AWS Route Advertisement
Route advertisement on AWS
This tutorial will describe configuring VPN access to a VPC without using NAT. This is useful for when security group rules are needed to control VPN users access to resources on the VPC. This example will use a server with two hosts attached. In the event that one host fails the VPC routing table will automatically be updated with the other host.
If replication is also used the VXLan option must be enabled and security groups should be configured to allow UDP port 4789 between Pritunl hosts.
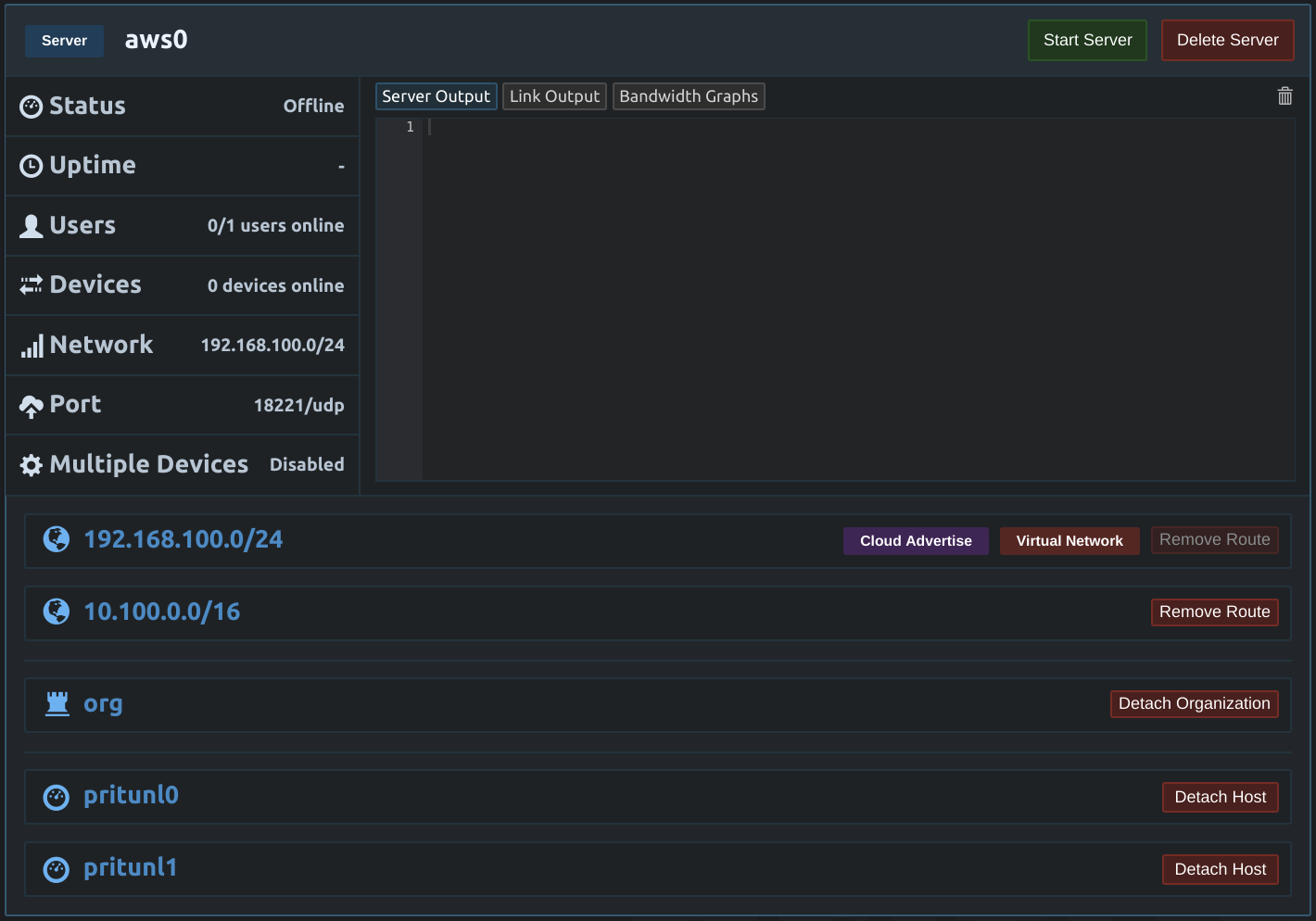
First create a IAM Instance Role with full VPC access. This is needed to allow the Pritunl Link client to modify the VPC routing table.
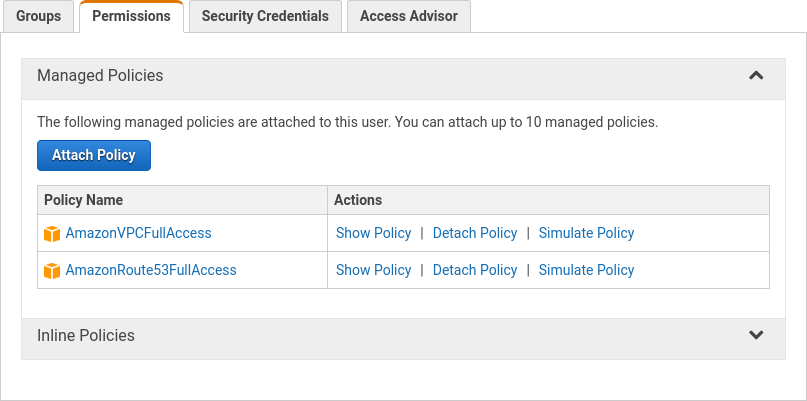
When launching the instance select IAM role created earlier.
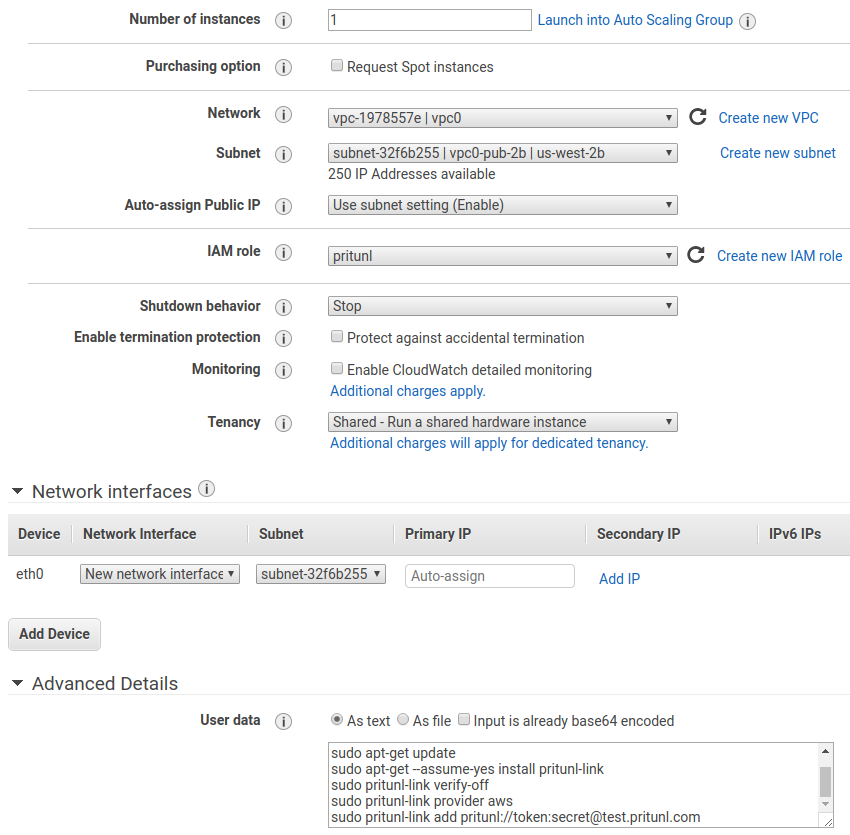
Once done copy the set the Cloud Provider to AWS in the settings. Then enter role for the access and secret key for the instance region. This will instruct Pritunl to load the AWS key from the instance IAM role.
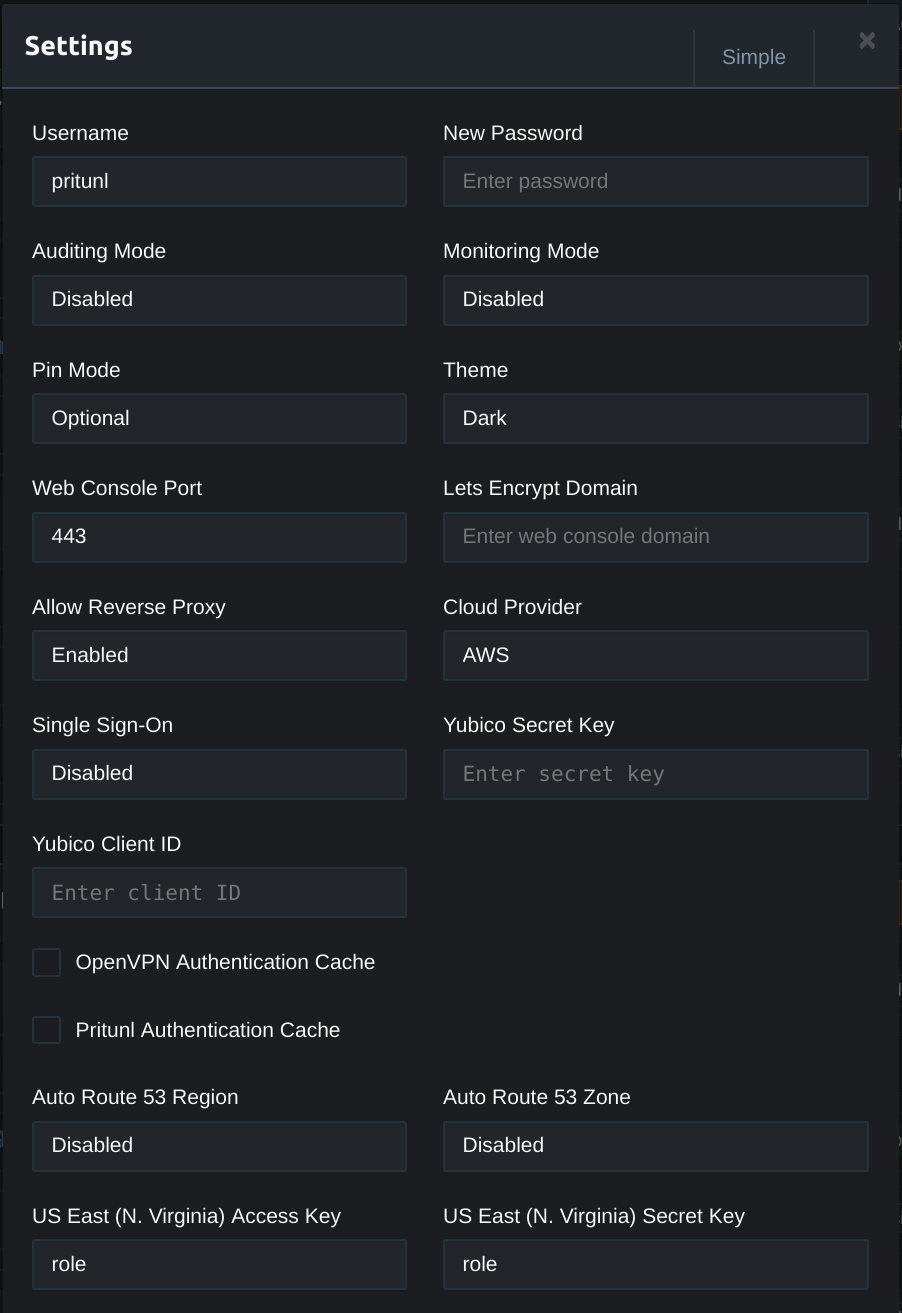
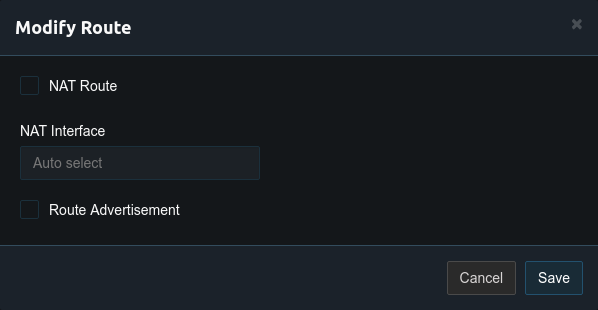
Next open the Pritunl route settings for the VPC network. In this example this is the 10.100.0.0/16 network. In the route settings uncheck NAT Route. Although the route will be advertised to this VPC network route advertisement should not be enabled for this route as the 10.100.0.0/16 network will already exists in the VPC routing table. Generally only the Virtual Network route will be advertised unless the Pritunl server is providing access to other networks such as in site-to-site configurations.
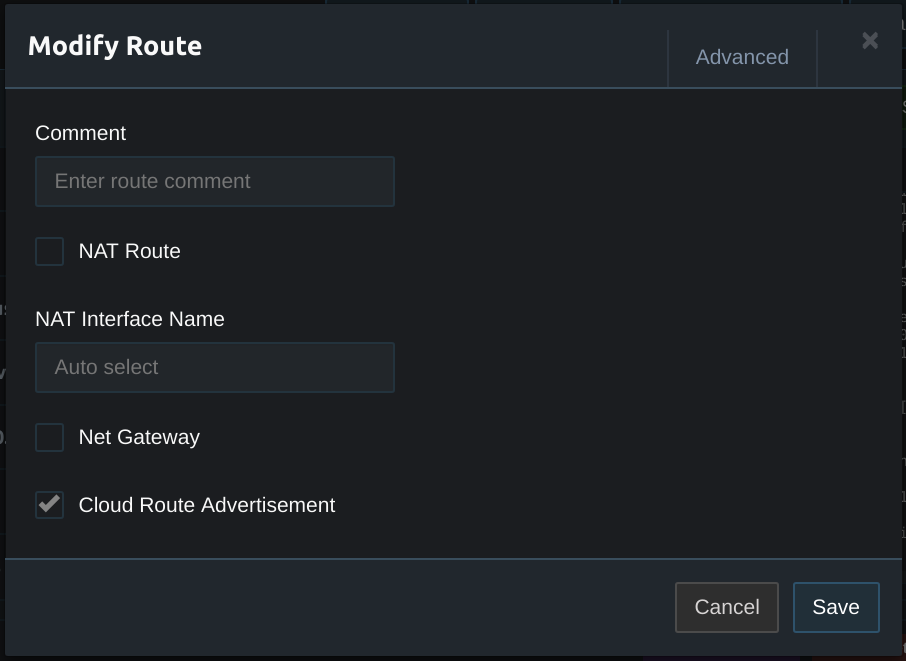
Next open the route settings for the virtual network. This will be the first network listed in the routes section and will have a Virtual Network label on the right side. Select Cloud Route Advertisement. This will add a route for the Pritunl host to the VPC routing table. With the route in the routing table servers on the VPC network will have a route to reach the Pritunl clients allowing for clients to access the VPC without NAT.
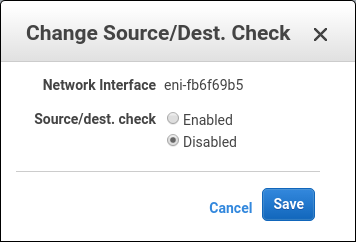
Before the EC2 instance can route traffic to the virtual network the source/dest check must be disabled. This can be found in the network interfaces section of the EC2 dashboard. This must be done to any network interfaces attached to Pritunl EC2 instances. This will allow the EC2 instance to route traffic to other networks such as the virtual network for the vpn server.
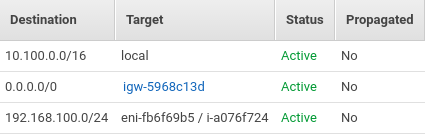
Once the route has been configured the server can be started. Once running an additional route should appear in the routing table for the VPC. The destination for the route should match the virtual network on the vpn server and the target should be the EC2 instance ID that is running the Pritunl server. The VPC routing table can be found in the AWS management console in the VPC section.
To allow vpn clients to access resources in the VPC it will be necessary to modify the security groups in the VPC to allow traffic from the Pritunl virtual network.
Updated over 6 years ago
