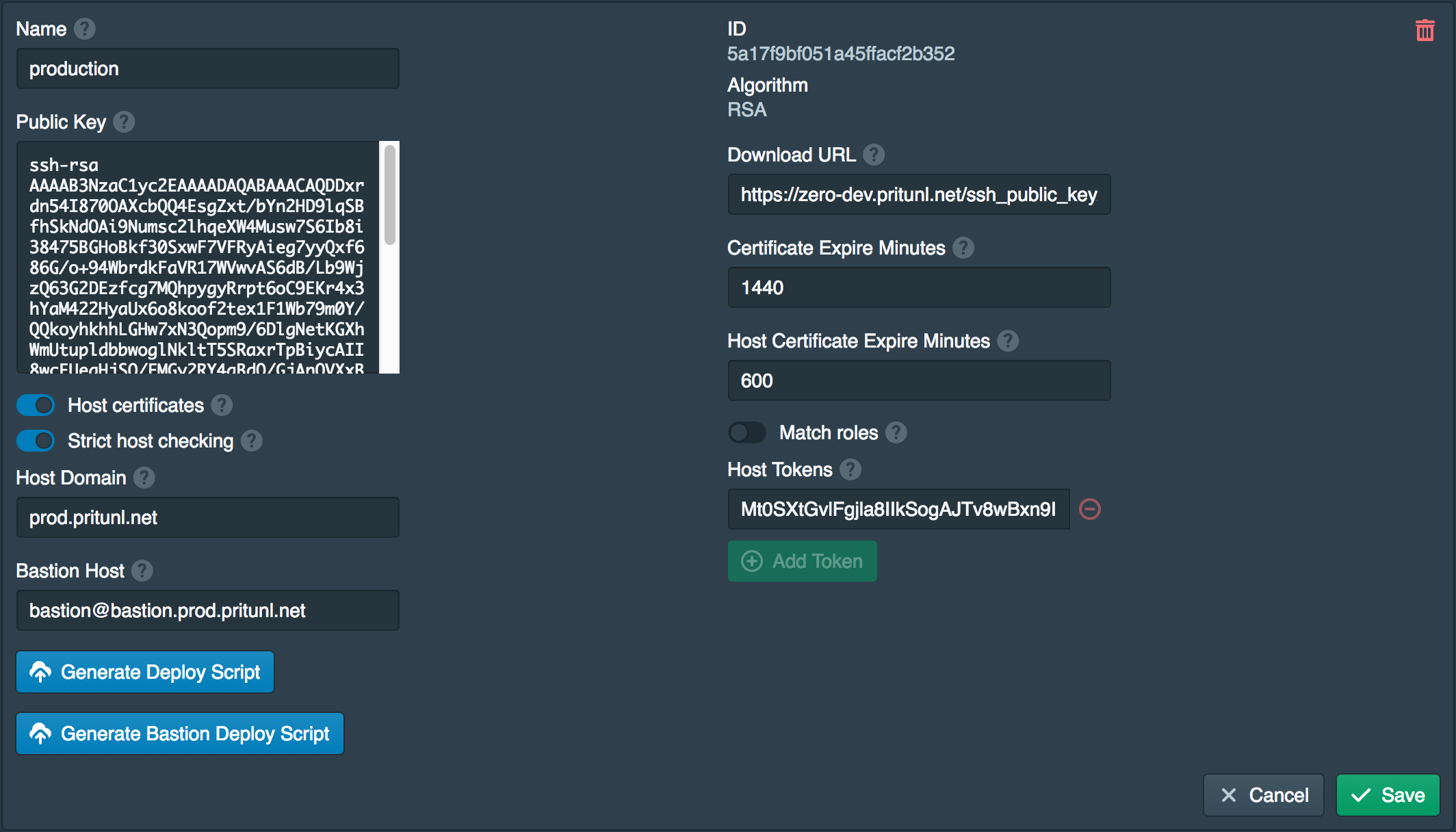
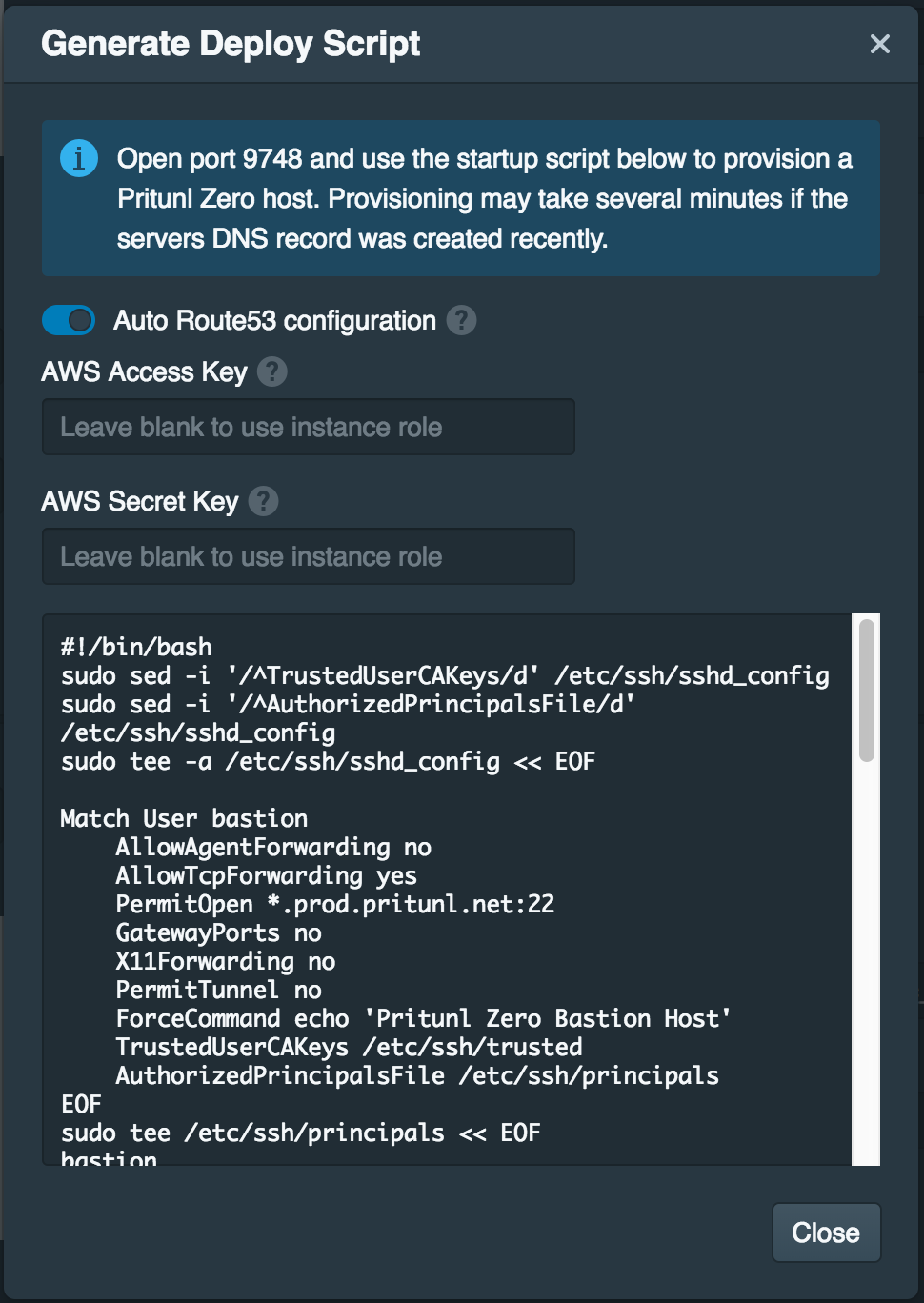
Once the bastion host is set click Generate Bastion Deploy Script and enable Auto Route53 configuration. Then copy the script to the user data or startup script when deploying the instance. The Pritunl Zero server must have access to TCP port 9748 on the instance to validate the certificate.
Private Subnet
If you are using a bastion host to access servers in a private subnet that does not have public addresses for the instances you will need to either not use host certificates or manually set the IP address of the host in the deploy script. This can be done with the command sudo pritunl-ssh-host public-address 12.34.56.78. This will set the Route53 entry to the private address of the host. The Pritunl Zero server must have access to TCP port 9748 on the private address to validate the certificate.
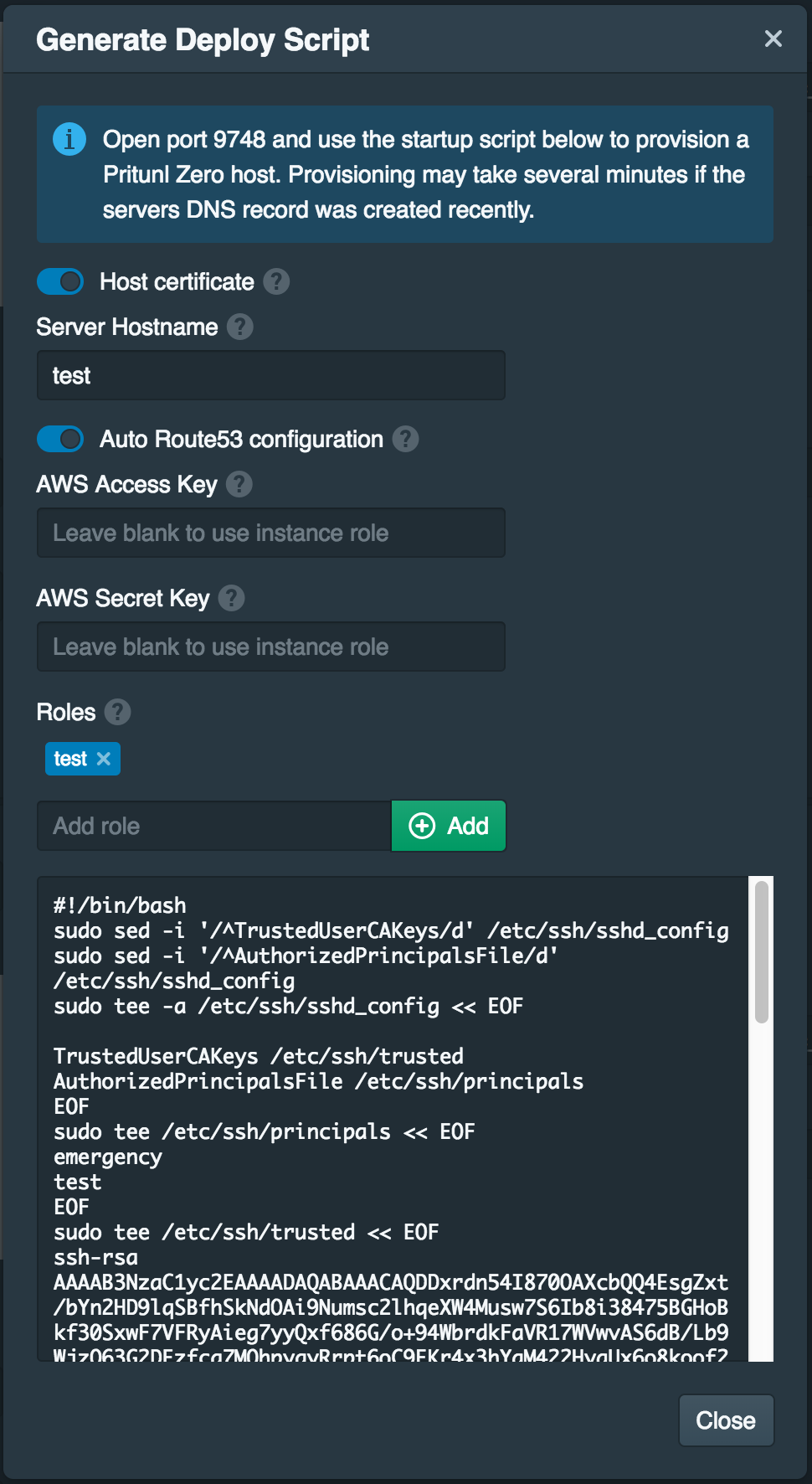
Deploy Host
When deploying hosts set the Server Hostname and enable Auto Route53 configuration. Configure the firewall to only allow access from the bastion server. If using a bastion host configure the firewall of the host to only allow access from the bastion host IP address. The Pritunl Zero server must have access to TCP port 9748 on the instance to validate the certificate.
Updated 4 months ago
