WireGuard Beta
Configure WireGuard beta
This beta is still untested and in development, it should not be used in production. Email any issues to contact@pritunl.com When reporting issues send all logs from the client.
Support for WireGuard will have the same features as an OpenVPN connection, this includes:
- Client automatic failover (approximately 13 seconds after server failure)
- Replicated servers
- Client to client traffic across replicated servers
- Static client IP addresses
- NAT and non-NAT routing configurations
- All secondary authentication methods
- Client port forwarding
- Client DNS mapping
- Client DNS management
- Routed client network links also know as an iroute
- IPv6 support
- Client access to linked servers (site-to-site link connections will continue to use OpenVPN)
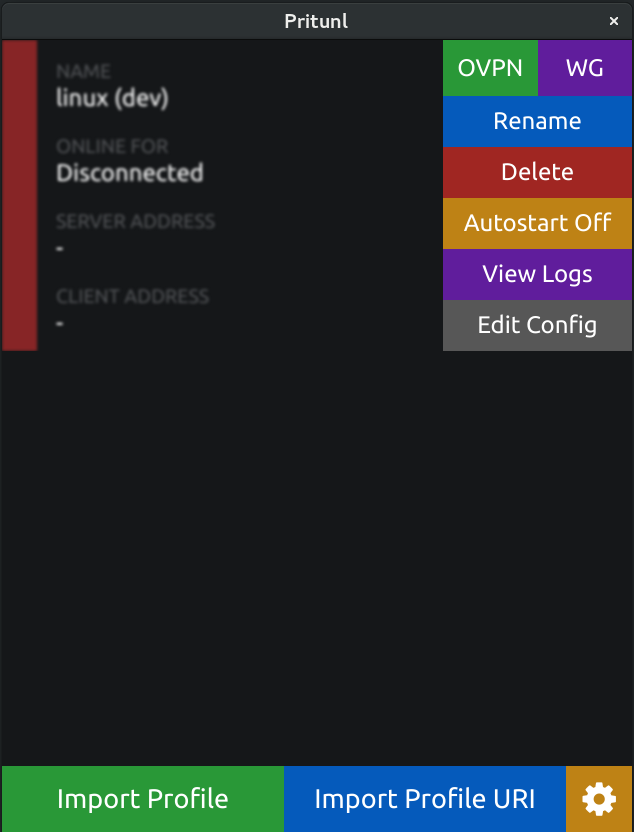
Client Implementation
The experience for the users will remain the same when connecting. If the server has WireGuard enabled and the required packages are installed on the client a button will be shown for the user to select OVPN or WG when connecting. If the WG button is not shown the WireGuard binaries were not found on the computer.
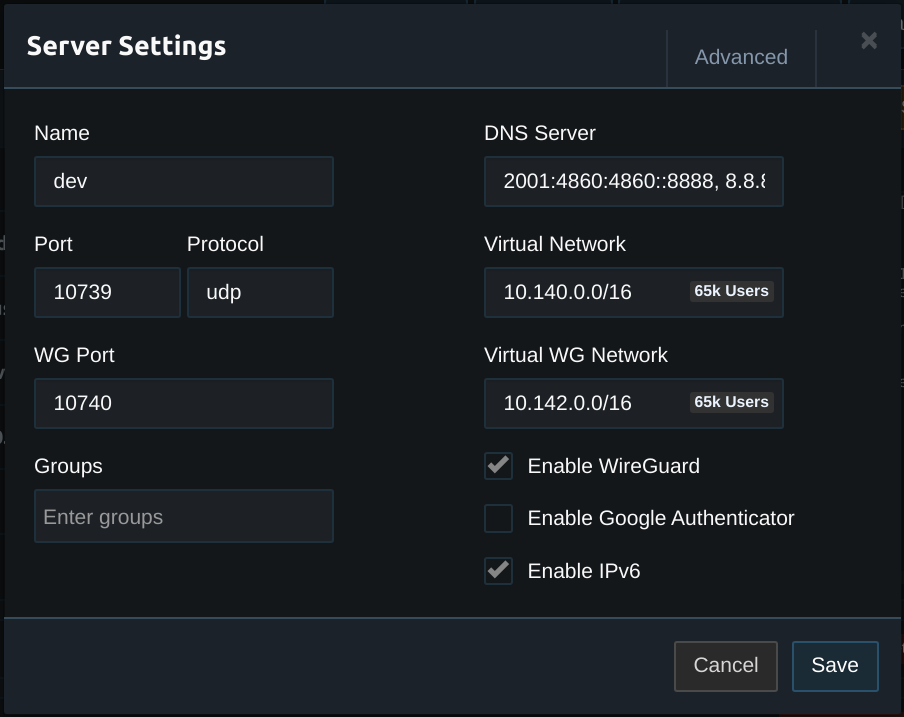
Server Configuration
To install the Pritunl server beta replace the stable path with dev in the repository URL as shown below. Current repository files can be modified to updated an existing installation.
sudo tee /etc/yum.repos.d/mongodb-org-4.2.repo << EOF
[mongodb-org-4.2]
name=MongoDB Repository
baseurl=https://repo.mongodb.org/yum/redhat/7/mongodb-org/4.2/x86_64/
gpgcheck=1
enabled=1
gpgkey=https://www.mongodb.org/static/pgp/server-4.2.asc
EOF
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/dev/yum/oraclelinux/7/
gpgcheck=1
enabled=1
EOF
sudo yum -y install oracle-epel-release-el7
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp; sudo rpm --import key.tmp; rm -f key.tmp
sudo yum -y install pritunl mongodb-org kernel-devel kernel-uek-devel
sudo systemctl start mongod pritunl
sudo systemctl enable mongod pritunlsudo tee /etc/yum.repos.d/mongodb-org-4.2.repo << EOF
[mongodb-org-4.2]
name=MongoDB Repository
baseurl=https://repo.mongodb.org/yum/redhat/7/mongodb-org/4.2/x86_64/
gpgcheck=1
enabled=1
gpgkey=https://www.mongodb.org/static/pgp/server-4.2.asc
EOF
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/dev/yum/centos/7/
gpgcheck=1
enabled=1
EOF
sudo rpm -Uvh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp; sudo rpm --import key.tmp; rm -f key.tmp
sudo yum -y install pritunl mongodb-org kernel-devel
sudo systemctl start mongod pritunl
sudo systemctl enable mongod pritunlWireGuard must be separately installed on the server. This can be done using the commands below. If sudo dkms status does not show the module with the current kernel version restart the server and run sudo dkms autoinstall.
sudo curl -o /etc/yum.repos.d/jdoss-wireguard-epel-7.repo https://copr.fedorainfracloud.org/coprs/jdoss/wireguard/repo/epel-7/jdoss-wireguard-epel-7.repo
sudo yum -y install wireguard-dkms wireguard-tools
sudo dkms autoinstall
sudo dkms status
sudo rebootThe DKMS status command should show the module along with the current kernel version. Once installed enable WireGuard in the server settings, set the WG Port and set the Virtual WG Network to a subnet with the same CIDR as the Virtual Network.
Linux Client
To install the Pritunl Client beta replace the stable path with dev in the repository URL as shown below. Only the pritunl-client-electron package is supported.
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/dev/yum/oraclelinux/7/
gpgcheck=1
enabled=1
EOF
sudo yum -y install yum-utils
sudo yum-config-manager --enable ol7_developer_epel
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp; sudo rpm --import key.tmp; rm -f key.tmp
sudo yum -y install pritunl-client-electronWireGuard must be separately installed on the client. The wireguard-tools and wireguard-dkms packages are required.
macOS Client
Due to limitations with the macOS hardened runtime system there is no plans to support WireGuard in the packaged client version. It can be installed from source to support WireGuard connections.
The Homebrew package wireguard-tools must be separately installed.
Windows Client
Download and install the Windows Beta Client
The WireGuard Windows package must be installed separately.
Client Configuration
If client configuration sync is available the client will not need to redownload the VPN profile. The client must have access to the Pritunl HTTPS server. This will be used authenticate the connection.
Updated 3 months ago
